Delivery is an easy rated machine on HackTheBox created by ippsec. In this walkthrough we will first abuse a logic flaw in 2 web applications, which let us use a temporary email address in a ticket system to recieve a verification email for a running Mattermost installation. Being logged into Mattermost we get some valuable information in a chat log which we use to get to the first user. For the root part we will will find some database credentials, which we use to get password hashes. Finally we will crack one of the hashes with a hashcat rule and log into the root account.
User
Nmap
We start our enumeration on the box with a nmap scan against all ports to get a full picture of the attack surface, followed by a version detection and script scan against the open ports.
All ports scan
1 | |
Script/version scan
1 | |
Web
On the website we get greeted with a message stating we should check out the helpdesk for all email related support.
Clicking on the link leads to heldesk.delivery.htb.So we add it to our /etc/hosts file and browse to it.
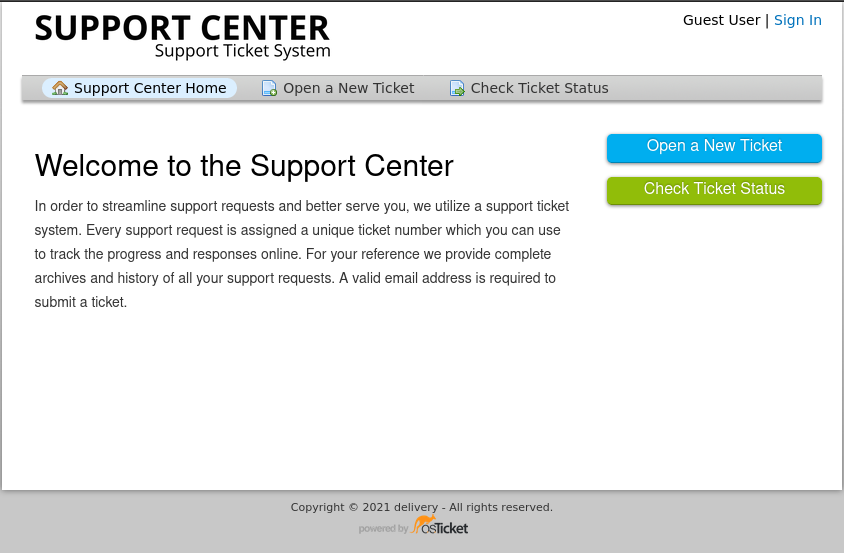
Going there we see a ticket support center, where we can create tickets and check the status of them.
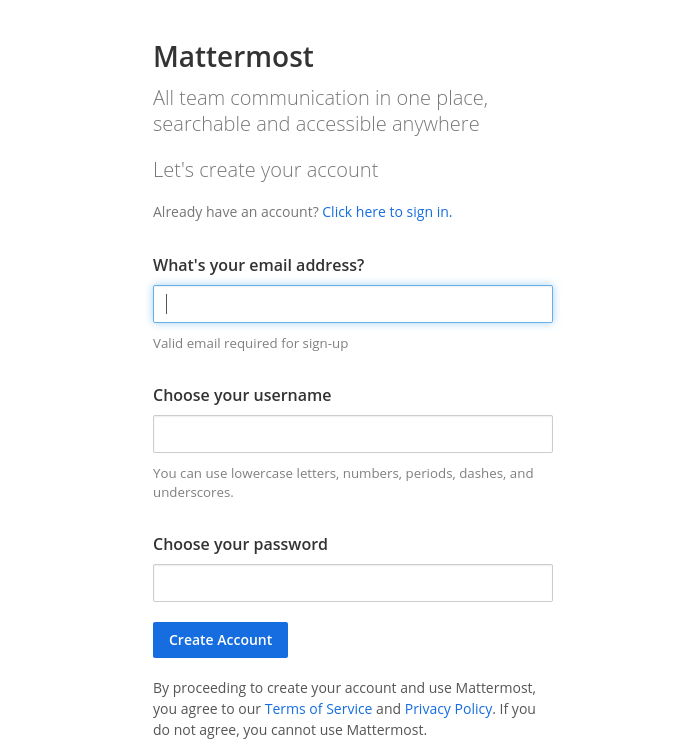
On port 8065 is a Mattermost application where we need a valid email address to verify the registration. Since the HackTheBox network is not connected to the internet we have to do this with an existing service on the machine in multiple steps.
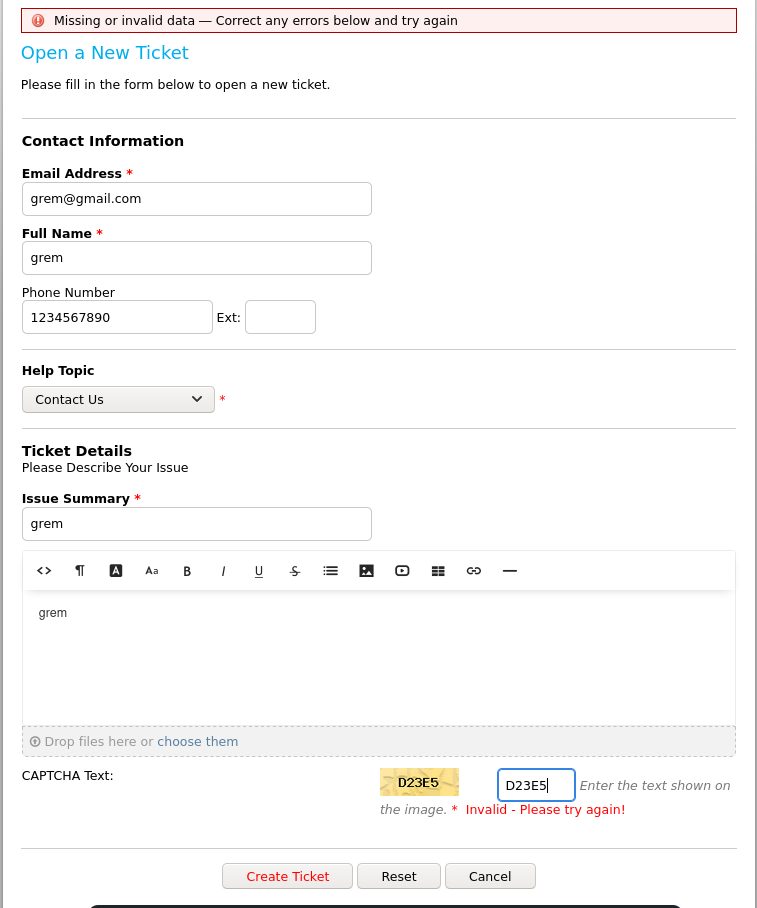
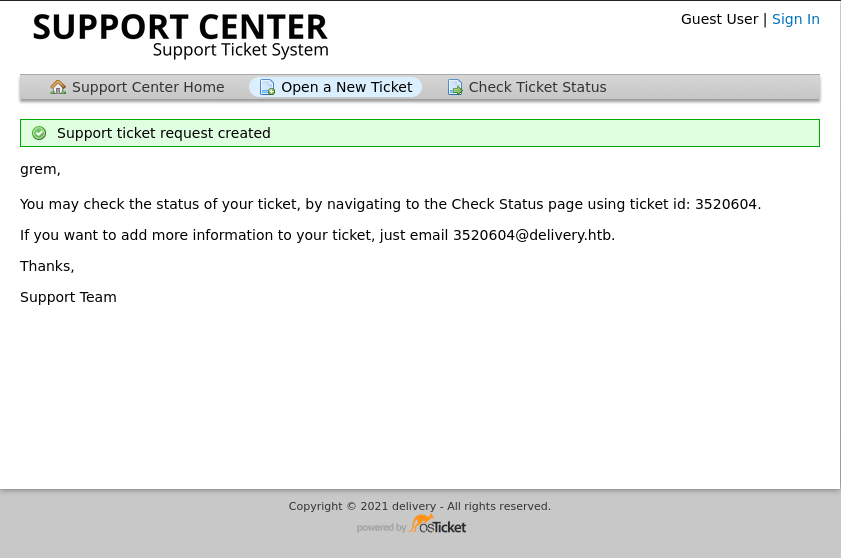
In a first step we create a ticket on the helpdesk platform.
This gives us a temporary email to add information to the ticket.
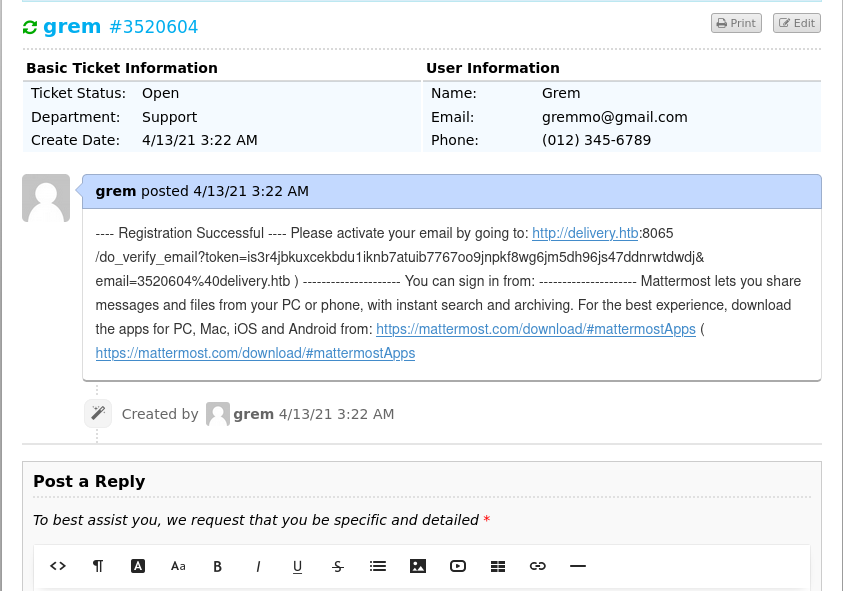
Using this email to sign up to Mattermost, we can now retrieve the confirmation e-mail in the check ticket status tab and use the verification link for Mattermost.
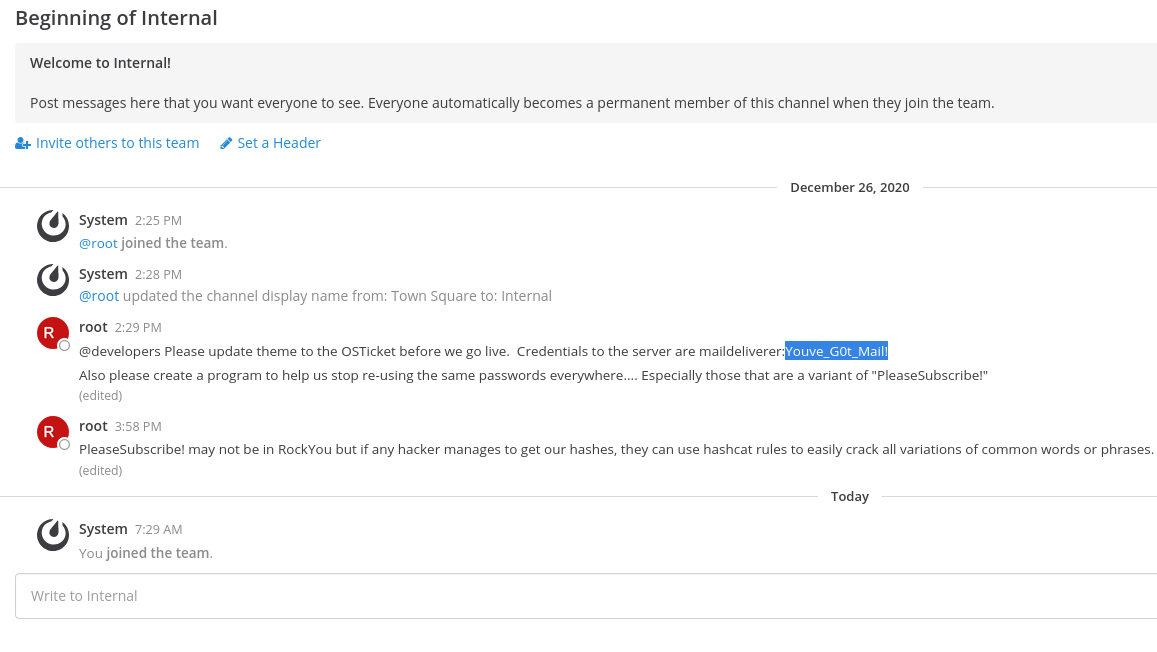
Logged into Mattermost there is an interesting conversation in the Internal channel between System and root. In the conversation there are the credentials maildeliverer:Youve_G0t_Mail! and it is also hinting that the password PleaseSubscribe! might be reused throughout the machine.
With the credentials we can log in with ssh as the user maildeliverer and are able to pick up the user flag.
1 | |
Root
Mysql
Looking around we find the database credentials for Mattermost in the file /opt/mattermost/config/config.json
1 | |
The password for the account is a hint for the next steps to take.
First we log into mysql to retrieve the usernames and passwords from the mattermost.Users table.
1 | |
Following the 2 earlier hints, we are particularly interested in the root hash in combination with variations of the password PleaseSubscribe!.
Cracking the hash
With the predefined best64.rule hashcat rule we are able to crack the password of the account in a short amount of time.
1 | |
1 | |
With this password we can now switch to the root user on the machine and grab the rootflag.
1 | |