ScriptKiddie is an easy rated machine on HackTheBox by 0xdf. For the user part we will exploit a web application that let’s us generate mfsvenom files with templates abusing CVE-2020-7384. This gives us a shell as the user kid, from whom we pivot to the user pwn abusing a running cronjob with another command injection. As pwn we can run msfconsole as root, which let’s us drop into a rootshell executing bash.
User
Nmap
As usual we start our enumeration on the target with an allports nmap scan to capture the whole attack surface, followed by a script and version detection scan to obtain more detailed information on the open ports.
Nmap allports
1 | |
Nmap script and version scan
1 | |
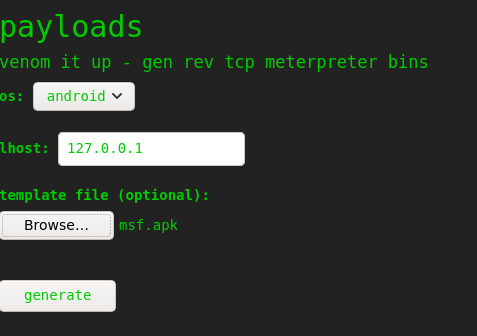
Msfvenom template
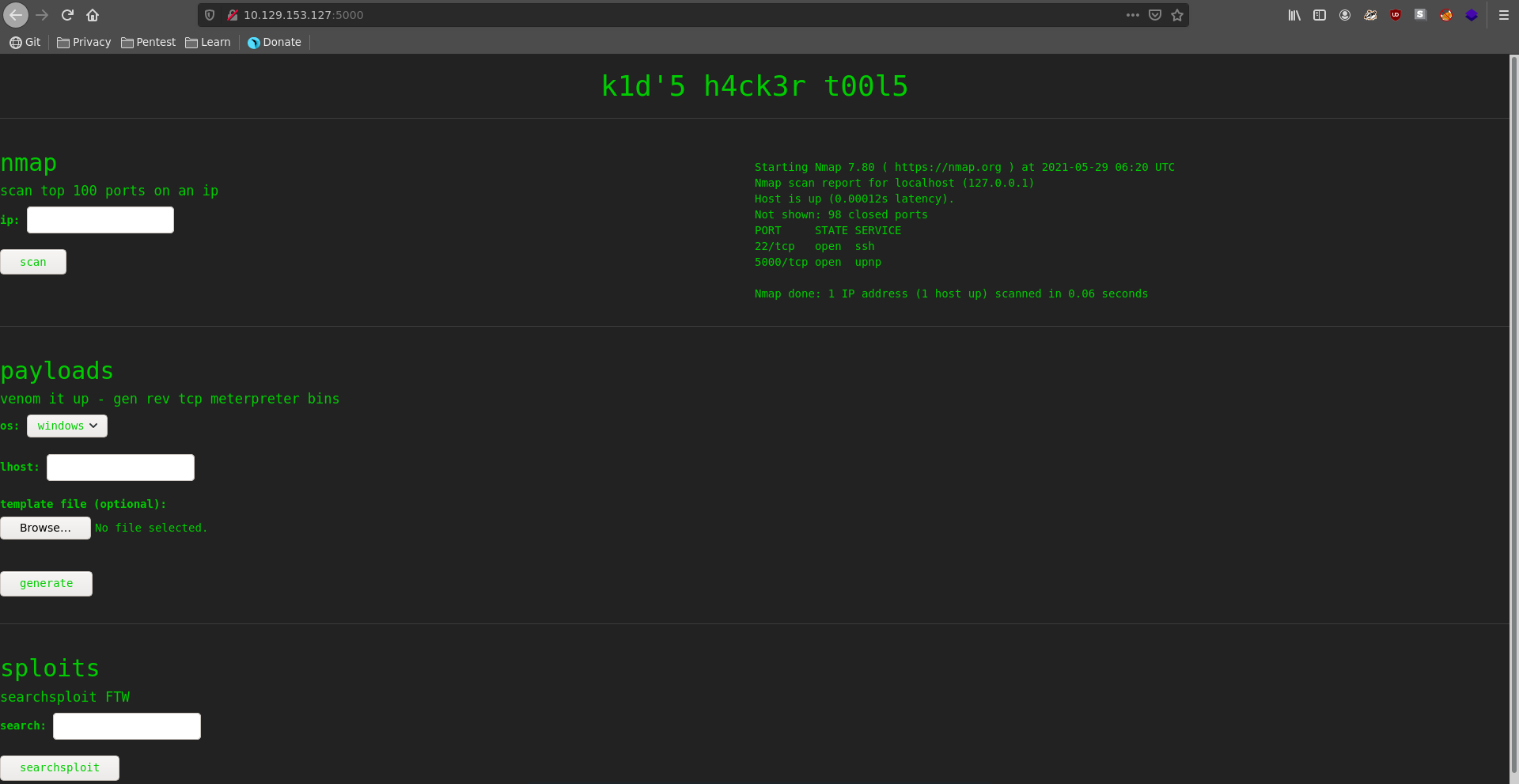
Going over to the werbserver on port 5000 we can see that it is offering 3 different applications.
We can scan a host with nmap entering an ip, generate msfvenom payloads with templates and also perform a searchsploit search. Scanning localhost with the nmap service we don’t get any additional information. The interesting thing here is the payload generation with a template because it is vulnerable to CVE-2020-7384.
This works by exploiting a command injection vulnerability in msfvenom when generating an apk payload with a template file.
In a first step we will generate the malicious apk file using the msf module unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection.
1 | |
Next we set up our ncat listener on the selected port.
1 | |
With preparations set we can now generate the msfvenom payload with our malicious apk template.
After a short moment we get a hit back on our ncat listener and upgrade the shell. Now we can grab the user flag in /home/kid.
1 | |
1 | |
Root
Command injection #2
Looking around in the other users home directory we find the script scanlosers.sh. This script reads the logfile in home/kid/logs/hackers takes the third argument in each row, seperated by a space and runs a nmap script against it. This is also vulnerable to a simple command injection, which we can use to gain a shell as the user pwn.
1 | |
First we set up our listener again.
1 | |
Then we place our command injection in the logfile and recieve an instant shell on the target.
1 | |
We upgrade our shell again and continue on our way to root.
1 | |
Sudo on Metasploit
Checking the sudo permission we see that pwn can run msfconsole as root. Since we can issue os commands inside msf, this gives us an easy way to escalate to root.
1 | |
We start up msfconsole with sudo and execute /bin/bash.
1 | |
This drops us into a rootshell and we can grab the rootflag.
1 | |