User
Paper is an easy rated machine on HackTheBox created by secnigma. For the user part we will abuse an information leak through a CVE in wordpress to register an account in a rocket chat installation. In rocket chat a bot is vulnerable to LFI which gets us a password that is reused for the user dwight. In the root stage we will go over the unintended method of using pkexec and the intended one of abusing polkit to add another user with sudo rights and root the machine.
Nmap
As usual we start our enumeration with a nmap scan against all ports followed by a script and version detection scan against the open ones to get an initial overview of the attack surface.
All ports
1 | |
Script and Version
1 | |
Wordpress draft
From the open ports http and https seem to be most promising. Opening port 80 in our browser we see the the Centos http server test page.
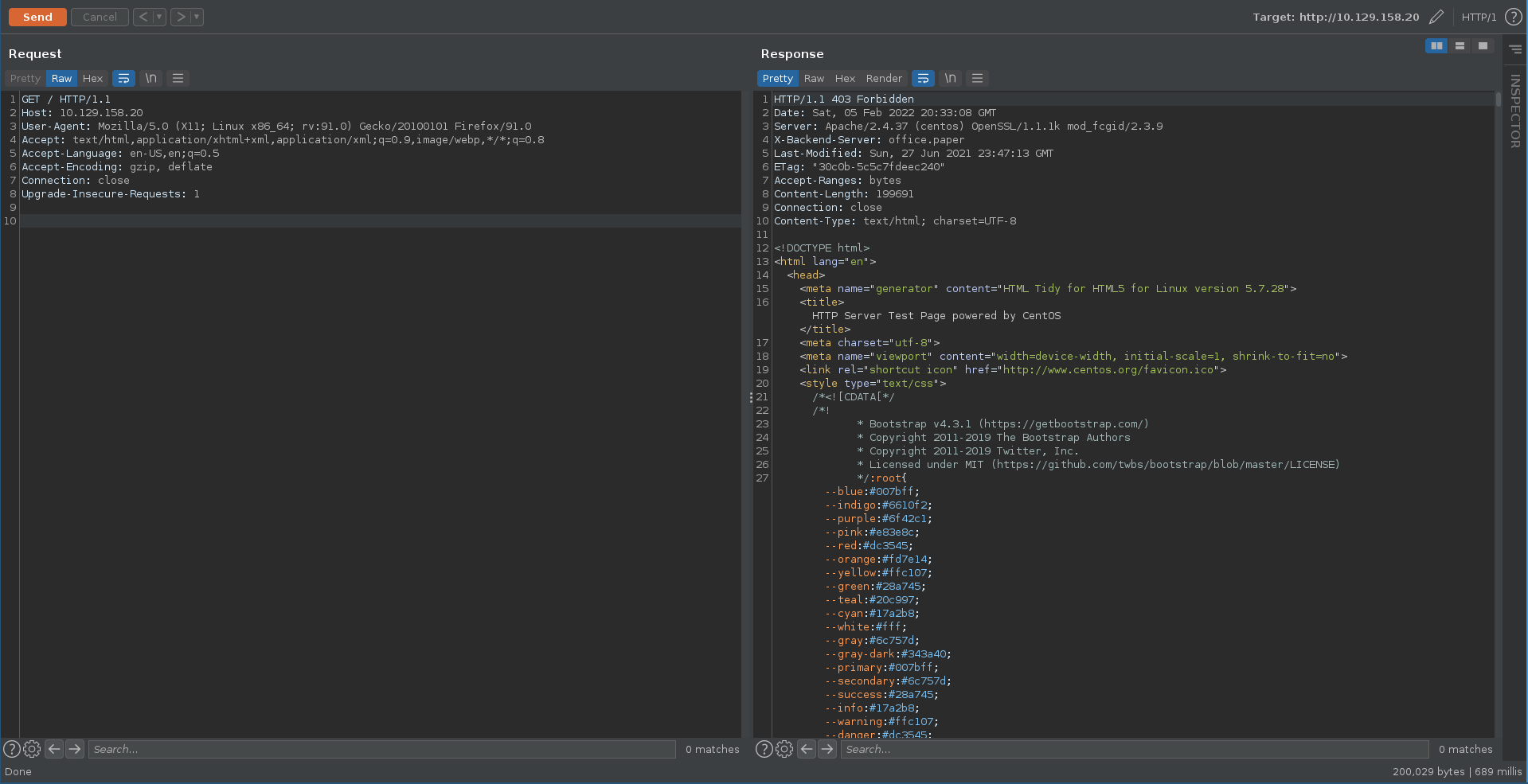
Intercepting a request in burp and looking at the response headers in repeater we can find that it leaks the vhost office.paper which we add to our /etc/hosts file.
Opening http://office.paper in our browser we see a wordpress blog.
Scanning the page using wpscan we can identify the version to be 5.3 and thus out of date.
1 | |
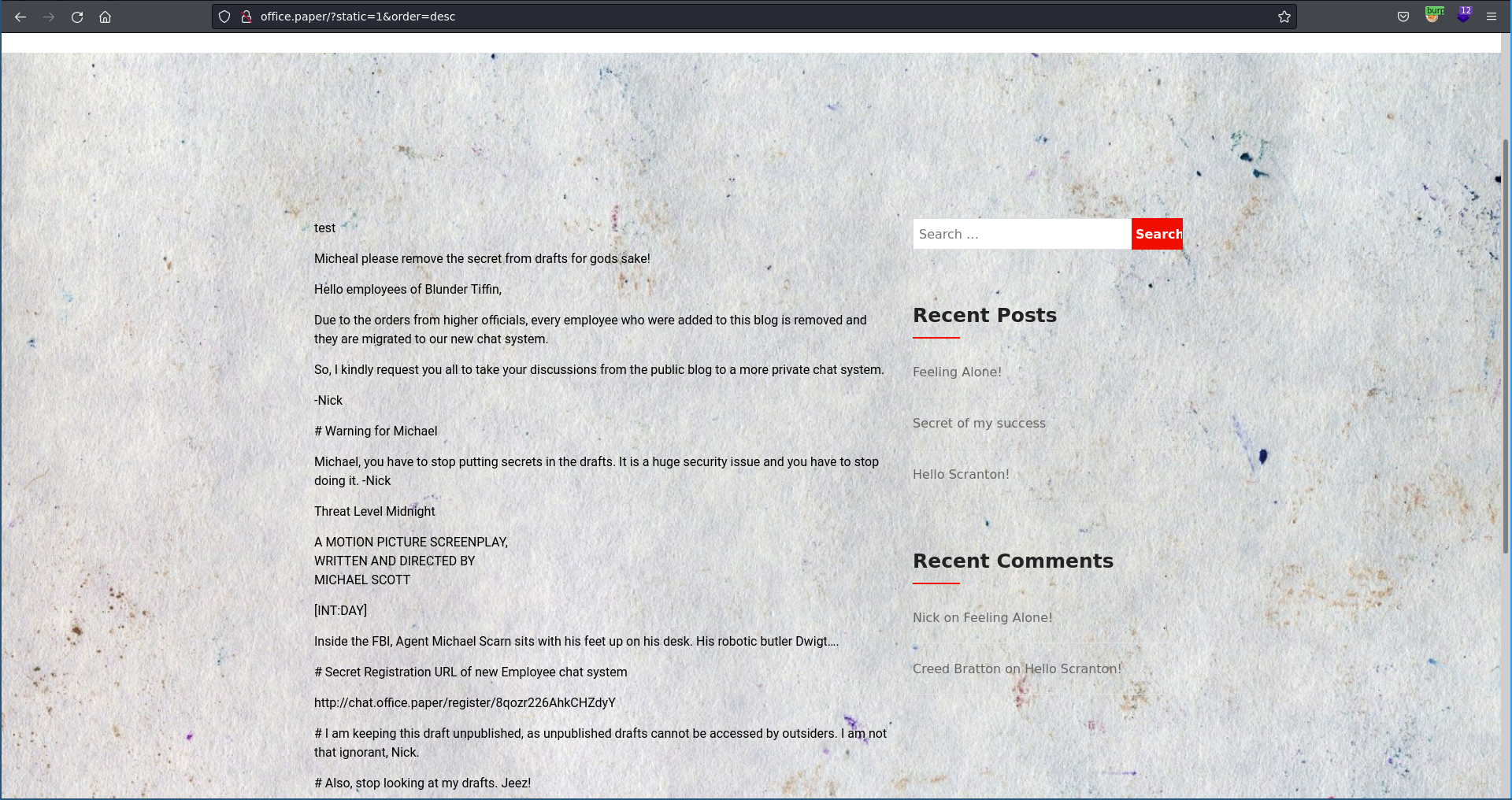
Checking for vulnerabilities in the installed version we find this describing an easy way to leak drafts. Using it as described with asc sorting it we get an error, however changing it to desc we get a draft leaking a rocket chat installation with the secret registration url.
Rocket chat LFI
After adding chat.office.paper to our /etc/hosts aswell and opening the registration link in our browser we are able to register an account on rocket chat.
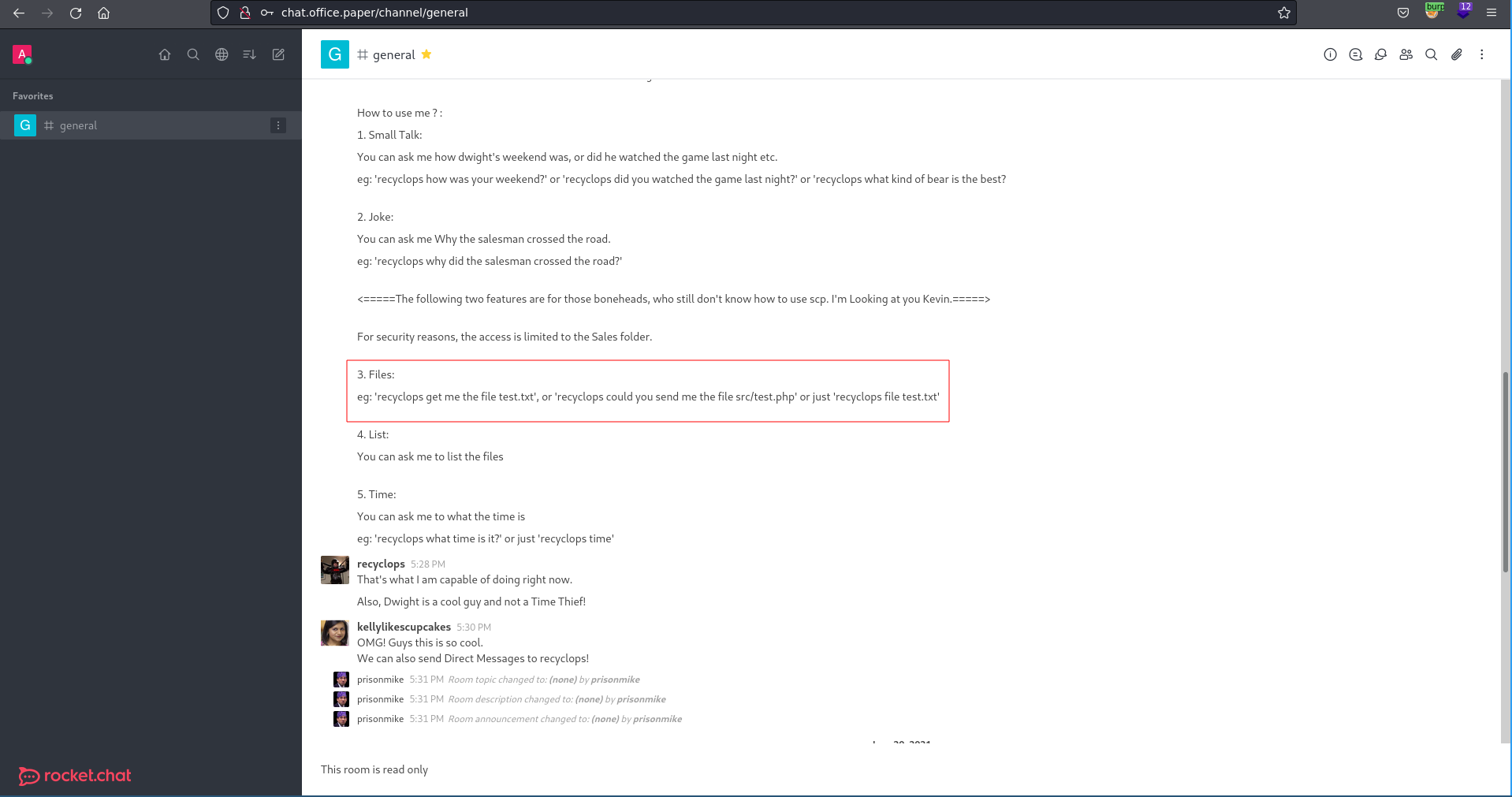
Once logged in with the created account there is an interesting discussion in general where we see some bot functionality. Especially the file retrieval seems to be interesting.
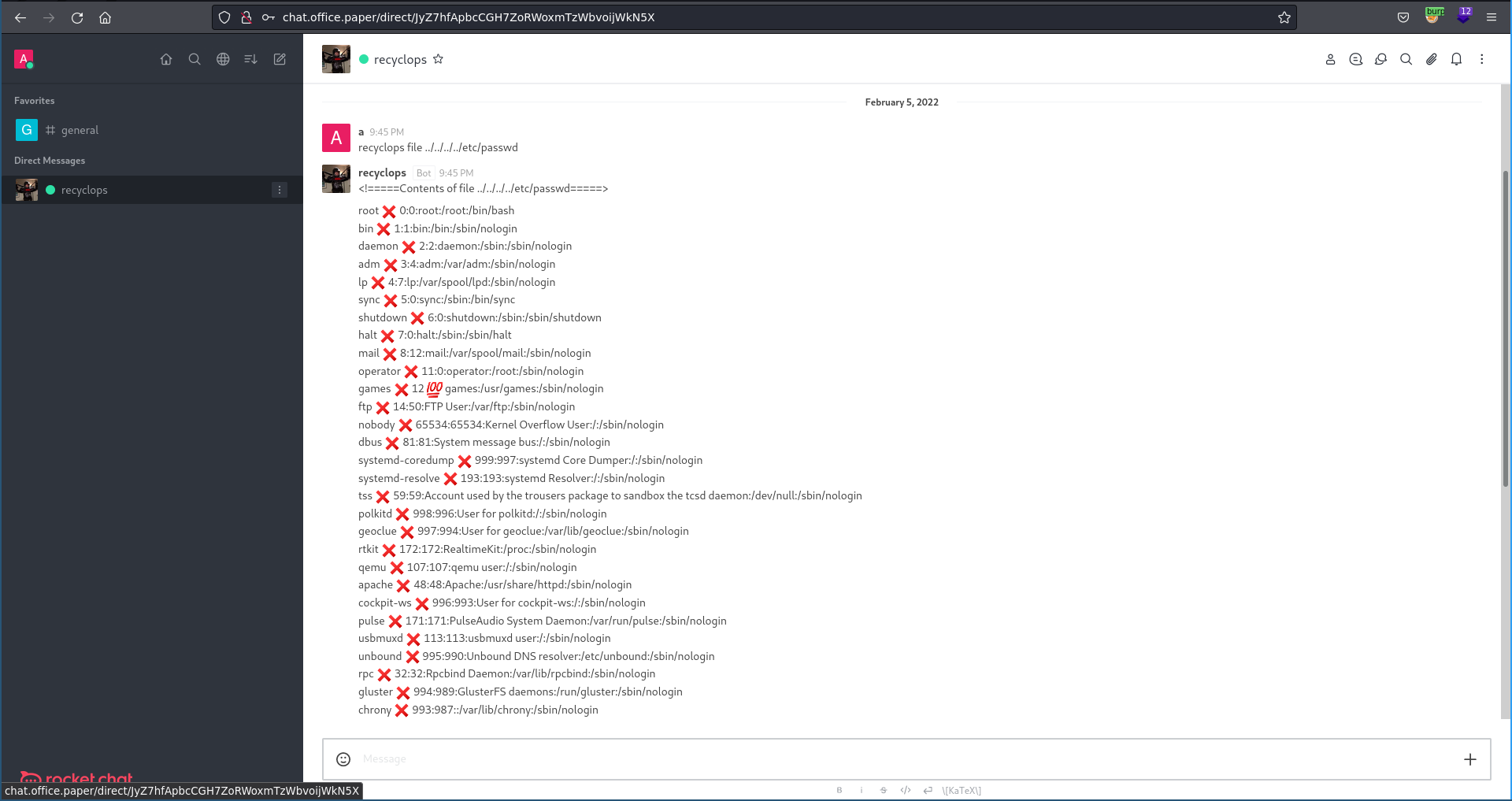
Starting a private conversation with the bot and testing if we can go back to the file system root with ../ it works and we are able to retrieve the /etc/passwd file.
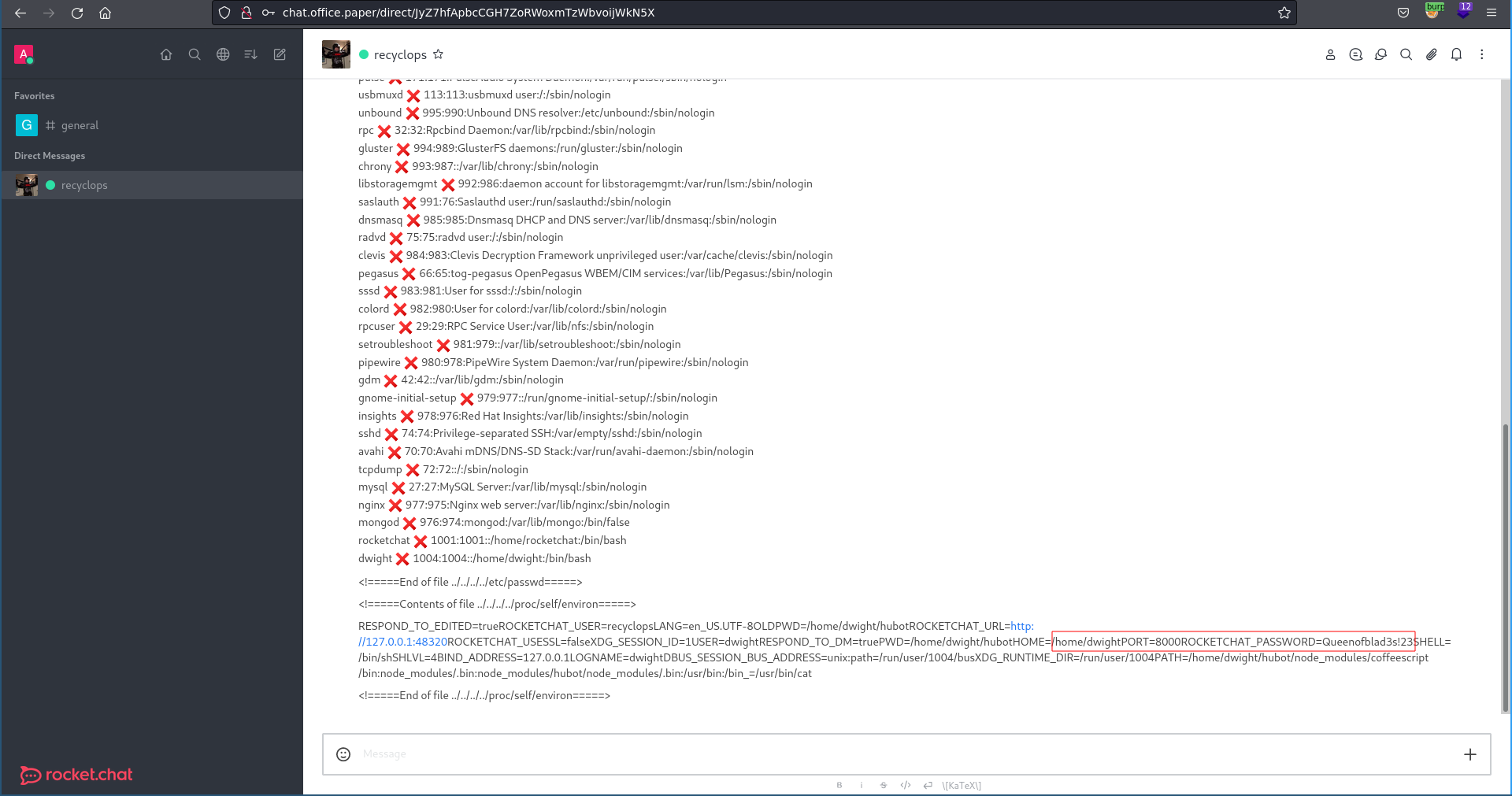
Checking the environment parameters of rocket chat with recyclops file ../../../../proc/self/environ we find the installation is running from the user dwight’s home directory and we also get the password.
Testing for password reuse over ssh we are able to log into the machine and grab the user flag.
1 | |
Root
pkexec
Until some time after release there was an unintended way to obtain root abusing a vulnerable pkexec version.
Checking for suid binaries we can see that pkexec is installed on the machine.
1 | |
Retrieving it’s version we see it is vulnerable to the recent CVE-2021-4034.
1 | |
We can use this PoC to exploit pkexec and obtain root on the machine. Since make is installed on the machine we clone the repo tar it up and scp it to the target as dwight.
1 | |
There we unpack the archive and “make” the binary.
1 | |
Running the exploit we get dropped into a root shell.
1 | |
Polkit
The actually intended solution to obtain root on the machine was to abuse polkit. Checking for the installed version we can see that it is vulnerable to CVE-2021-3560.
1 | |
Using the authors poc script we are able to create a new user with sudo rights and add the root flag to our collection. Note that this exploit is because of its time based nature not completely stable and might need rerunning until it works.
1 | |