Driver is an easy rated machine on HackTheBox created by MrR3boot. For the user part we will phish a user with a UNC path pointing to our machine in a scf file we can upload, capturing his hash with responder. To obtain system we will abuse permissive ACLs on ricoh drivers and also obtain system with printer nightmare.
User
Nmap
As usual we start our enumeration of with a nmap scan against all ports followed by a script and version scan against the open ones to get an initial overview of the attack surface.
All ports
1 | |
Script and version
1 | |
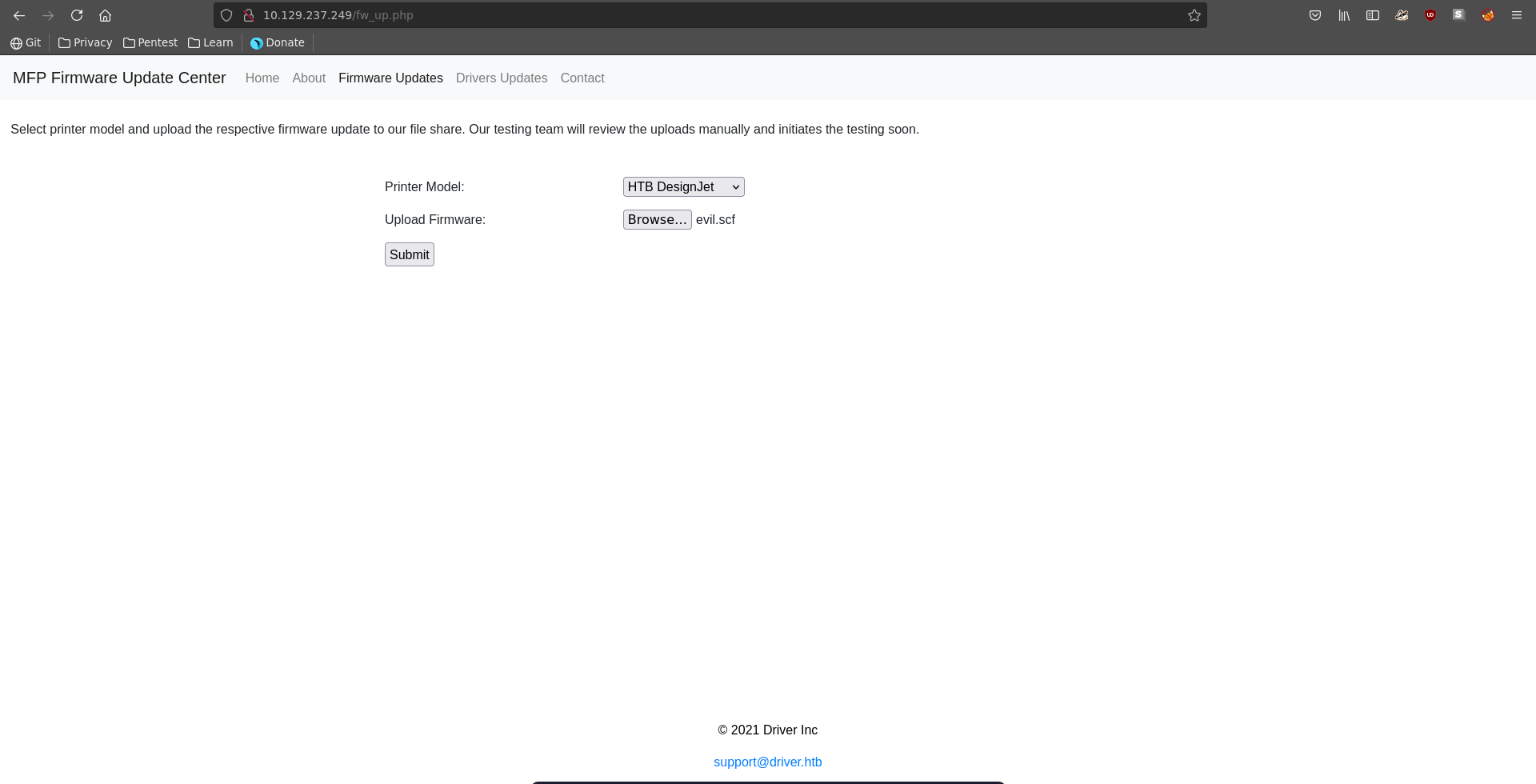
Firmware update
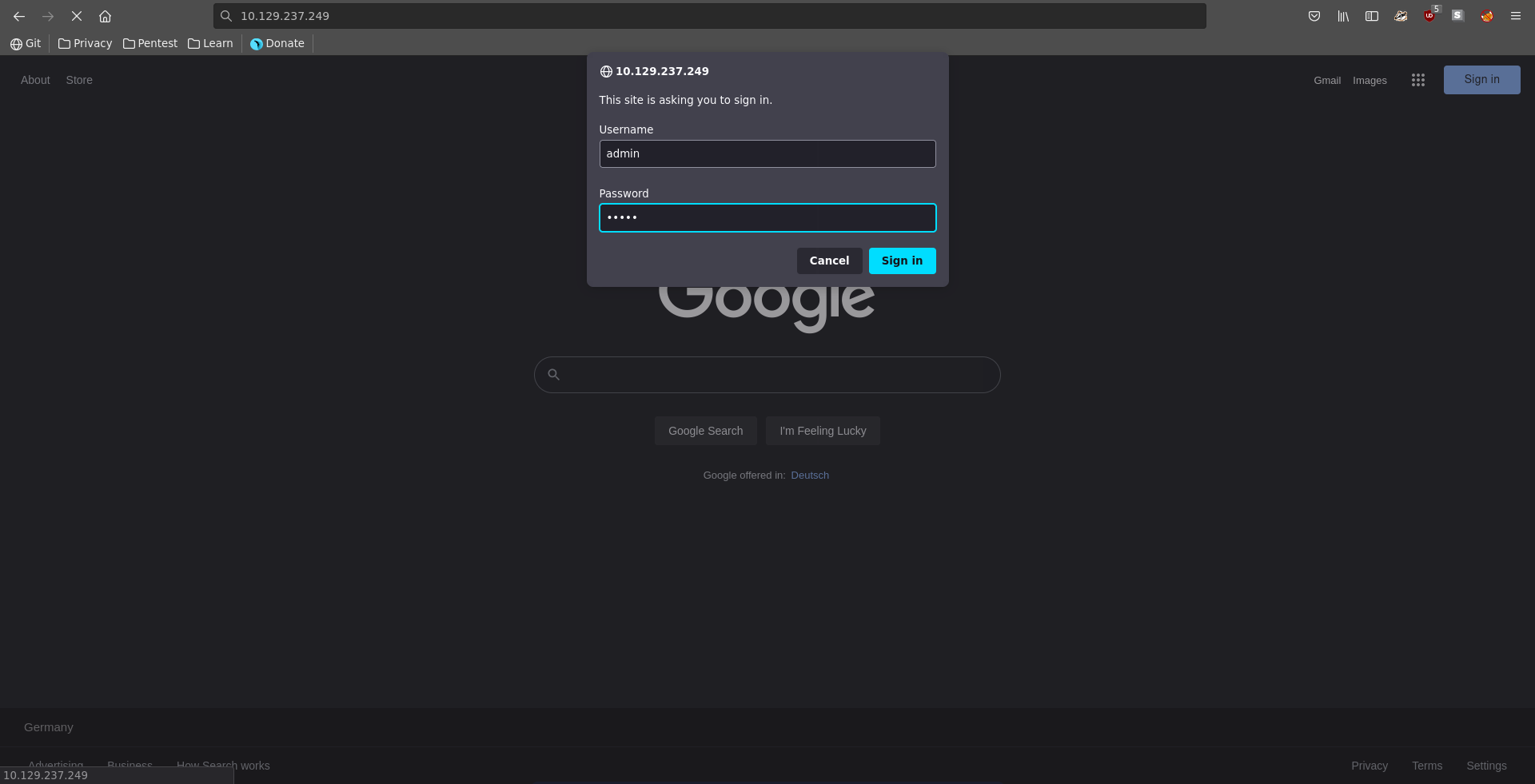
From the open ports port 80 seems to be the most promising. Opening the page in our browser HTTP basic authentication is enabled. We are however able to log in using the common credentials admin:admin
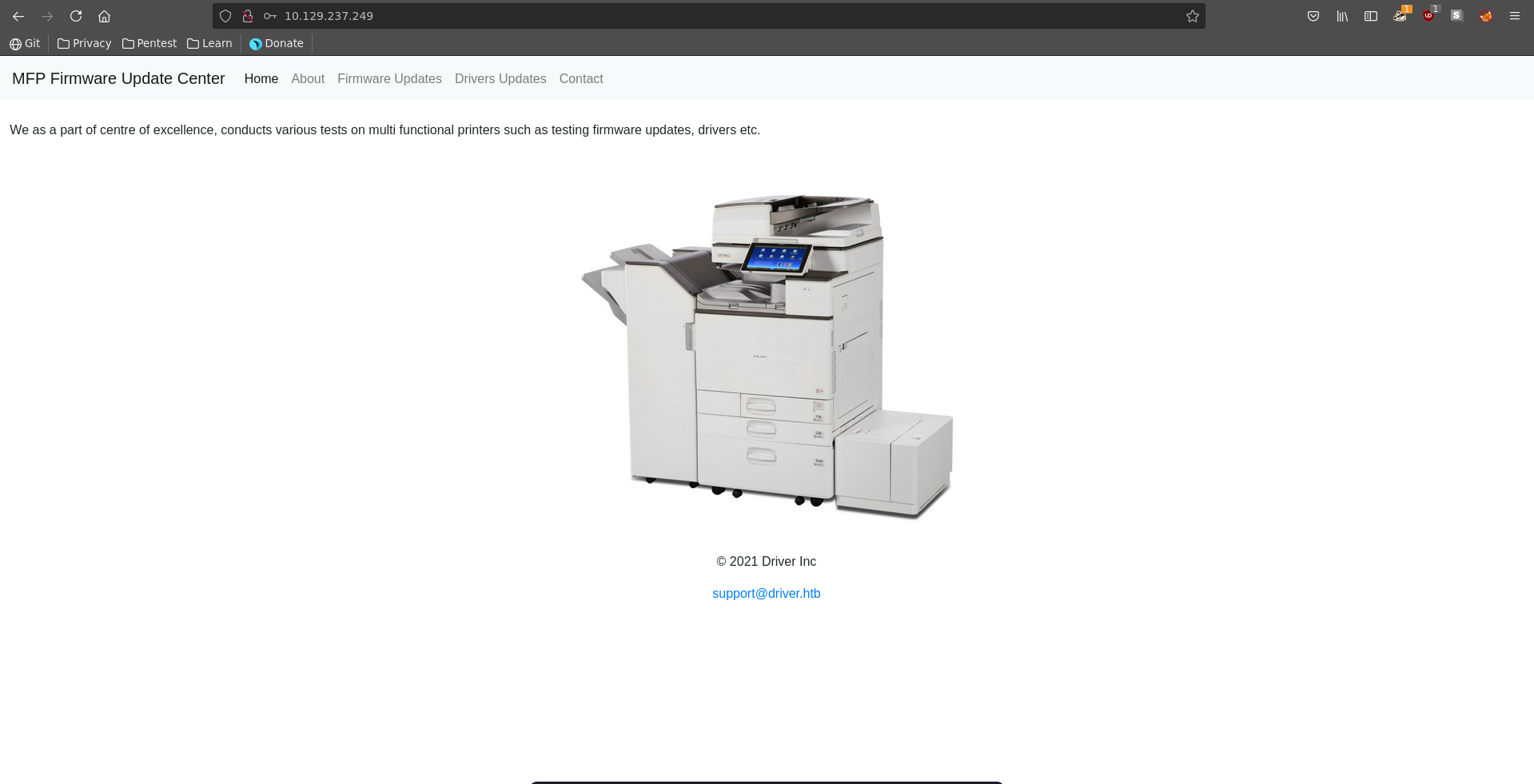
The page displays a printer firmware update center.
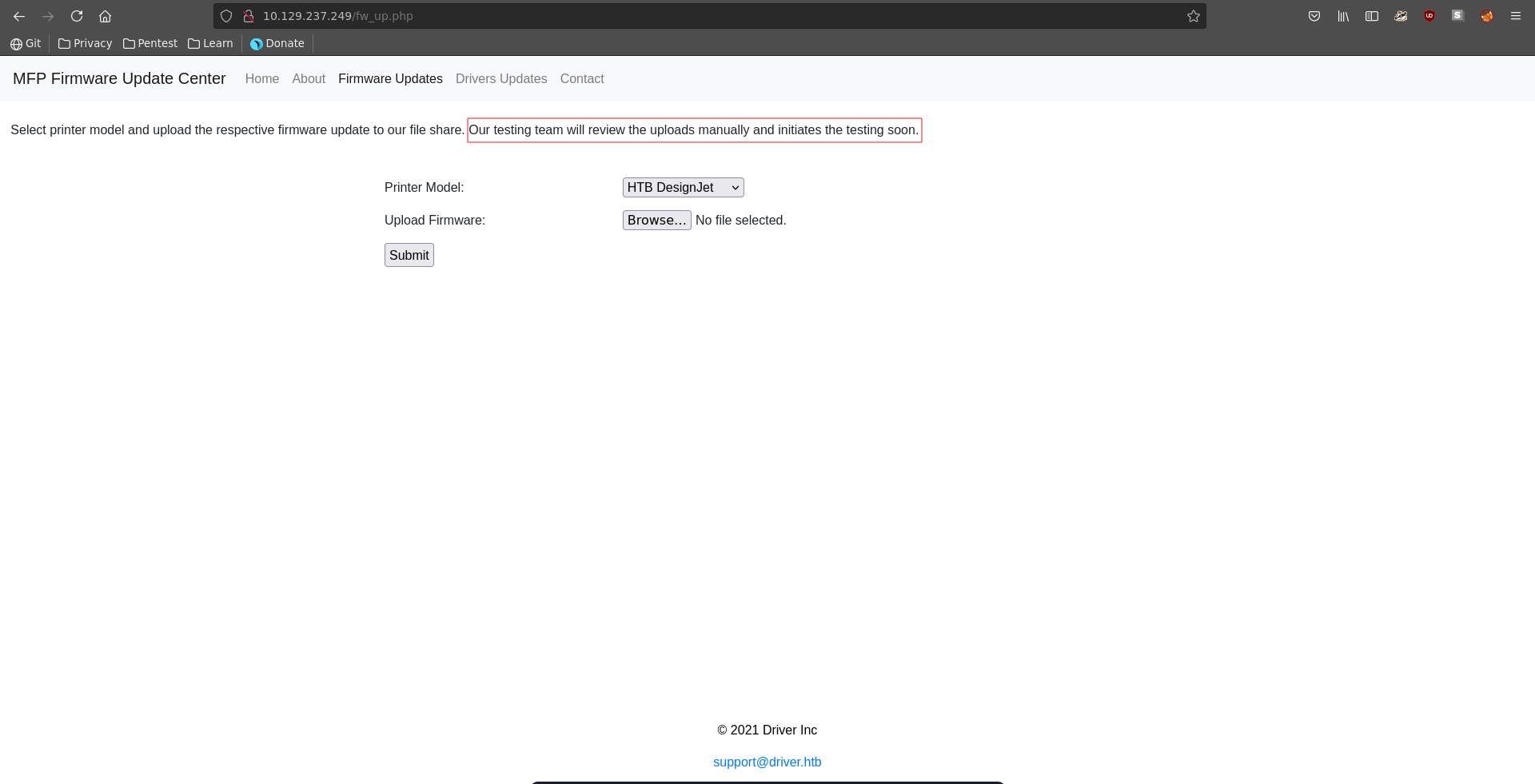
Going over to Firmware Updates we can upload files and it is stated that someone will manually look at those.
We are able to abuse this by uploading a scf file setting the icon to a UNC path pointing to our ip.
evil.scf
1 | |
Before uploading the file we start responder to intercept incoming NTLM authentications.
1 | |
After uploading our scf we get a connection by tony and capture a NetNTLMv2 authentication hash.
1 | |
This hash cracks rather quickly using hashcat leaving us with the credentials tony:liltony
1 | |
We can now log into the machine on the open winrm port and grab the user flag.
1 | |
Root
To get system we will dive into two possible paths and start with the ricoh driver vulnerability.
Ricoh driver
Looking at the files in C:\ProgramData we see an unusual RICOH_DRV folder.
1 | |
Checking the acl of the dll’s in this directory we can see that everyone as has full control of them.
1 | |
Look for vulnerabilities in ricoh printer software we find this exploit code on exploit-db. This abuses the overly permissive ACL on the dll’s, replaces and loads one of them as system when creating a new printer. To abuse it we first generate a meterpreter executable with msfvenom.
1 | |
We start a handler in the background with the payload we generated, the ip and the lport.
1 | |
Next we upload the meterpreter to the machine using evil-winrm and execute it.
1 | |
The exploit doesn’t seem to work well in the initial session but migrating solves the problem. I couldn’t figure out why this is the case. If someone knows the reason feel free to reach out to me. We interact with the openend meterpreter session, list the running processes and migrate to another one.
1 | |
Now we background the meterpreter with bg and use the meterpreter module to abuse ricoh driver. We set the payload to a staged x64 meterpreter set the lhost, session and run the exploit. Upon finishing another meterpreter session as system returns.
1 | |
Now we can add the root flag to our collection.
1 | |
Printer nightmare
Another possibility to obtain system was to abuse printer nightmare. We will use the PoC by cube0x0 for this.
In addition to the install instruction of the readme we create a python virtual enviroment to not clobber our existing impacket installtion.
1 | |
Next we need to generate a malicious dll which we will load with system privileges later. We will use msfvemon in this case.
1 | |
We upload the dll to the machine and start a handler to catch the meterpreter specifiying the same parameters as in msfvenom.
1 | |
1 | |
Running the exploit with the gathered credentials for tony results in another meterpreter session as system.
1 | |
1 | |
We can now simply interact with the session and read the root flag.
1 | |