Anubis is an insane rated machine on HackTheBox created by 4ndr34z. For the user part we will exploit a command injection in a contact form to get system in a docker container. There we discover another vhost in a CSR and see a webserver running on the host which we can forward to our machine. There we can abuse a install application, which let’s us capture a users NetNTLMv2 hash. Cracking the hash we have access to a smb share with multiple jamovi files. We are able to phish a user with XSS in the column name resulting in a reverse shell. To obtain system we will abuse the misconfigured access control of a certificate template. Changing the certificate usage to client authentication we can enroll the administrator user as alternative name and request a TGT for him.
User
Nmap
As usual we will start our enumeration off with a nmap scan against all ports, followed by a script and version detection scan against the open ones to get an initial overview of the attack surface.
All ports
1 |
|
Script and version
1 |
|
Command injection
The nmap scan reveals a dns name for the running webserver on port 443 so we add it to our /etc/hosts file. Browsing there we see the homepage of the windcorp company.
Going over to Contact we can submit a contact request which we intercept with burp and send it to repeater.
Testing for command injection we create a small payload and see if it get’s evaluated.
1 |
|
We put our payload in the message paramater, urlencode it and open the request in our browser.
After getting redirected we see our payload get evaluated proofing code execution.
The next step is to extend our payload to result in a reverse shell. For this we create VBscript payload downloading a netcat binary hosted by us and sending us a reverse shell with it.
1 |
|
We first stand up our webserver hosting the binary and set up our ncat listener.
1 |
|
1 |
|
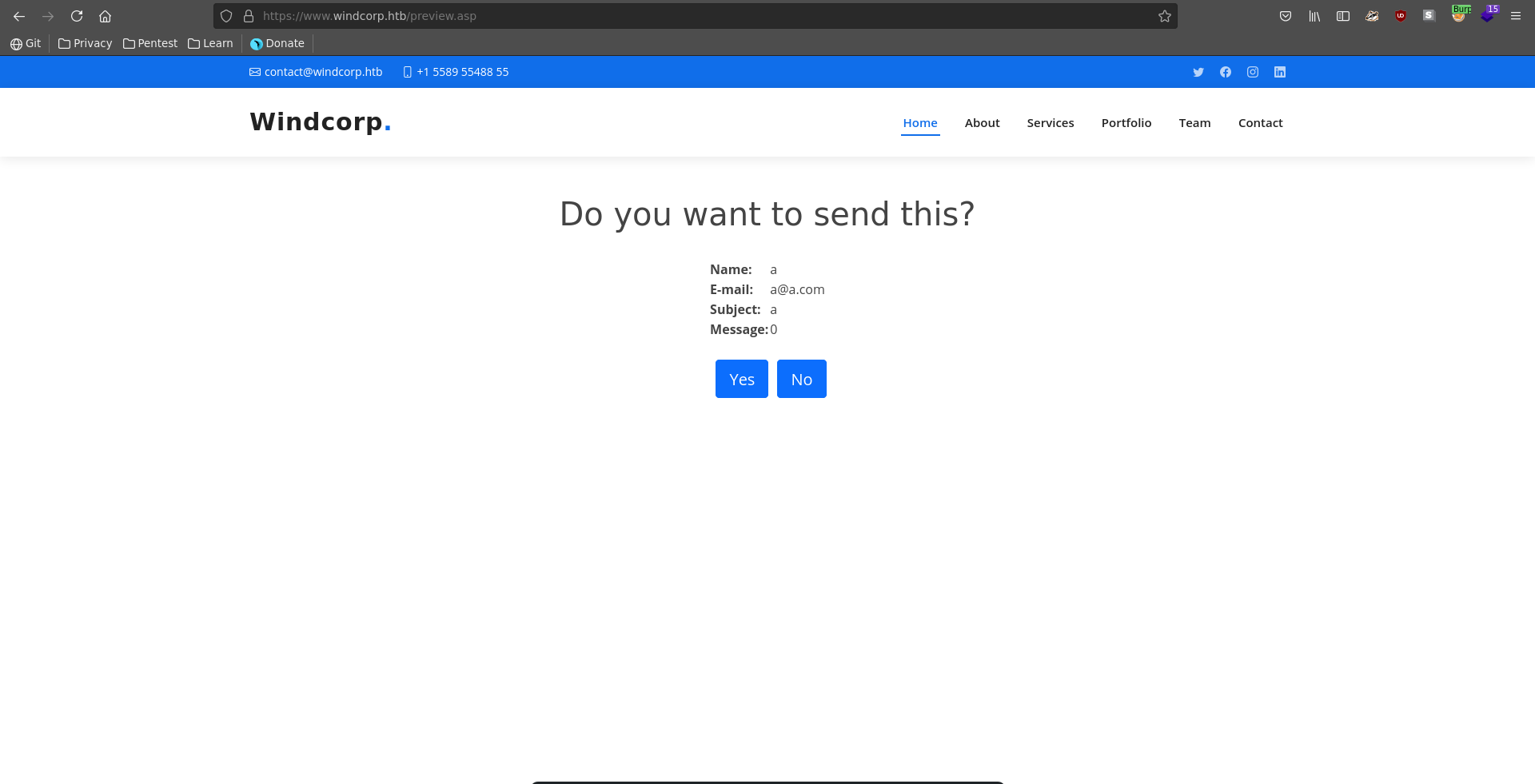
Then we repeat the same steps as before and open the request in our browser.
After clicking on yes we get a hit on our webserver to download nc.exe and a reverse shell on our listener as nt authority\system on what seems to be a docker container.
1 |
|
1 |
|
Softwareportal
Looking around on the file system we find a certificate signing request on the administrators desktop.
1 |
|
Taking a closer look at it with openssl we find another subdomain.
1 |
|
The subdomain doesn’t belong to the docker webserver so we need to find the host it belongs to. Checking ipconfig and the arptable we only find one additional host.
1 |
|
1 |
|
Testing for open common webserver ports on it http is open.
1 |
|
To reach it from our machine we have to forward it. For this we upload a chisel binary, start the chisel server on our local machine and run the client on the docker.
1 |
|
1 |
|
1 |
|
Seeing the session established we now need to add the entry 127.0.0.1 softwareportal.windcorp.htb to our /etc/hosts file.
1 |
|
Opening the page in our browser we see the WINDCORP - SOFTWARE PORTAL.
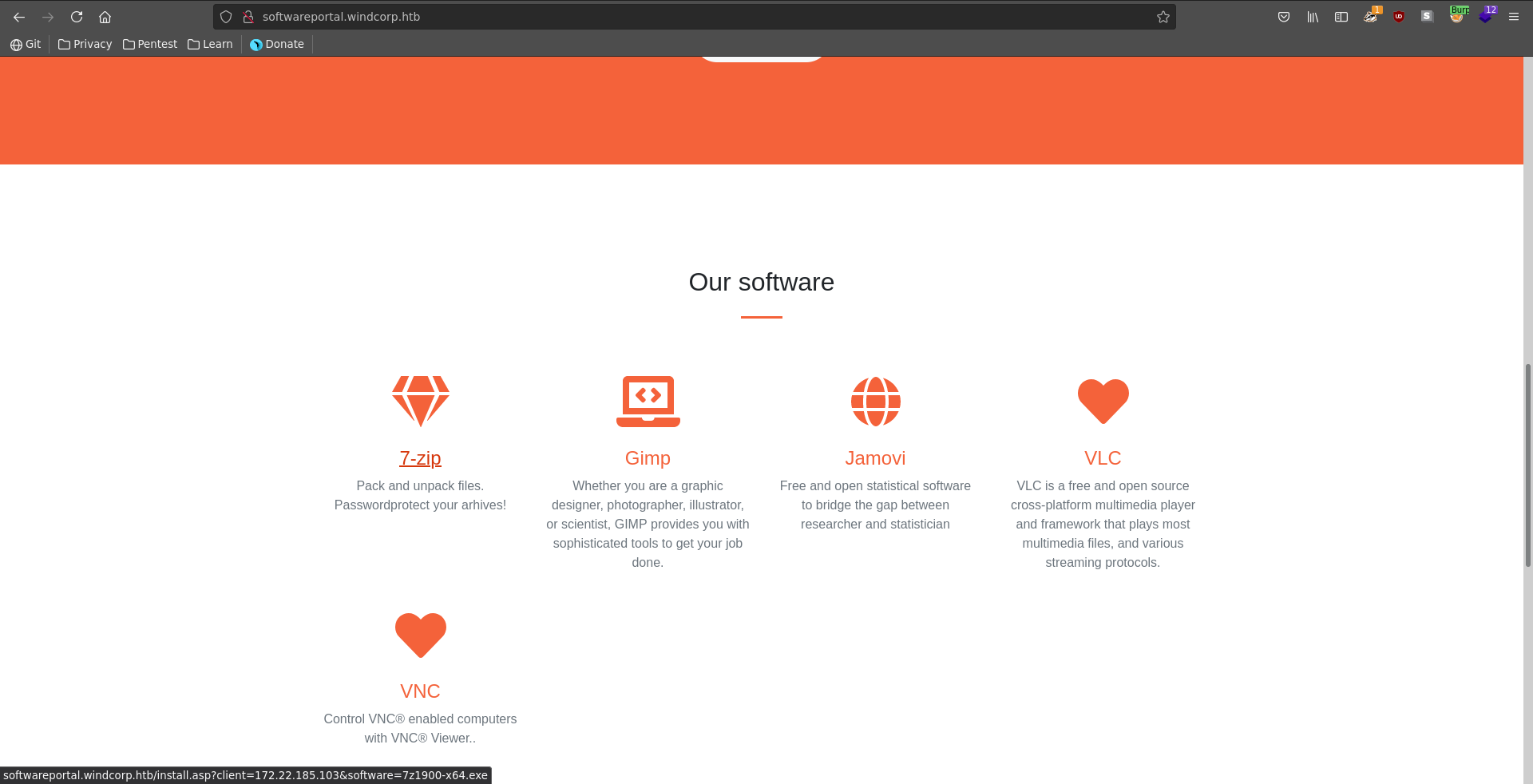
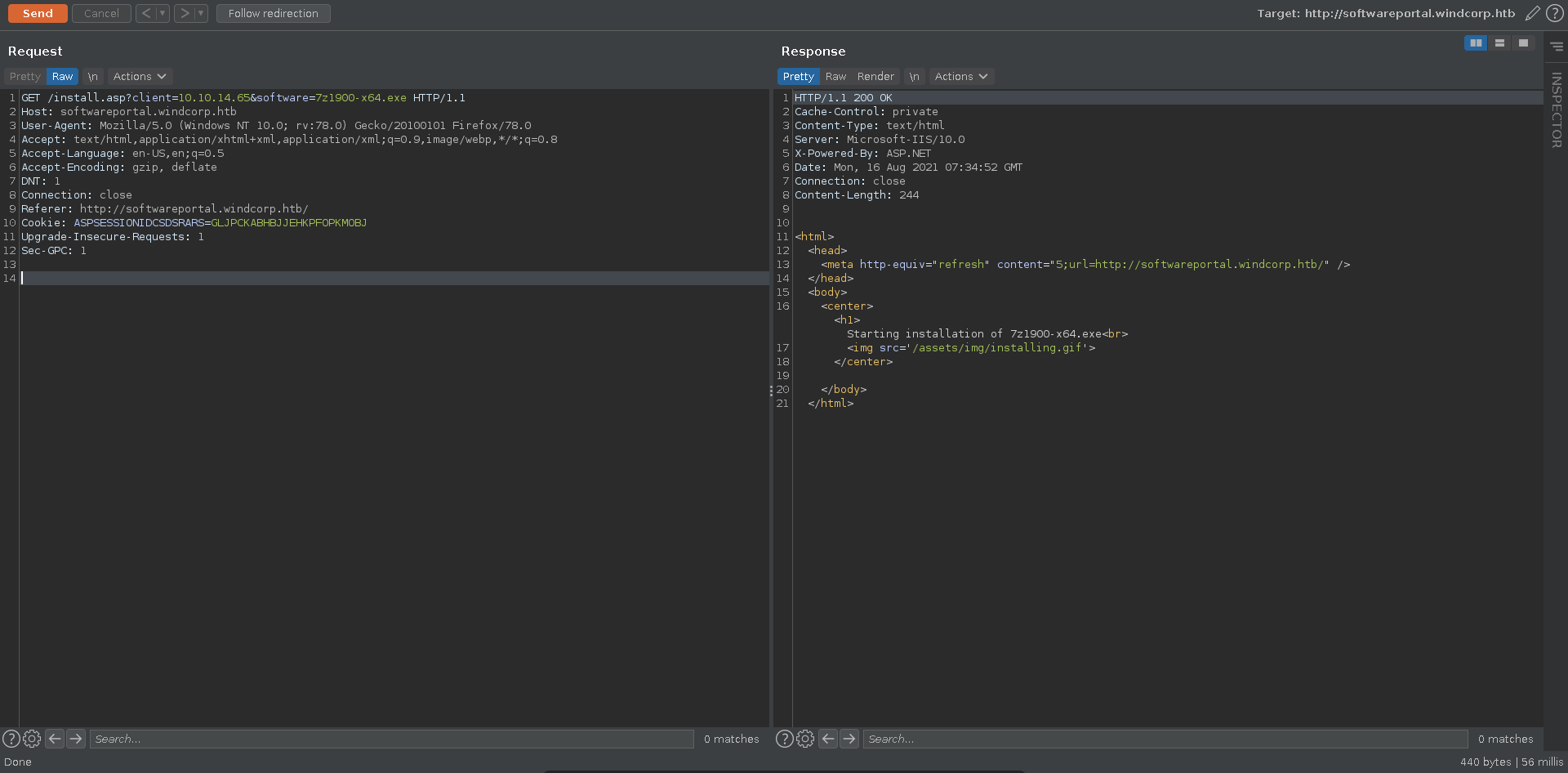
Scrolling further down the page we can click on multiple tools to install. Checking the query string on the bottom left of our browser windows it takes two parameters, client and software. The client parameter is an ip and the software the executable to be installed. We click on the button and send the request to burp repeater.
Since we have control over the ip we might be able to make it connect to us and capture a NetNTMLv2 hashr. To do this we first start responder and then send the request with our ip in the client parameter.
1 |
|
Checking responder, it captured the NetNTLMv2 hash for the localadmin user, which cracks quickly using hashcat.
1 |
|
1 |
|
Jamovi
We can now authenticate to smb with the credentials windcorp/localadmin:Secret123 and list the shares. There are two non default shares CertEnroll and Shared.
1 |
|
Checking out the Shared share there are multiple omv documents, which is the format jamovi stores tables. One of the files has a creation date of today making it particularily interesting so we download it.
1 |
|
Looking for vulnerabilities we find a recent CVE by the author of the machine without PoC. This mentions a XSS in the column name of the omv. Since jamovi is an electron app, XSS means code execution on the target os instead of its browser, thus making it particularily interesting. To modify the omv we need to figure out what we exactly have at hand here. A quick check with file shows it seems to be a zip.
1 |
|
1 |
|
Looking at the metadata.json it seems to contain the column name so we modify the first columns name to include a script hosted by us.
1 |
|
After finishing we compress the file to a zip archive again.
1 |
|
The next step is to create a javascript file with the code we want to run on the target. We can use the child_process module for this, download a netcat binary again and invoke it in the next command.
a.js
1 |
|
First we set up our ncat listener and host the javascript file with a python webserver.
1 |
|
1 |
|
Next we copy our modified Whatif.omv over the initial one.
1 |
|
After about 5 minutes we get a hit on our webserver first downloading a.js and then nc.exe. As the second command gets executed we recieve a shell on our listener as the user diegocruz and can grab the user flag.
1 |
|
1 |
|
SYSTEM
Certificate template ACL
Looking at the groups of the user he is in the webdevelopers group. Since ADCS seems to be installed it might be interesting to list templates on the target.
1 |
|
Doing this with certutil we find the Web template over which the webdevelopers group has full control, meaning we can abuse this to impersonate any user in a few steps.
1 |
|
First we need import ADCS.ps1 and PowerView.ps1 to interact with the template.
1 |
|
Using Get-ADCSTemplate on the Web template we retrieve information about it. Currently this template is used for Server-authentication, which isn’t of much use to us.
1 |
|
Since we have full control over the template we can easily change this though. To make this a Client-authentication template we have to change the pkiextendedkeyusage and msPKI-Certificate-Application-Policy property which we do using Set-ADCSTemplate from ADCS.ps1.
1 |
|
We can verify the properties got changed by calling Get-ADCSTemplate again.
1 |
|
Now we dowload Certify.exe andRubeus.exe for the next steps to take.
1 |
|
First we need to know the CA which we can obtain with certify.
1 |
|
Now we can request a certificat for the template with the altname Administrator using certify. At the bottom of the output we already get the command presented to convert the .pem into a .pfx using openssl, which we do in the next step on our linux machine specifying a password of our choice
1 |
|
1 |
|
To authenticate with the resulting certificate using rubeus, we transfer it over to the target.
1 |
|
Since we now own a Client-authentication certificate with the altname administrator we can use rubeus to request a TGT as him. The password is the one we specified generating the certificate with openssl.
1 |
|
After recieving the ticket we can verify it got cached with klist.
1 |
|
Having a TGT for the administrator in our cache we can now invoke commands as him on the machine.
1 |
|
We can already read the flag now but let’s get a reverse shell. We first set up the ncat listener again and use the netcat binary we uploaded earlier to send the shell back to us.
1 |
|
1 |
|
We get a connection as administrator and can pick up the root flag.
1 |
|
Unintended / password reuse
Until some time after release there was a unintended route making the box really short and easy. On the docker container the password for the user iisadmin was reused for the domain administrator.
1 |
|
Dumping the sam on the docker with mimikatz you could retrieve the NTLM hash.
1 |
|
With this you could now simply psexec into the machine and grab both flags.
1 |
|
1 |
|
1 |
|