Previse is an easy rated machine on HackTheBox created by m4lwhere. For the user part we will exploit direct access to the registration form, which will give us access to the source code of the webpage upon logging in. The source code reveals the database credentials and a command injection vulnerability, which leads to a reverse shell. To obtain root we will exploit a path injection in a script we are allowed to run as root with sudo.
User
Nmap
As always we start our enumeration off with a nmap scan against all ports, followed by a script and version detection scan against the open ones to get a full picture of the attack surface.
All ports
1 | |
Script and version
1 | |
Account creation
There are only 2 ports open on the machine with http being the bigger attack surface so we will start there. Browsing to it we are greeted with a login page.
Since the server is running php we can add this extension to our gobuster scan to retrieve additional files. This also reveals an accounts.php.
1 | |
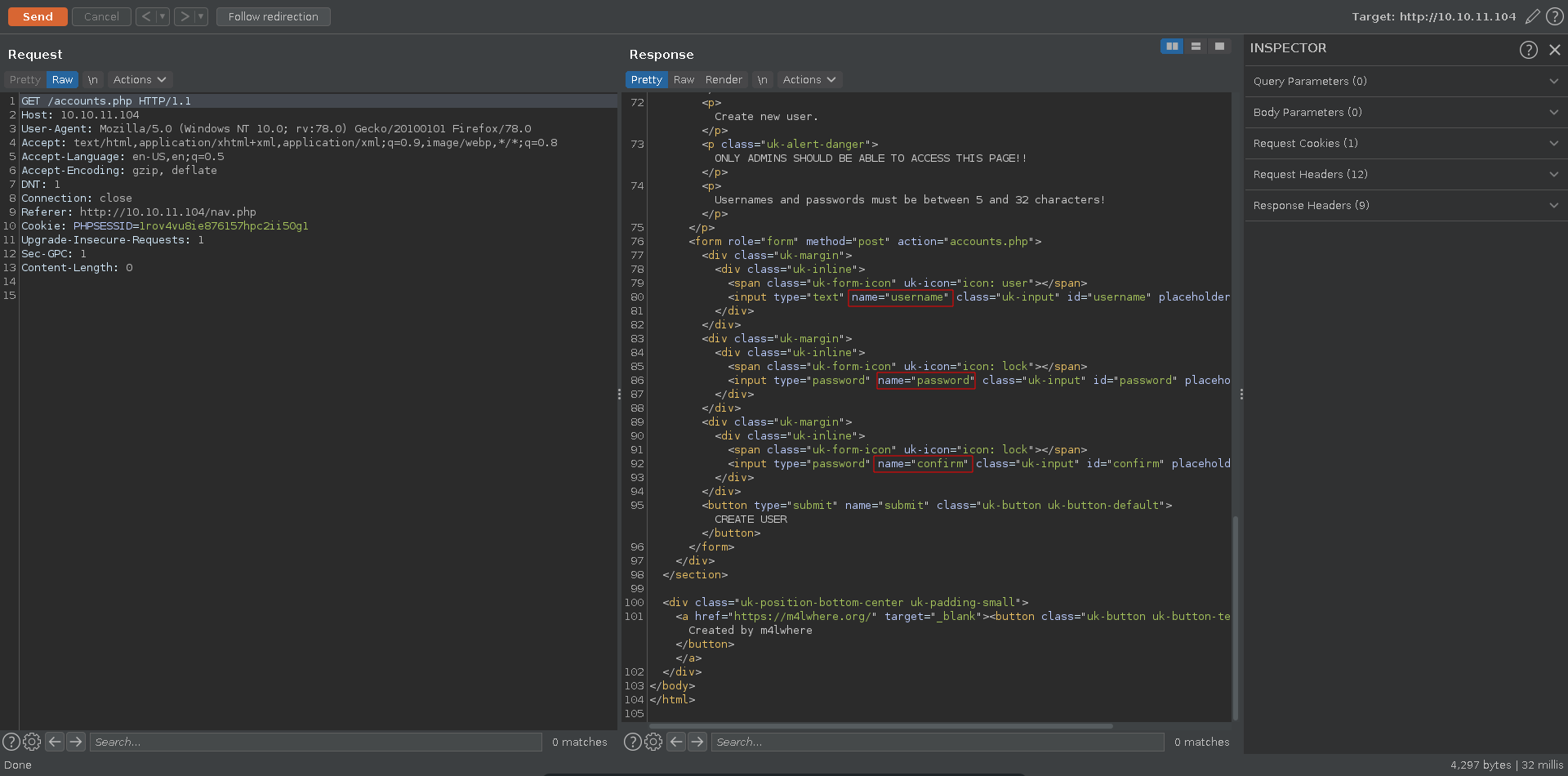
Going directly to this page we get redirected to /login.php, if we however request it directly in burp we can see the source of the page and that it expects 3 parameters to create an account.
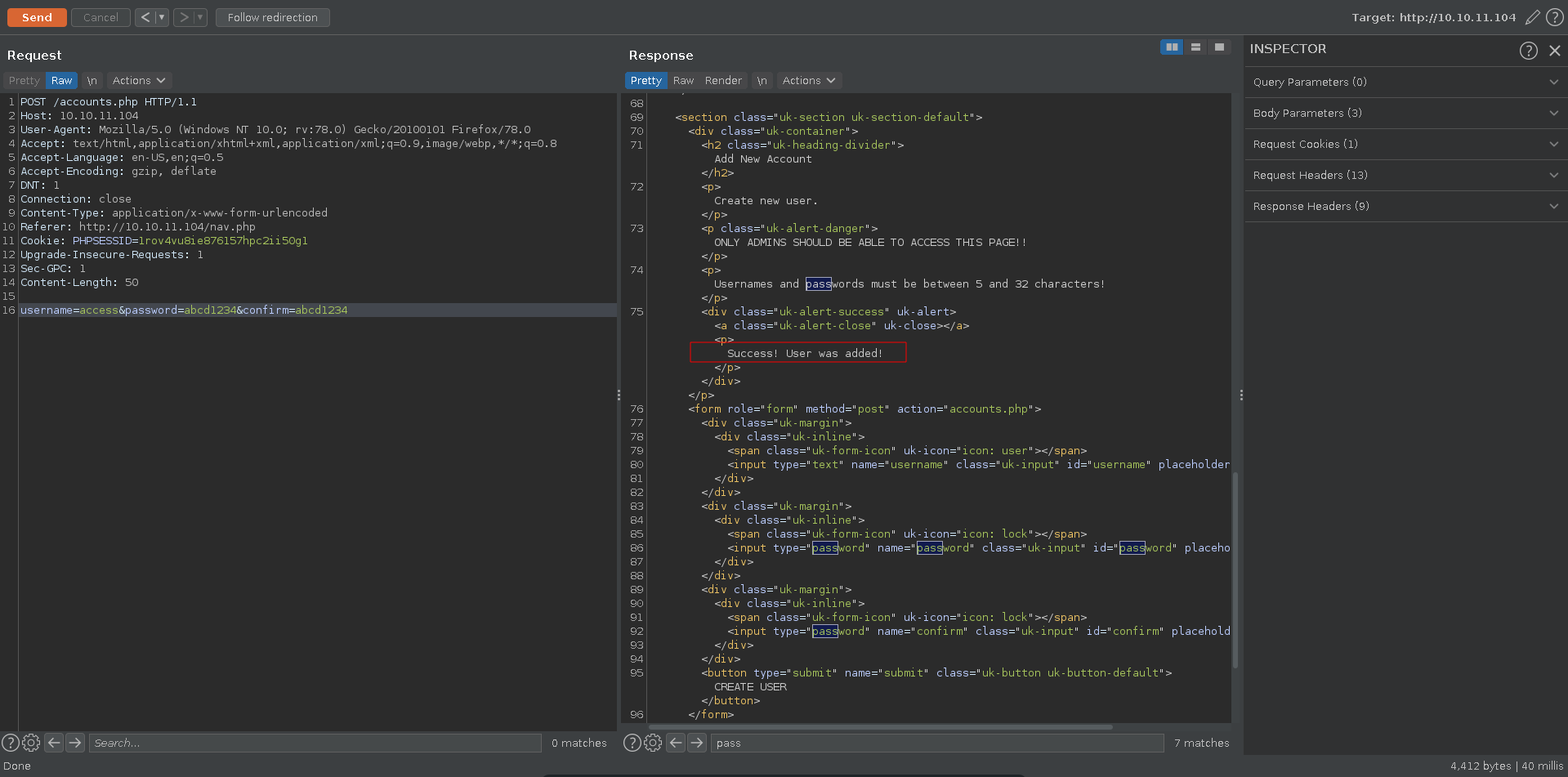
Sending a post request with all 3 variables we see that our account was successfully created.
This enables to log into the webpage now.
Source code => command injection
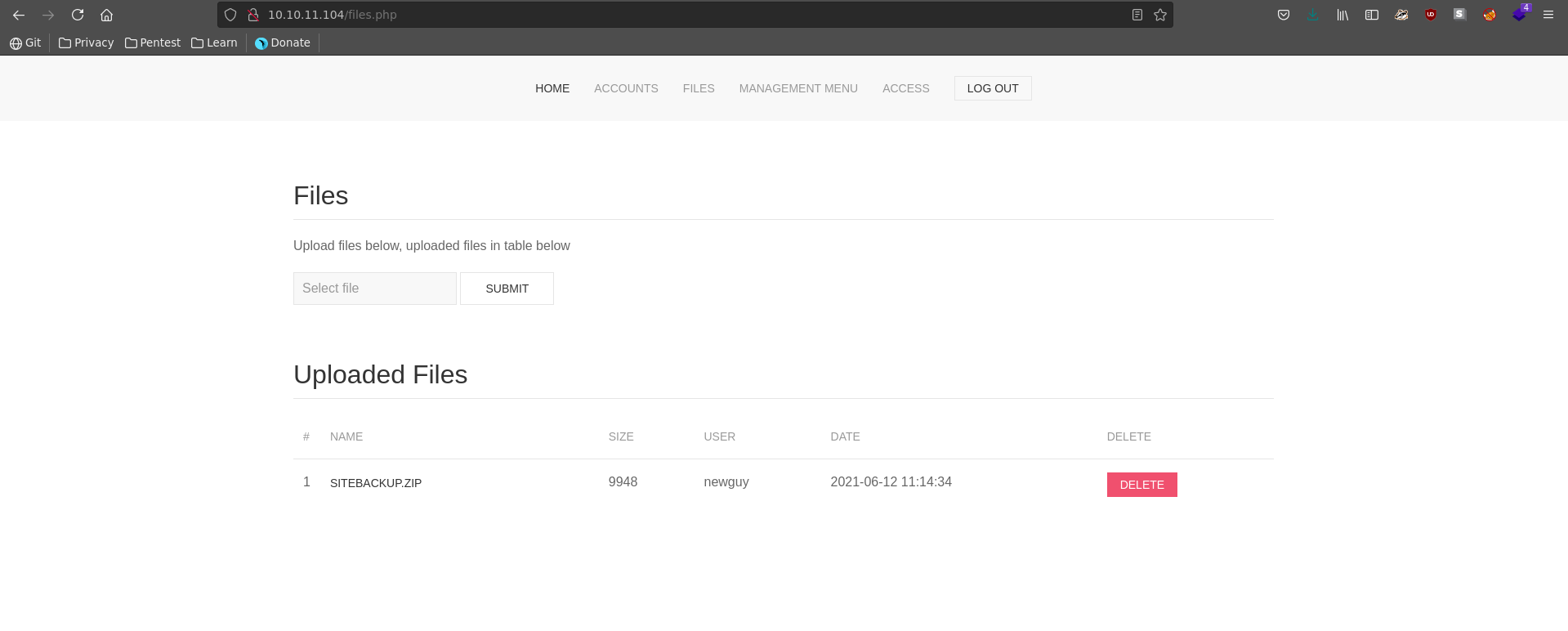
Going over to the files tab we see a sitebackup.zip which we can download.
Opening the zip file it seems to indeed contain the source code of the web application.
1 | |
Looking at the config.php we find the credentials to connect to the backend mysql database, which might be usefull later on.
config.php
1 | |
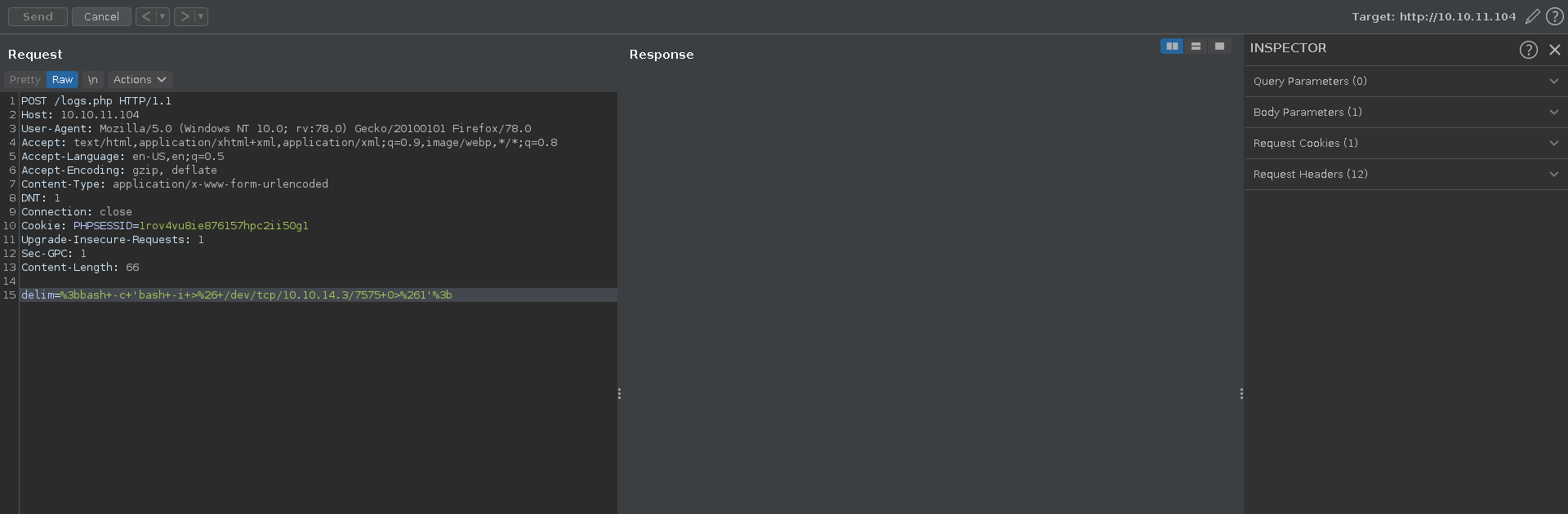
What is very helpful now is the command injection vulnerability in logs.php. The POST parameter delim gets directly passed to the exec function which runs a python script.
logs.php
1 | |
To exploit this we first set up our ncat listener.
1 | |
Then we send ourselves a reverse shell with burp in the delim parameter by chaining a command to it with ;.
After recieving the shell we upgrate it to get a full tty and fix the terminal size.
1 | |
Database hash
Since we have the database credentials we can now connect to it.
1 | |
There is only one custom database named previse.
1 | |
Looking at the tables, accounts looks particularily interesting.
1 | |
Getting everything from this table we can retrieve the hash for the user m4lwhere.
1 | |
This cracks after some time with hashcat.
1 | |
Testing the credentials with ssh we can login and grab the user flag.
1 | |
Root
Path injection
Looking at sudo permisions we can see m4lwhere can run a bash script as root.
1 | |
The script calls two binaries with relative PATH and since the env is not reset this leaves us enough space to inject into the PATH with our own custom version of date or gzip.
/opt/scripts/access_backup.sh
1 | |
To do this we create our own custom version of date first in the /tmp folder.
/tmp/date
1 | |
We mark it as executable and adjust the PATH so our date gets called first. With everything set we can now run the script with sudo.
1 | |
After running the script we can confirm bash has the suid bit set.
1 | |
This let’s us drop quickly into a root shell and add the root flag to our collection.
1 | |
1 | |