Search is a hard rated machine on HackTheBox created by dmw0ng. For the user part we will abuse a password being publicy posted in an image. This leads us to discovering of an account with SPN set whose password is weak. This password was reused by another user who also has an excel sheet containing more credentials pairs stored. One of those credentials work giving us access as Sierra and the user flag. As Sierra we crack a password protected certificate which gives us access to a PowerShell Web Console. There we will dump the gMSA password of another account which has GenericAll rights over a domain admin leading to full compromise.
User
Nmap
As usual we start our enumeration with a nmap scan against all ports followed by a script and version detection scan against the open ones to get an initial overview of the attack surface.
All ports
1 | |
Script and version
1 | |
Posted Password
The scan shows we are dealing with a domain controller. Furthermore the open web ports look interesting so we will start there. Opening it in our browser we see the homepage of Search research.
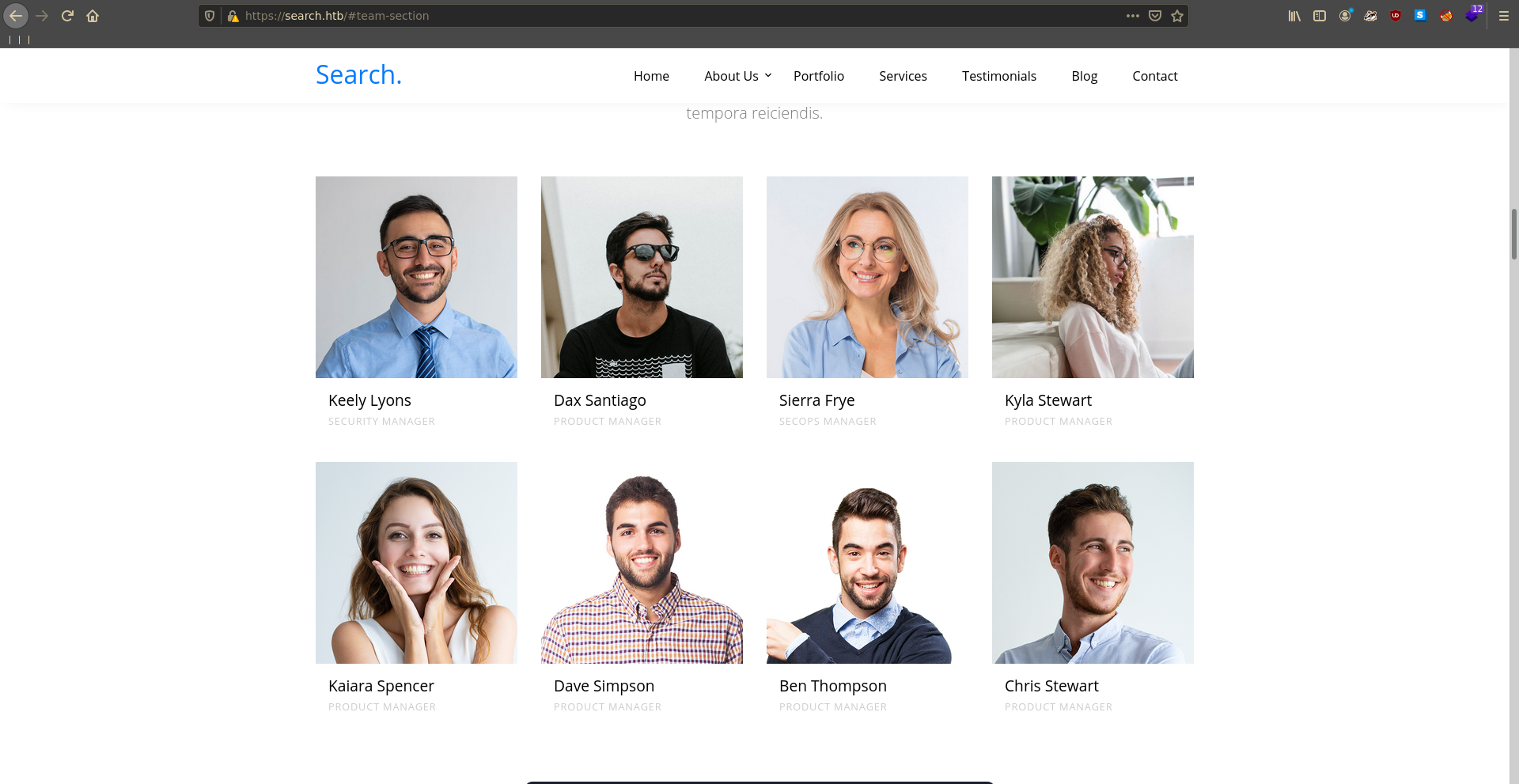
Scrolling a bit further down we can find a few people that might also have an account in AD.
To test for this we take their names and perform 3 common mutations on them.
1 | |
Using kerbrute we can now check which usernames exist on the machine by requesting a TGT. This reveals the naming scheme of the company firstname.lastname.
1 | |
This does however not get us onto the machine yet, so we go looking for more information on the web page. There we find a picture with a notepad on it.
Taking a closer look at the notpad we see a username an a password.
Testing this set of credentials using the earlier identified naming scheme using cme we are able to authenticate to AD and list shares on the machine.
1 | |
SPN crackable
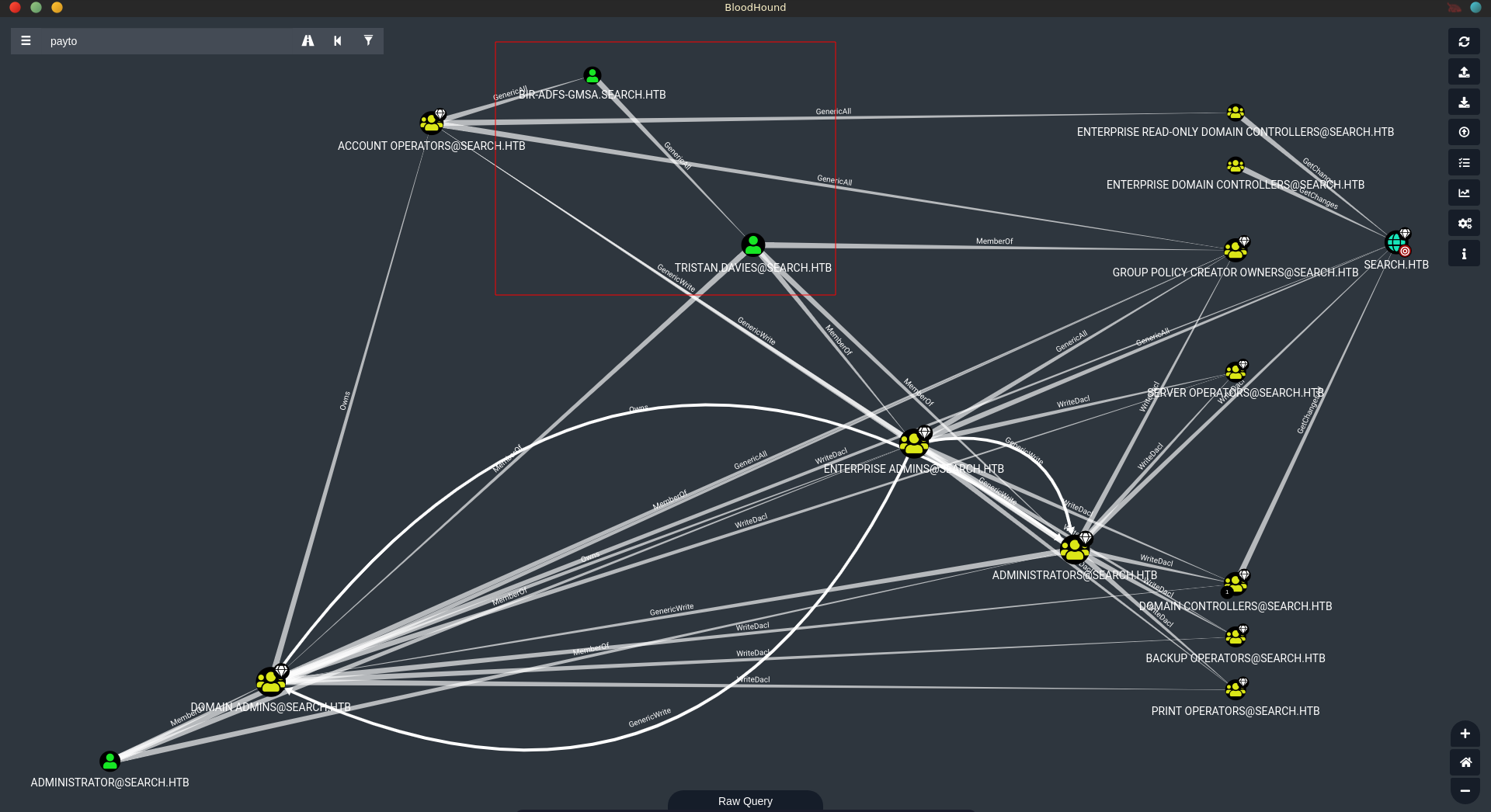
Since we are not being hunted and we got user credentials we can get a quick overview using bloodhound-python to dump active directory.
1 | |
Checking the common queries we see that web_svc has a SPN set.
Retrieving the ticket hash using impacket’s GetUserSPNs.py it cracks rather quickly.
1 | |
1 | |
Password reuse
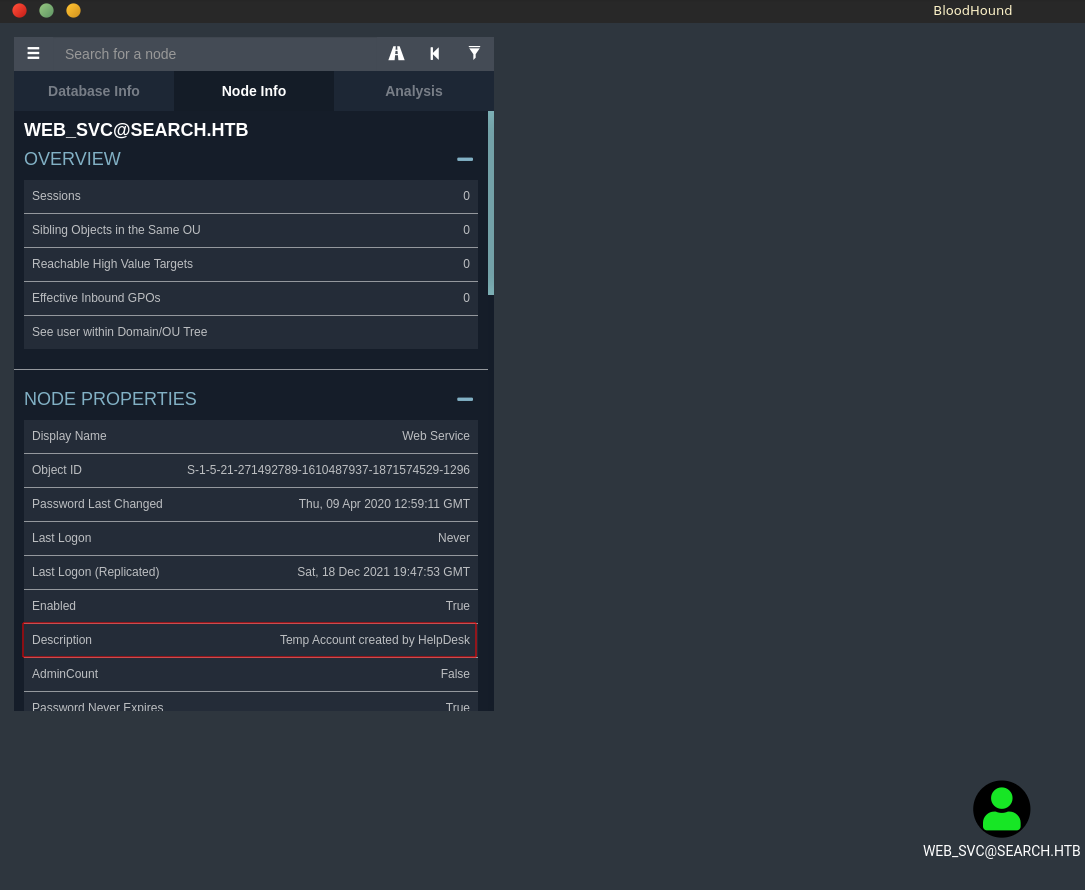
There is another interesting thing about web_svc, which is the account description. It mentions the account is a Temp Account created by HelpDesk.
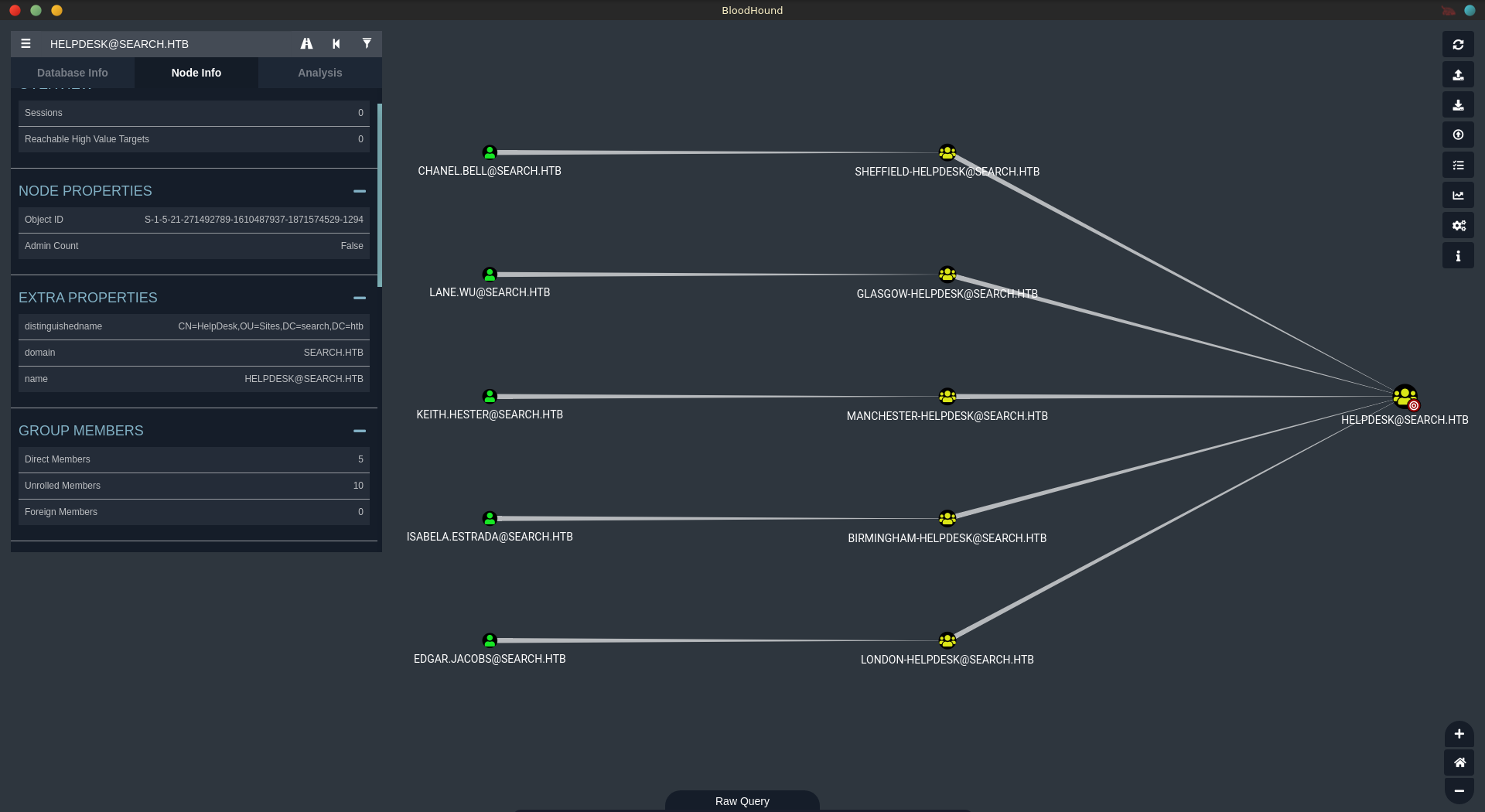
If we are lucky this might mean that the password is reused from a member of the HelpDesk group. We can get all the recursive group members using bloodhound.
Running cme against the list of usernames we can see that EDGAR.JACOBS probably reused his account password to create web_svc.
1 | |
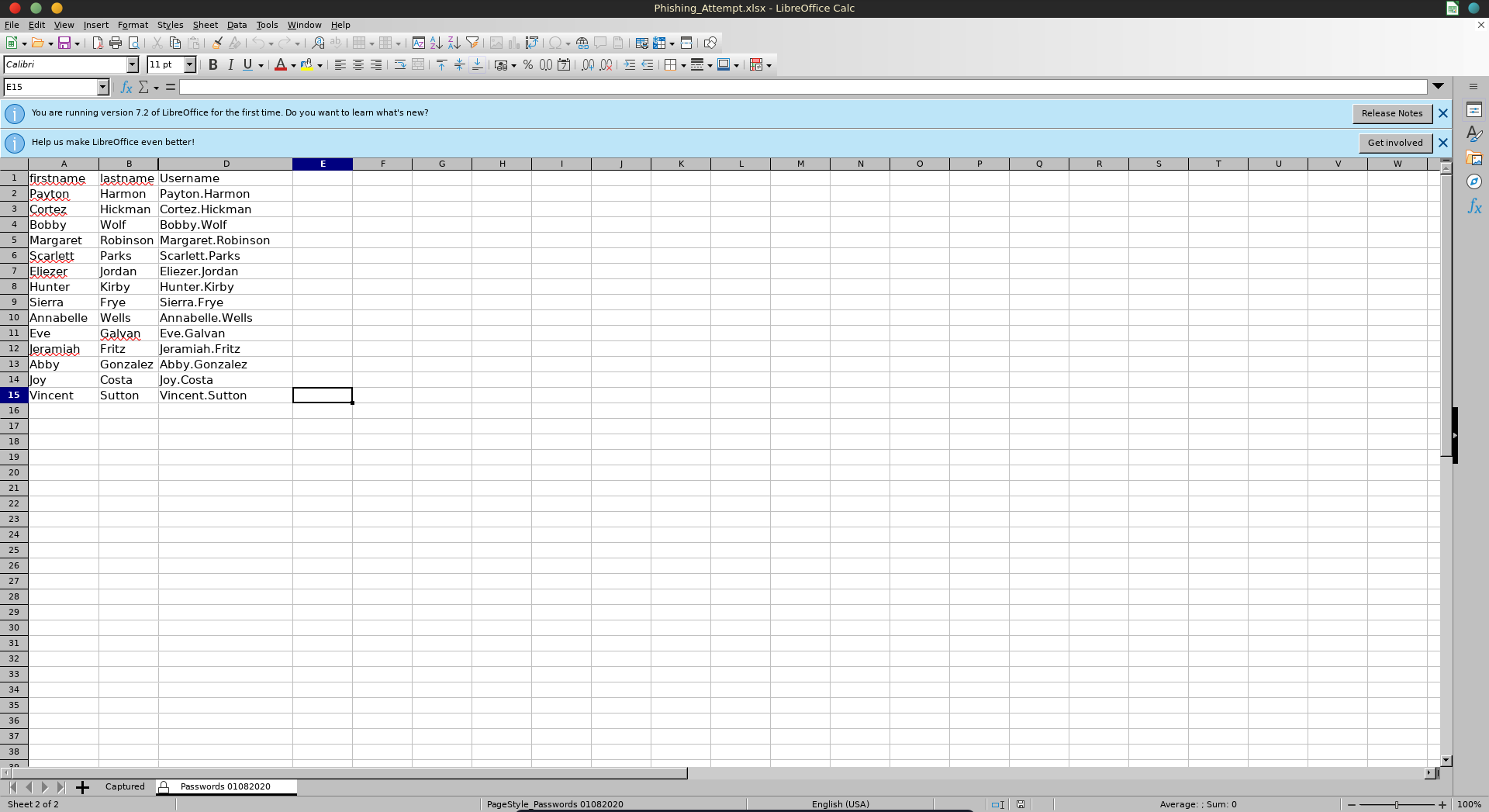
Checking the users home directory which is in the RedirectedFolders$ smb share we find an interesting looking excel file Phishing_Attempt.xlsx.
1 | |
Opening it the column C is missing.
Copying everything with CTRL + A => CTRL + C and pasting it into a new file we see the hidden column contained the password fo the usernames.
creds
1 | |
To find out which combination is valid we put the usernames and password and in seperate lists and use them with cme against smb.
1 | |
1 | |
This shows that the password for Sierra.Frye is valid. Checking her mounted home directory we are able to retrieve the user flag.
1 | |
1 | |
Root
To domain admin we will go over multiple ways with the first two of them probably being patched by now.
All the ways involve reading the gMSA password of BIR-ADFS-GMSA$ first as sierra.frye. This user has in turn GenericAll over Tristan.Davies who is in the EA/DA/A groups.
RSAT
One way to abuse this using the RSAT toolset on a windows machine. First we add the DNS entry for search.htb to our C:\Windows\System32\drivers\etc\hosts file.
Now we can create a netlogon sessions for sierra using runas.
1 | |
In this spawned powershell windows we are able to read the gMSA password for BIR-ADFS-GMSA$, impersonate the account and change the password for the user Tristan.Davies.
1 | |
Now we can spawn another powershell window with runas as tristan.
1 | |
In this console we can just psexec onto the machine and read the flag.
1 | |
Winrm
Another way to dump the gMSA password remotly is gMSADumper.
1 | |
This tool returns the rc4 hash of BIR-ADFS-GMSA$. This hash in turn can be used to PTH over WINRM. Now you could just quickly change the password for tristan.davies.
1 | |
With the password being changed you could enter another WINRM session as tristan and read the rootflag.
1 | |
Cert
The actually intended way involved finding the staff certificate in Sierra’s downloads folder on her home share. We found earlier that there is a /staff route on the webserver which returns a 403 error.
1 | |
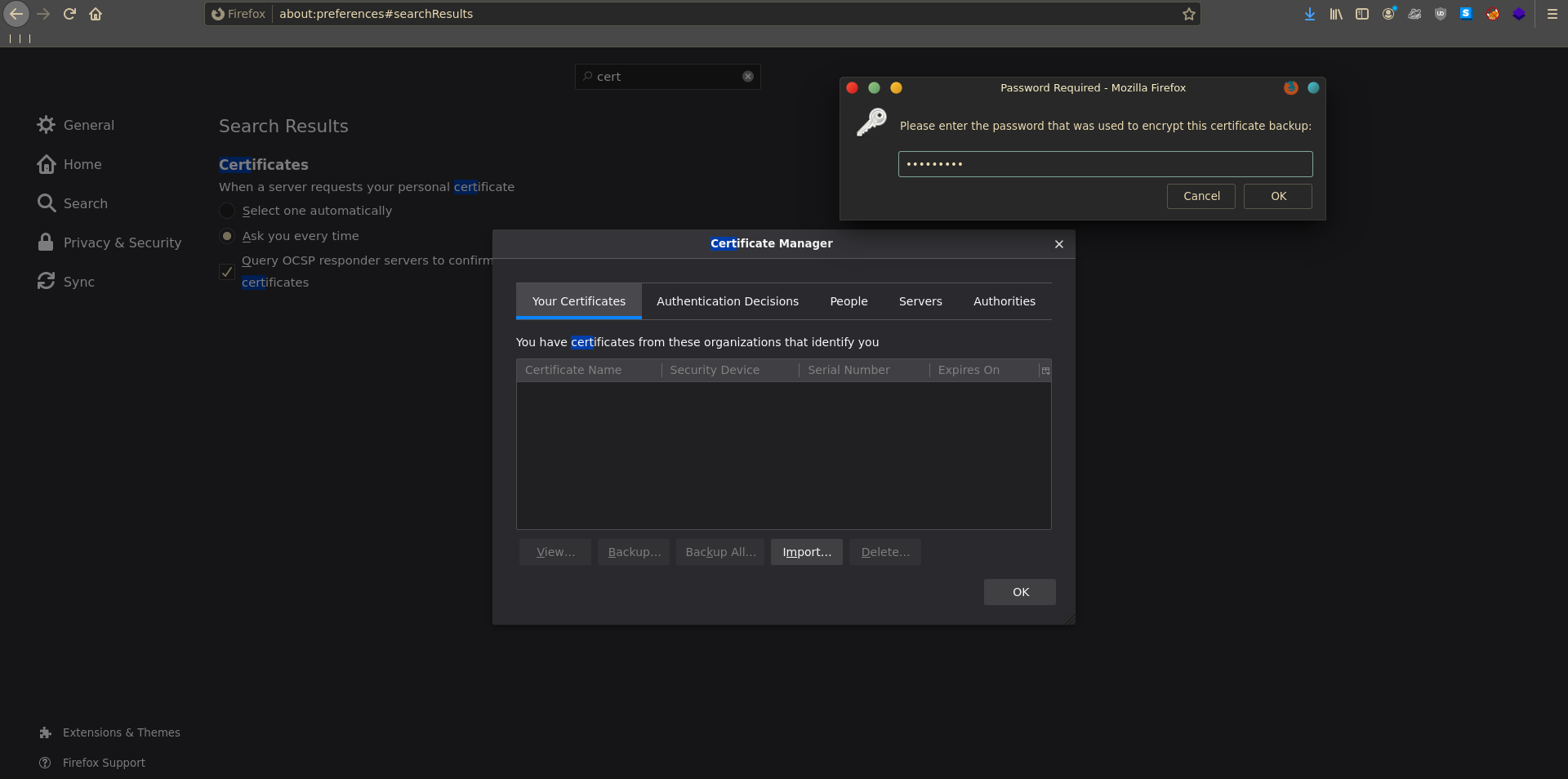
The certificate is password protectet. A quick way to get a crackable hash is pfx2john.py. The port of the script version from python2 to 3 was not fully done so there were python3 binary string specifiers still in the output. All that is needed to clean up is to remove the b'' parts.
1 | |
The cleaned hash cracks rather quickly using john with rockyou.
1 | |
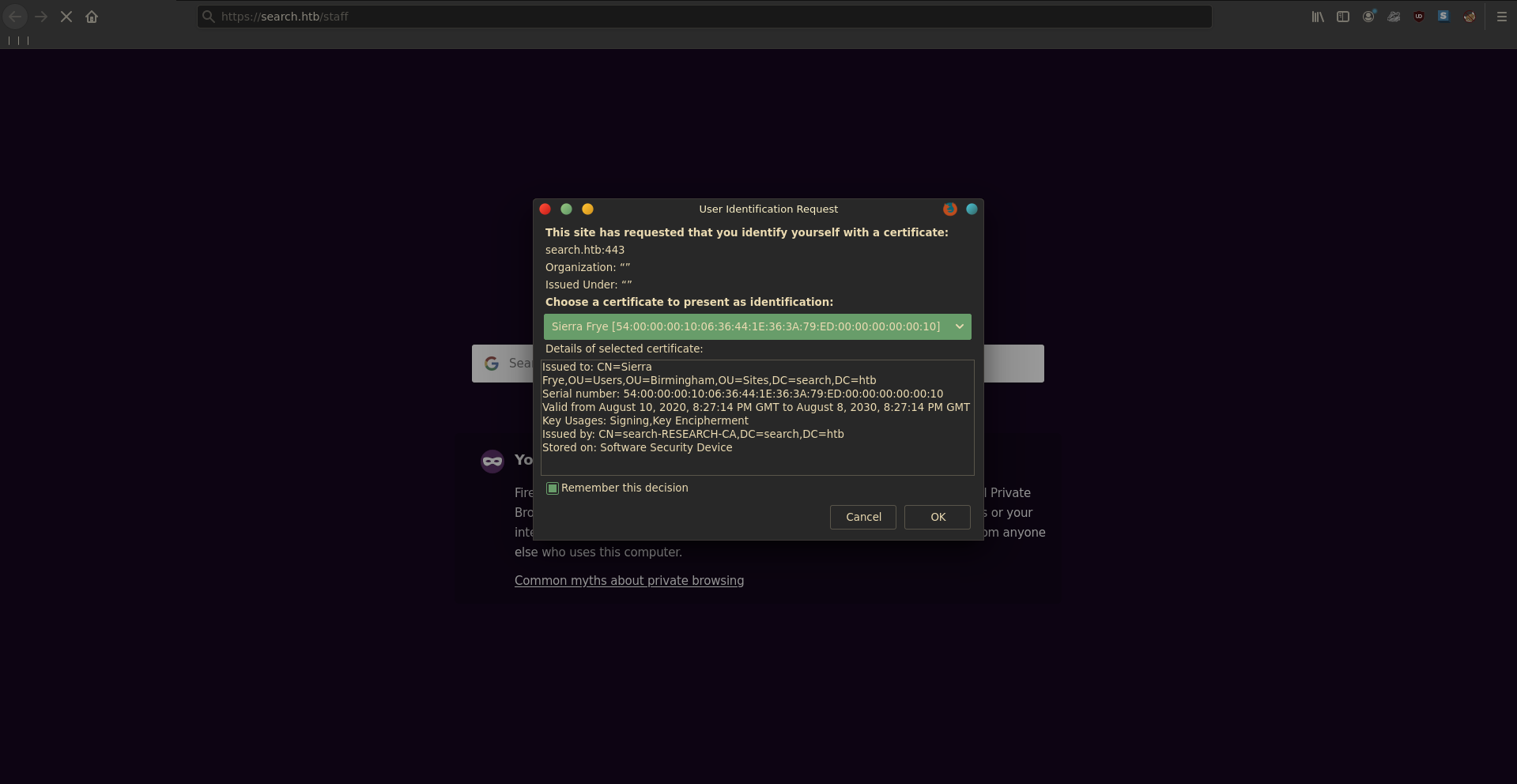
To use the certificate we first import it into our browser.
Browing to /staff now we are able to authenticate us as Sierra.
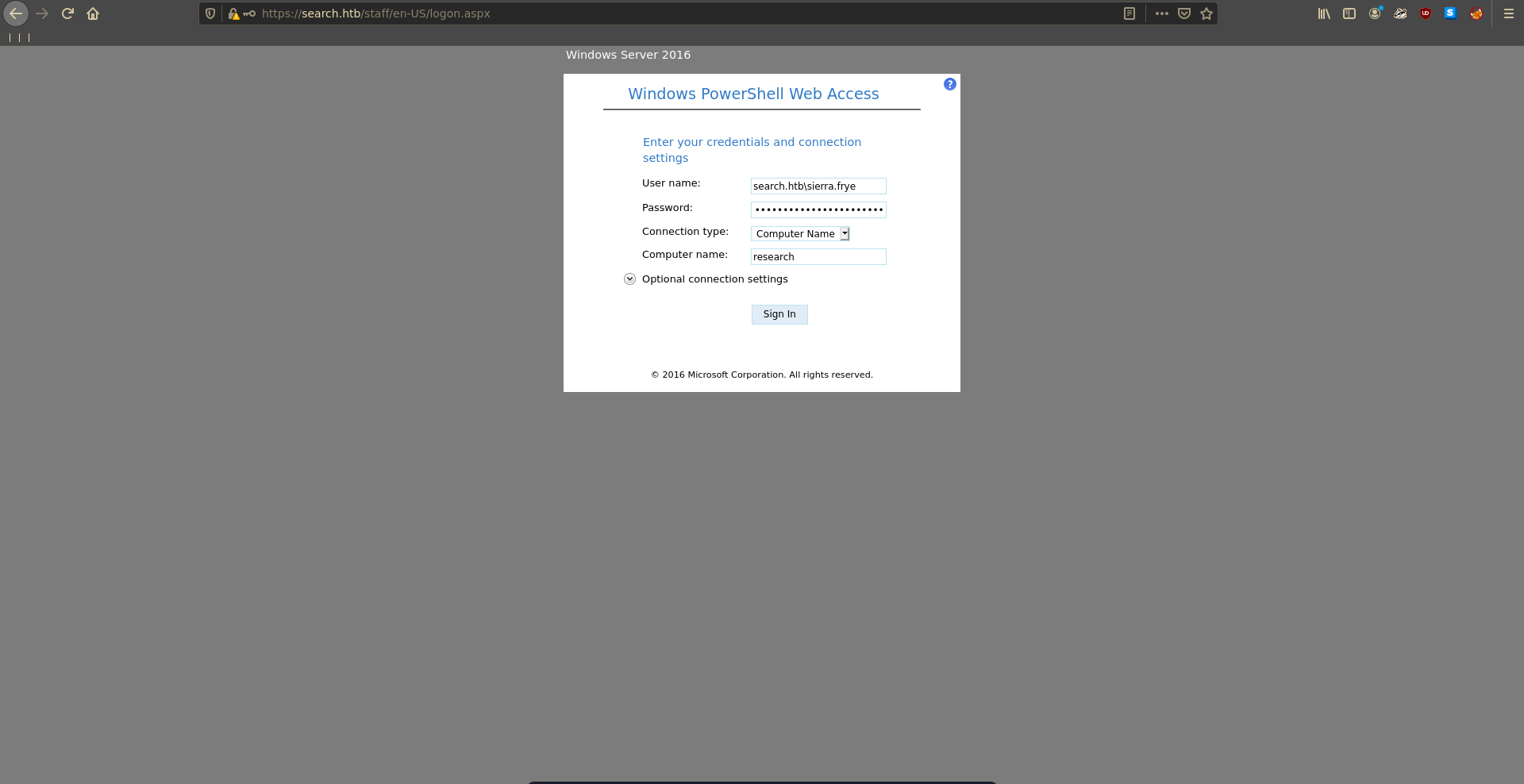
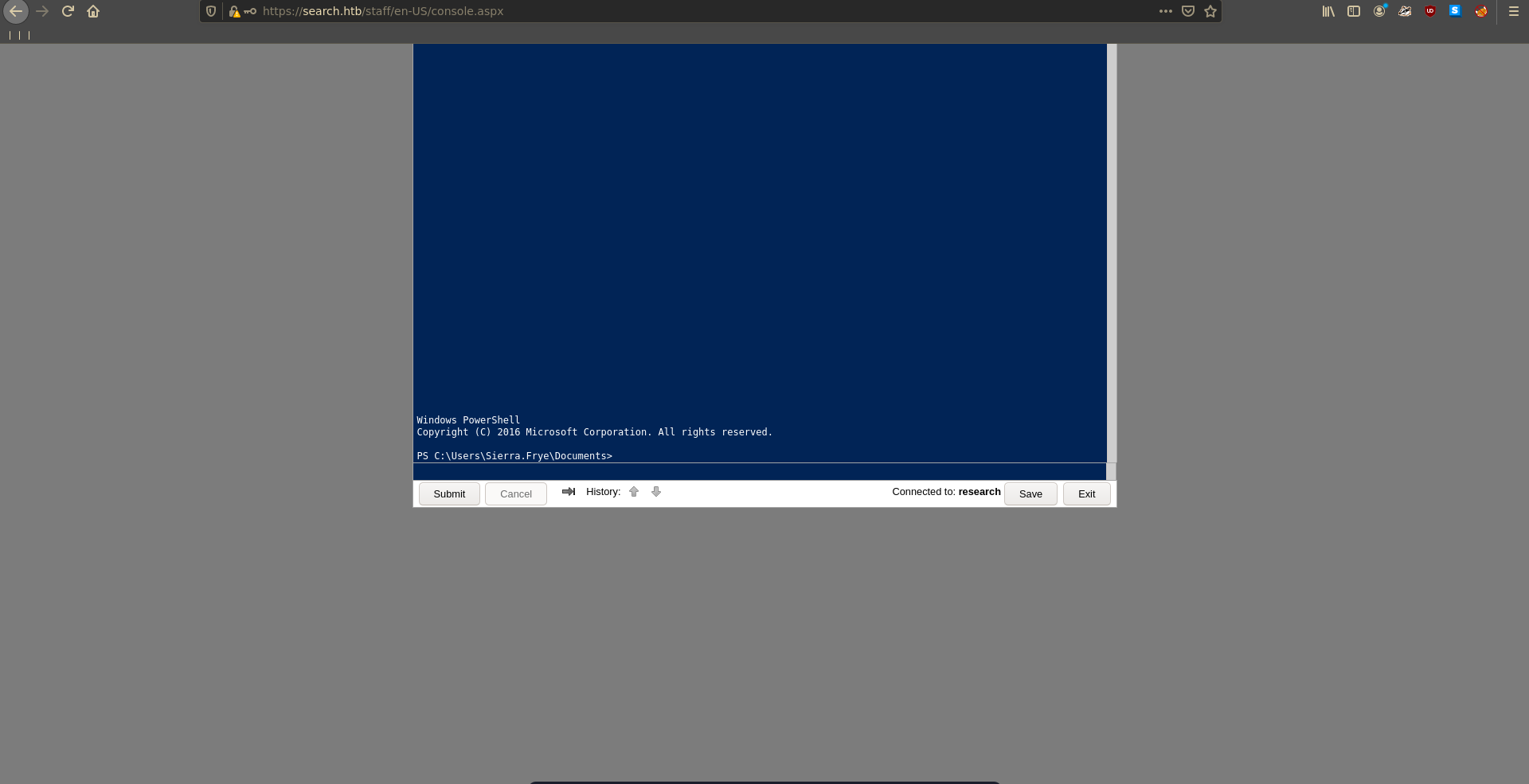
In the PowerShell Web Access login in we enter the credentials for Sierra.
Now we are able to issue commands remotly on the target.
The steps from here are pretty much the same as with RSAT. We first retrieve the gMSA password for BIR-ADFS-GMSA$.
1 | |
Next we impersonate BIR-ADFS-GMSA$ to change the password of tristan.davies
1 | |
Impersonating tristan we are now able to add the root flag to our collection.
1 | |