Cap is an easy rated machine on HackTheBox by InfoSecJack. For the user part we will find credentials for the ftp service in a pcap by abusing IDOR. These credentials are reused for ssh which gives us access to the machine as nathan. To get root we will then abuse the suid capability on python.
User
Nmap
As always we start our enumeration of with a nmap scan against all open ports, followed by a script and Version detection scan against the open ones to get an initial picture of the attack surface.
All ports
1 |
|
Script and version
1 |
|
Pcap
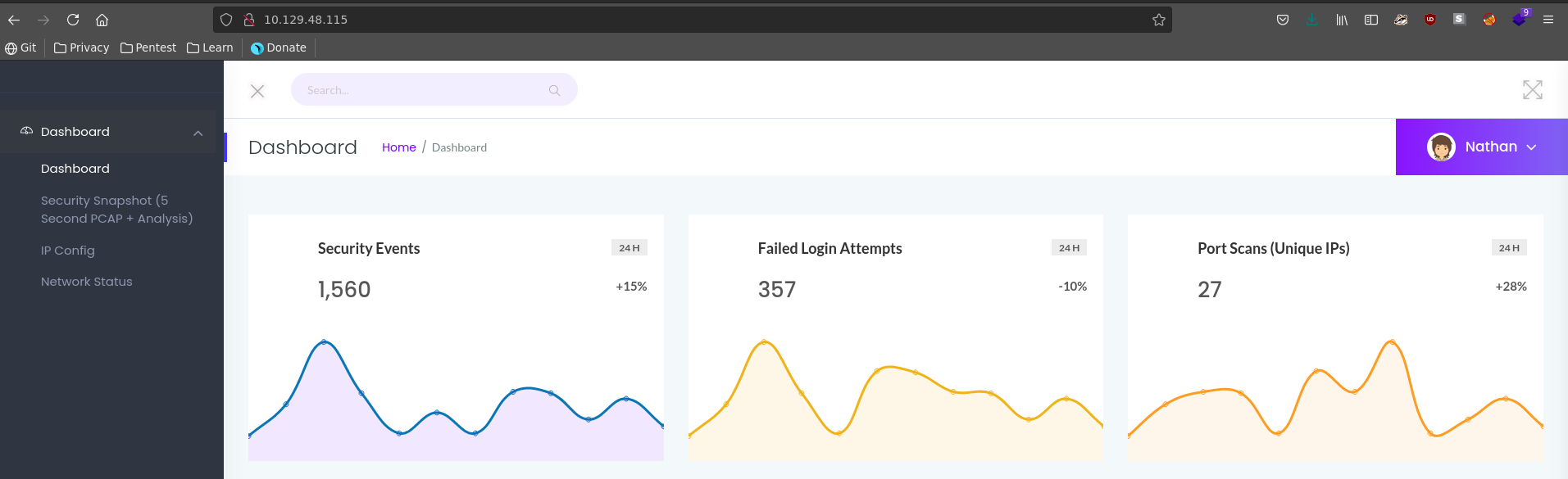
Port 80 seems to be the most promising inital target and going there we see a security dashboard with 3 different functionalities. We can download a PCAP, look at the IP configuration and look at the output of netstat.
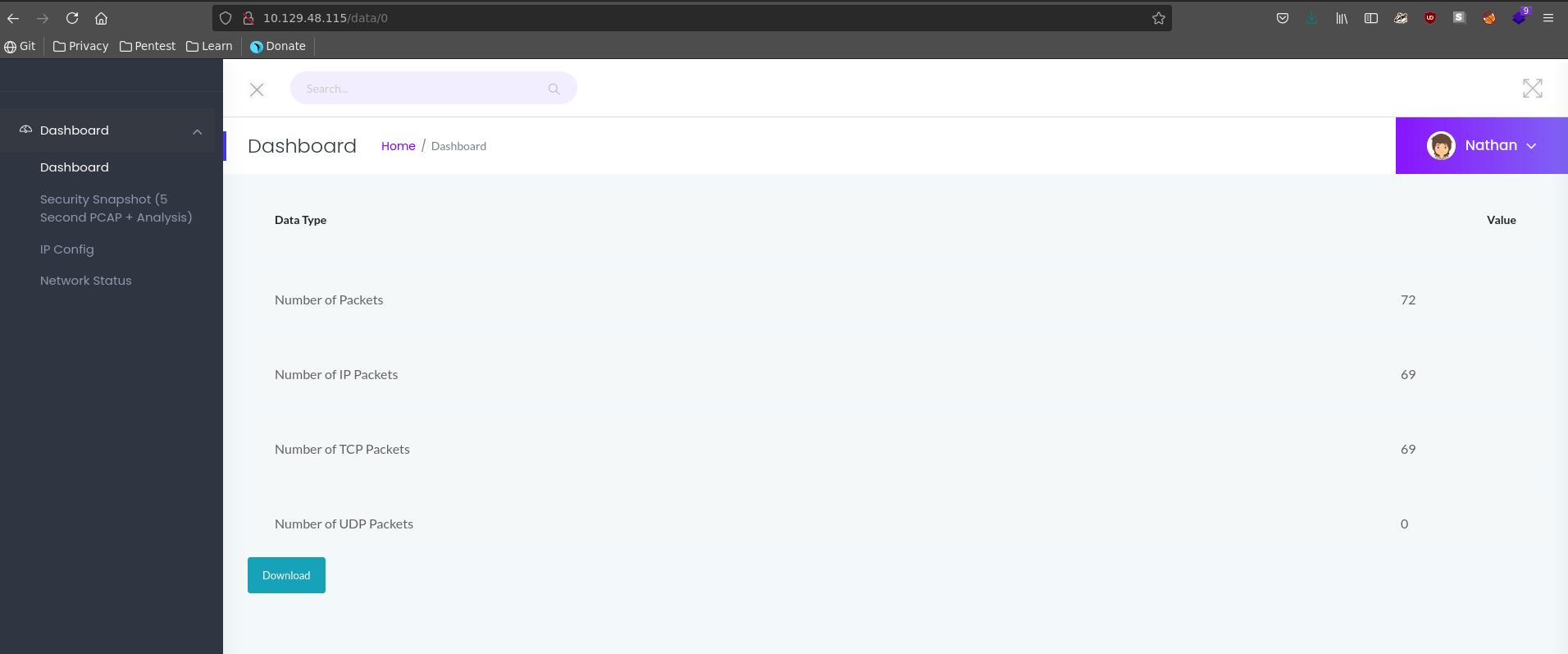
Going over to the Security Snapshot PCAP we don’t get any usefull information downloading the file presented. We can however change the number after data in the URL to download the first available pcap 0.
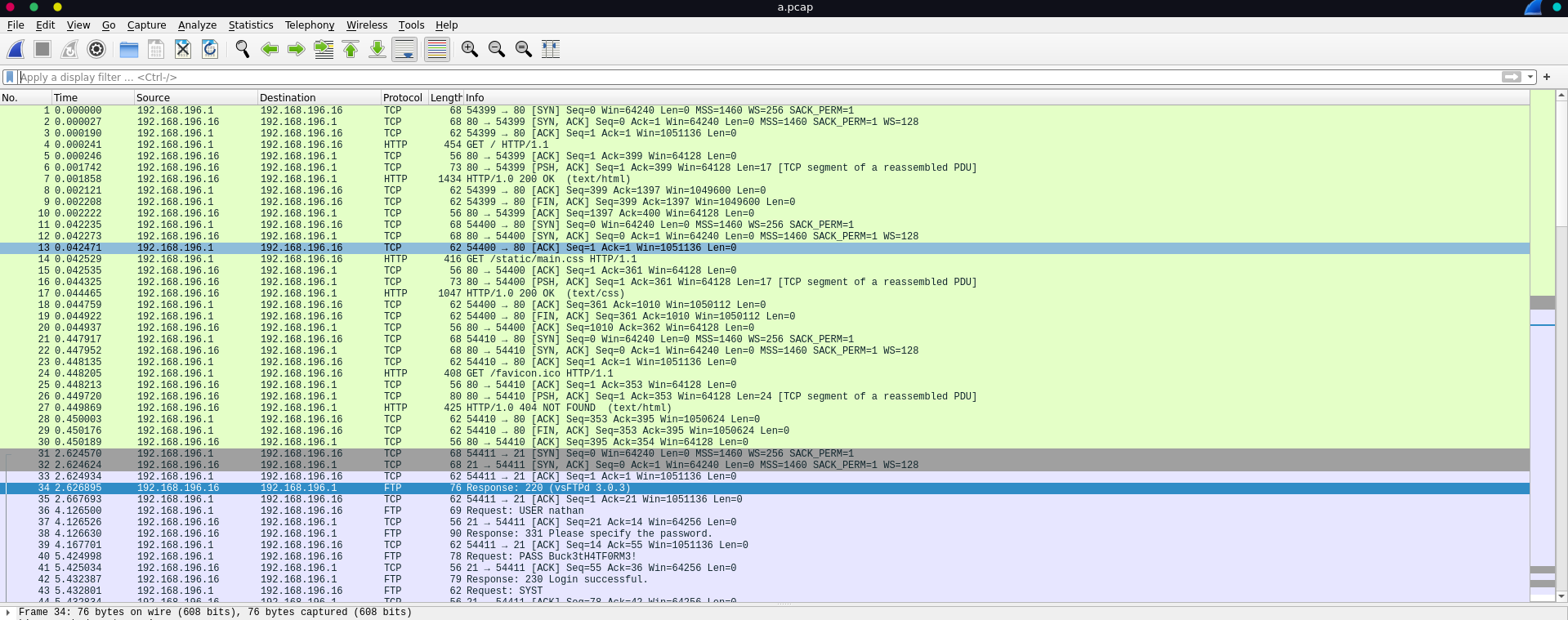
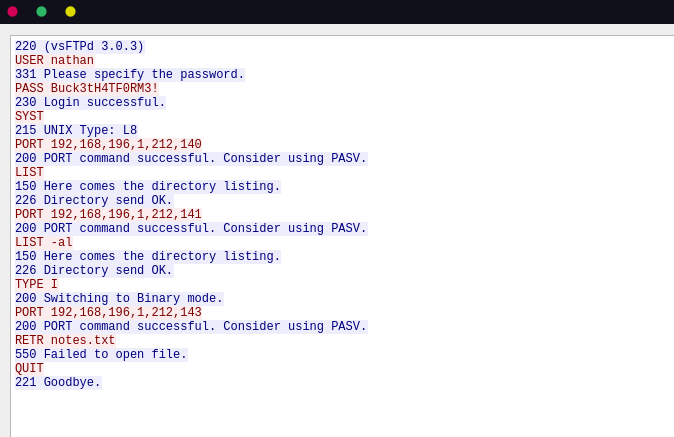
Analyzing this PCAP in wireshark we see some HTTP and FTP traffic.
Following the TCP-Stream for the FTP traffic reveals FTP credentials for the user nathan.
This credentials where reused for ssh which gives us access to the machine and the user flag.
1 |
|
Root
Python Capability
Looking at the capabilites we see that python has the cap_setuid capability set. This means we can set the user id running python.
1 |
|
We can abuse this quickly to get a shell as root by first importing os, setting the user id to 0 (root) and then spawning a bash shell. Now we can add the root flag to our collection.
1 |
|