Armageddon is an easy rated machine on HackTheBox created by bertolis. For the user part we will abuse CVE-2018-7600 aka Drupalgeddon2. After gaining a foothold we will find the database credentials from drupal’s settings.php file. Cracking the hash in the database we can ssh in as the user brucetherealadmin. Bruce is allowed to install any snap package with root permissions, which gives us an easy root modifying the dirty_socks exploit.
User
Nmap
As usual we start our enumeration of with a nmap scan against all ports, followed by a script and version detection scan against the open ones to get a full picture of the attack surface.
All ports
1 | |
Script and version
1 | |
Drupalgeddon
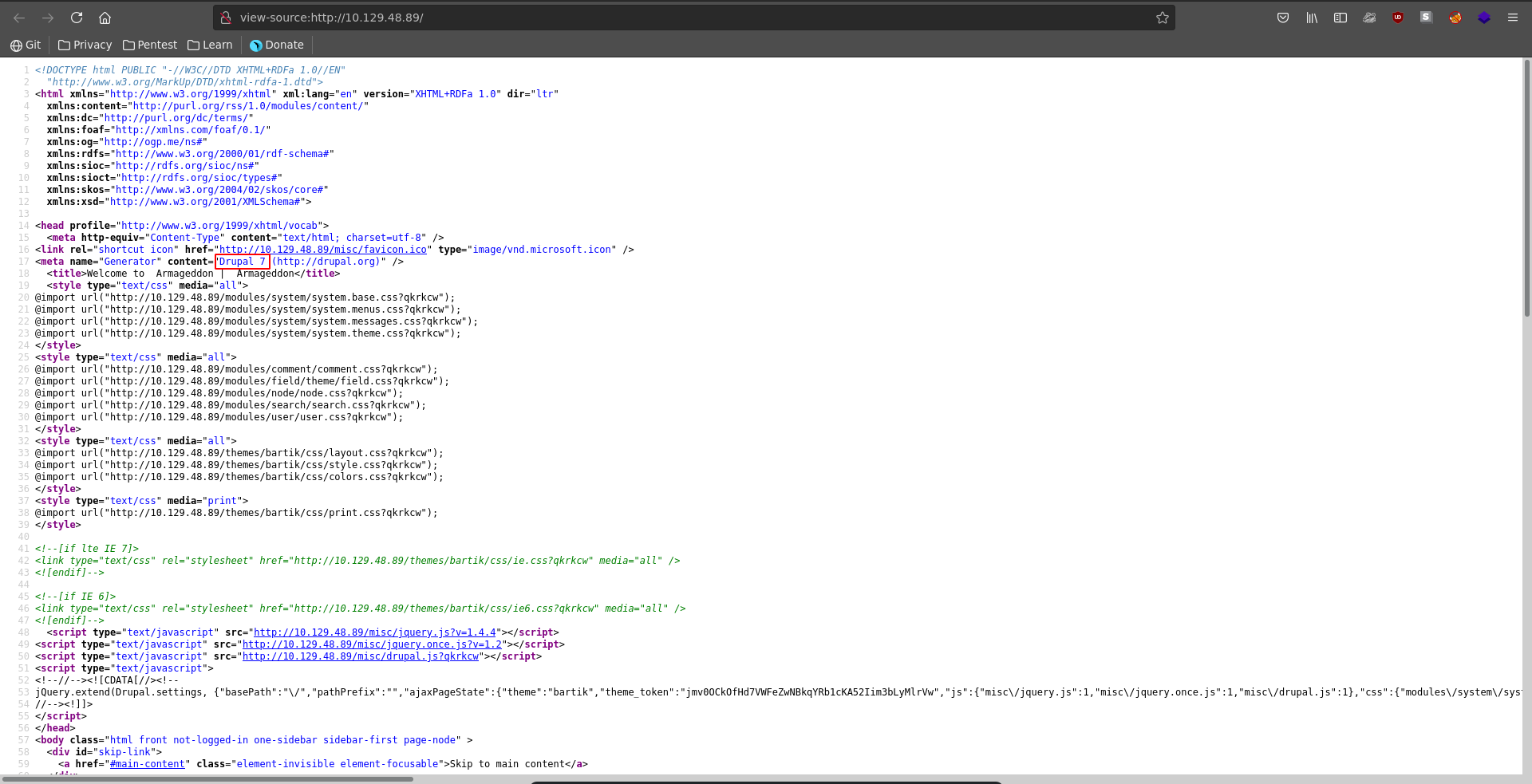
There are only two ports open on the target with http being a significantly larger attack surface than ssh, hence we will start there. Browsing to it in our browser we see a login interface where the source reveals it is running drupal 7.
This version of drupal is vulnerable to CVE-2018-7600 also called drupalgeddon2. There exists a msf module for this CVE which we will use out of simplicity. We set the port to one that is mostly allowed for outbound connections, set the lhost to our vpn ip, set the rhost to the target and run the exploit. After some time it returns in a meterpreter on the target.
1 | |
Database credentials
Drupal often stores the database credentials in a settings.php file which is also the case here.
1 | |
Since we can neither use python nor script, getting a real shell is hard. So we use the -e in mysql to get information from the database. Looking through the database as drupaluser we find the hashed password for brucetherealadmin using the drupal database in the users table.
1 | |
1 | |
1 | |
Hashcat cracks the hash quite quickly.
1 | |
After logging in as brucetherealadmin via SSH we can now grab the user flag.
1 | |
Root
Snap
Checking for sudo permission we see that we can run snap install on any snap package as root.
1 | |
Probably the easiest way to abuse this is by using the dirty_sockv2 exploit since it works by installing a malicious snap package aswell. For this we grab the base64 snap package from the source and decode it do our snap package.
1 | |
1 | |
Now we just have to transfer it to the target…
1 | |
… and install it with root permissions.
1 | |
This adds a user dirty_sock with the password dirty_sock to the machine which is allowed to run any command with sudo.
1 | |
After switching to the user and escalating to root with sudo su we can add the rootflag to our collection.
1 | |