User
Intelligence is a medium rated machine on HackTheBox by Micah. For the user part we will find default credentials through an IDOR vulnerability on a website hosting PDF’s. This will give us access to a smb share where we find a powershell script being run every 5 minutes. We can abuse this scheduled task and capture the hash for another user with responder after adding a DNS entry. After cracking the hash we can retrieve the NTLM hash for a service account over gMSA. With this credentials we can now abuse the constrained delegtion over our target, impersonate the administrator user and psexec into the machine.
Nmap
As always we start our enumeration off with an nmap scan against all ports, followed by a script and version detection scan against the open ones.
Allports
1 | |
Script and version
1 | |
PDF IDOR
The open ports and the dns name hint on this machine being a domain controller. Port 80 being open on a DC is unusual and might bring some quick success, so we will start there. Going over to the page we see an almost completely static website with most things filled from a default template.
The only thing not looking fully default is the download functionality, where we can download 2 PDF’s.
The PDF’s seem to be structured in the format <year>-<month>-<day>-upload.pdf, if there are no additional checks on the website we might be able to access different PDF’s, which aren’t supposed to be public.
For this we create our wordlist first with a short python script.
1 | |
1 | |
We use this wordlist with ffuf to fuzz for alternative dates/PDF names and get indeed a lot of hits. To download all the files in the next step we export the ffuf output as CSV.
1 | |
Using this CSV we can now use wget on all the PDF’s in ffuf’s output to dump them.
1 | |
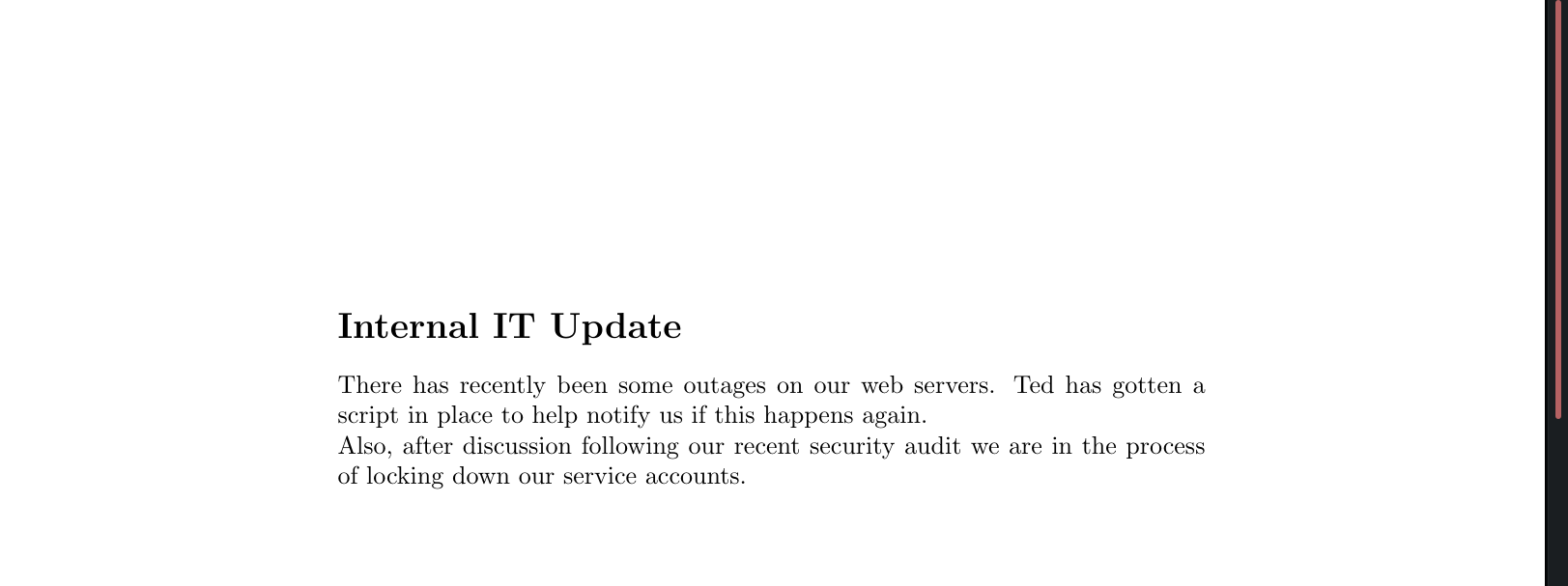
Looking through the files we see 2 particularily interesting ones. 2020-12-30-upload.pdf is stating that there is a script running to check web server connectivity and that they are planning to disable their service accounts due to a security risk they pose.
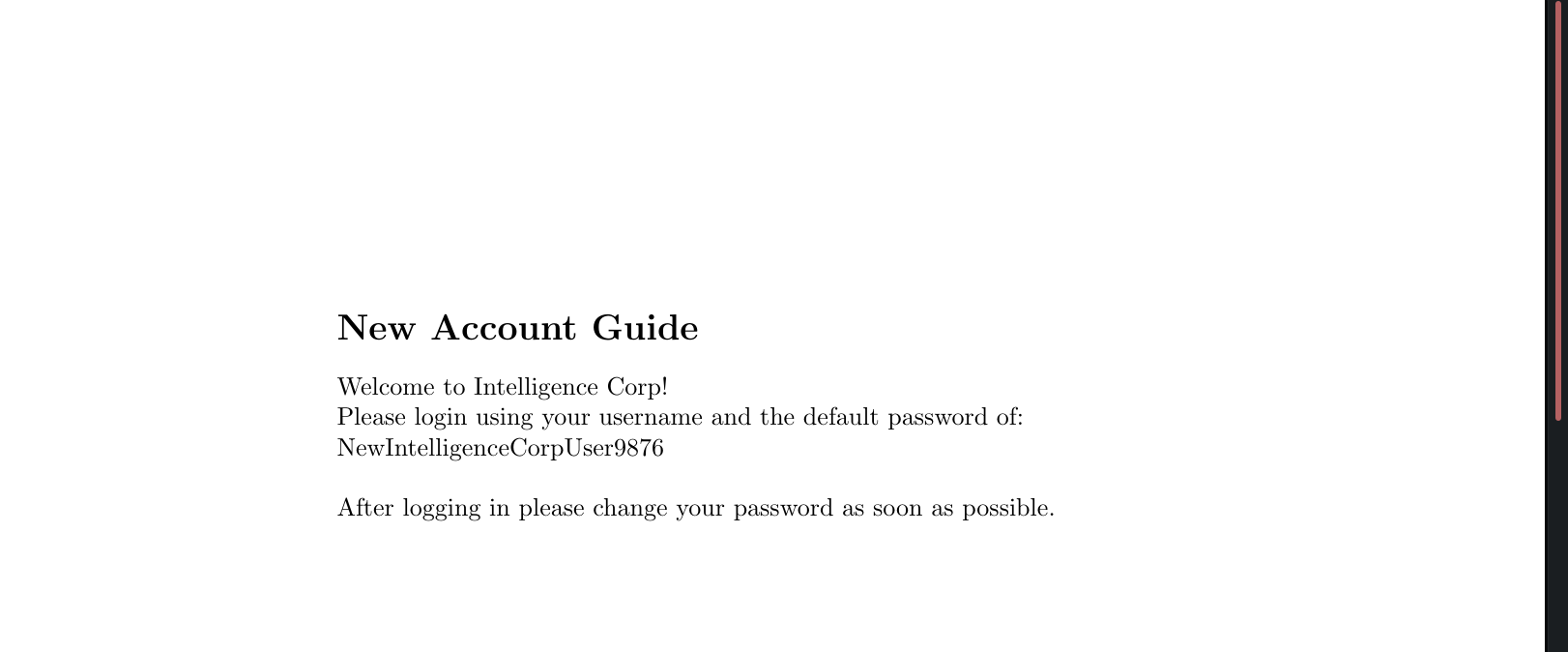
2020-06-04-upload.pdf gives even better information for now. It leaves us with a default password, meaning if we get a list of username we might be lucky and a user did not change his password.
Looking at the PDF’s with exiftool we see the Creator field seems to contain possible usernames.
1 | |
We can extract all of the usernames with a bash one liner for further work.
1 | |
SMB
Using crackmapexec to check the password for every user we see it is valid for Tiffany.Molina and she has access to the Users and IT share.
1 | |
1 | |
To go through the files quicker and with more tools available we turn on recursive mode in smbclient, turn off the prompt an download all files.
1 | |
Going through the retrieved data we can grab the user flag.
1 | |
Root
Scheduled Task
In hte IT share we see the earlier mentioned powershell script.
1 | |
The script checks all DNS records for ones that starts with web and uses Invoke-WebRequest with default credentials on them. If the server does not respond it sends an email to ted stating the host is down. If we can add a DNS entry for our ip address starting with web we can possibly exfiltrate the hash with responder.
1 | |
For this we use dnstool.py with the credentials for Tiffany and add our dns entry.
1 | |
We quickly set up responder to listen and wait. After a maximum of 5 minutes Ted.Graves connect’s to us and presents us his hash for the challenge.
1 | |
Using hashcat the hash cracks quite quickly leaving us with the password Mr.Teddy for Ted.Graves.
1 | |
We still cannot login to the machine as Ted.Graves so we check if we might be able to escalate to another user as him using bloodhound.
1 | |
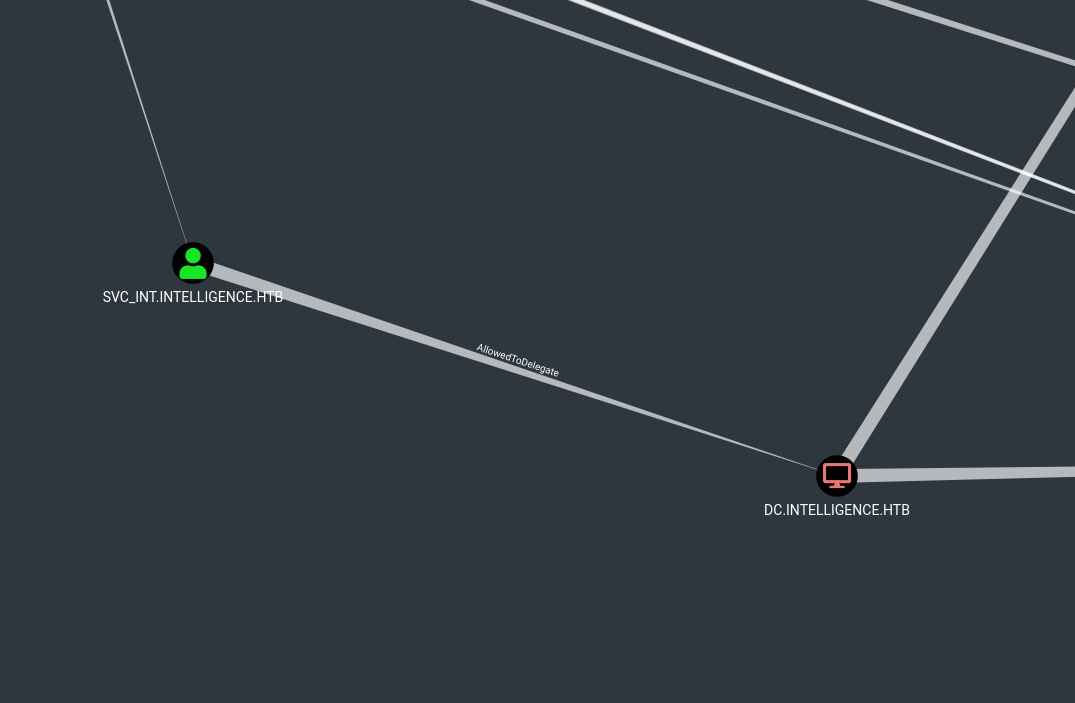
Bloodhound shows an interesting edge for the earlier mentioned service account. If we manage to get to svc_int we can escalate to domain administrator in the next step abusing constrained delegation on the domain controller.
gMSA
One possible way to get to a service can be gMSA. Looking in the author’s github we see he has even realeased a tool for remotely dumping the gMSA password for a service account.
Using this tool as Ted.Graves on svc_int we can indeed retrieve the password hash for the account.
1 | |
Constrained delegation
Now we can abuse the earlier seen constrained delegation. Since we are using kerberos for this we have to first fix the time on our vm by syncing it with the dc.
1 | |
Then we can create a service ticket with the spn www/dc.intelligence.htb impersonating the domain administrator.
1 | |
We export the ticket to our KRB5CCNAME environment variable to use it in the next step.
1 | |
Since impacket automatically converts the requested www ticket to a needed host ticket, we can now simply psexec into the machine and grab the root flag.
1 | |