Pivotapi is an insane rated machine on HackTheBox created by CyberVaca and 3v4Si0N. For the user part we will identify a username in the metadata of a PDF we download from an ftp share. This user has no preauth with kerberos set so we can request a TGT for him which we manage to crack with hashcat. With the new credentials we can log into SMB where an exe is stored which hands us credentials for mssql after some debugging and reversing. With these credentials we discover a keepass database on the machine and exploit a few misconfigurations in Active Directory until we obtain the local administrators password through LAPS and PSExec to SYSTEM. Furthermore we will also look at two unintended ways to get to SYSTEM from mssql, one of them being still unpatched.
User
Nmap
As always we start our enumeration of with a nmap scan against all ports, followed by a script and version detection scans against the open ones to get a initial view on the attack surface.
All ports
1 |
|
Script and version
1 |
|
FTP
The target seems to be a domain controller with a lot of ports open, however there is no webserver running. The lowest hanging fruit seems to be the FTP server with anonymous login enabled.
We can use wget with anonymous login and the -m flag to mirror all the files to our machine
1 |
|
Looking at the files they hint at a windows buffer overflow, which is however a rabbit hole.
1 |
|
Checking the metadata of the PDF files with exiftool we can find something interesting in notes2.pdf. The author of the PDF is Kaorz and the publisher is LicorDeBellota.htb which is also the domain name of the machine.
1 |
|
Kerberos preauth
Since kerberos is installed and activated on the machine we can test if this user has pre authentication set. Using impackets GetNPUsers.py we see that this is not the case and we can retrieve a TGT for the user Kaorz in hashcat format.
1 |
|
We can crack the ticket quite quickly with hashcat mode 18200 and retrieve the password Roper4155.
1 |
|
With this credentials we can now list shares on the target with smbclient.
1 |
|
Going over to the NETLOGON share we see a HelpDesk folder which we can download to our local machine.
1 |
|
1 |
|
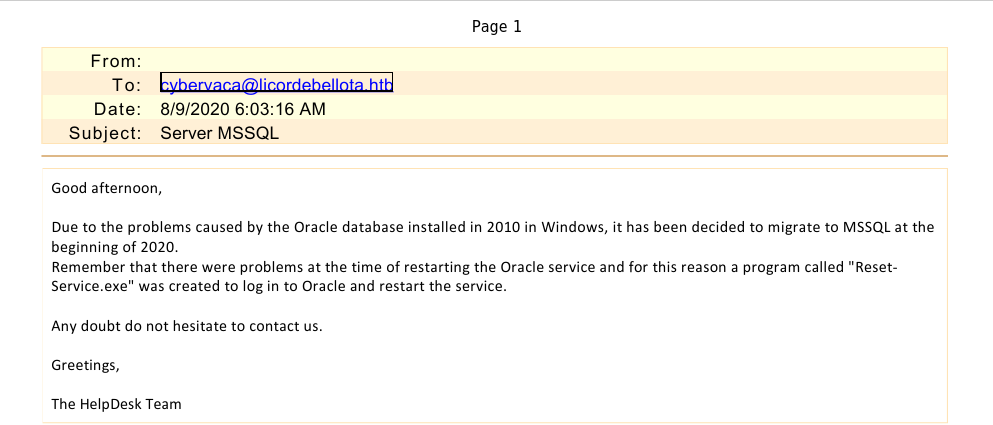
We cannot read the 2 .msg files right away but we can convert it with either outlook, cli-tools or an online converter to a readable format. Uploading them to zamzar and converting them to PDF files we are now able to read them comfortably.
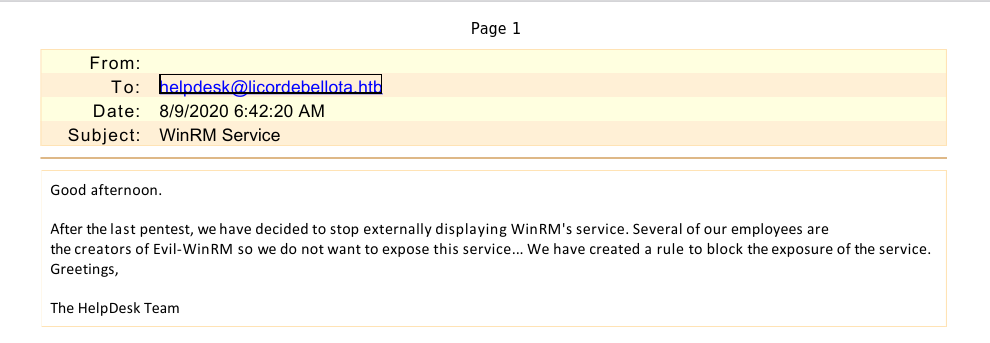
The second message hints at WinRM being disabled and is of no use just yet, but the other one states a migration from oracle to mssql lately and it mentions a Reset-Service.exe. This seems to be related to the Restart-OracleService.exe we downloaded from the smb share. For better analysis options we transfer the executable to a windows vm.
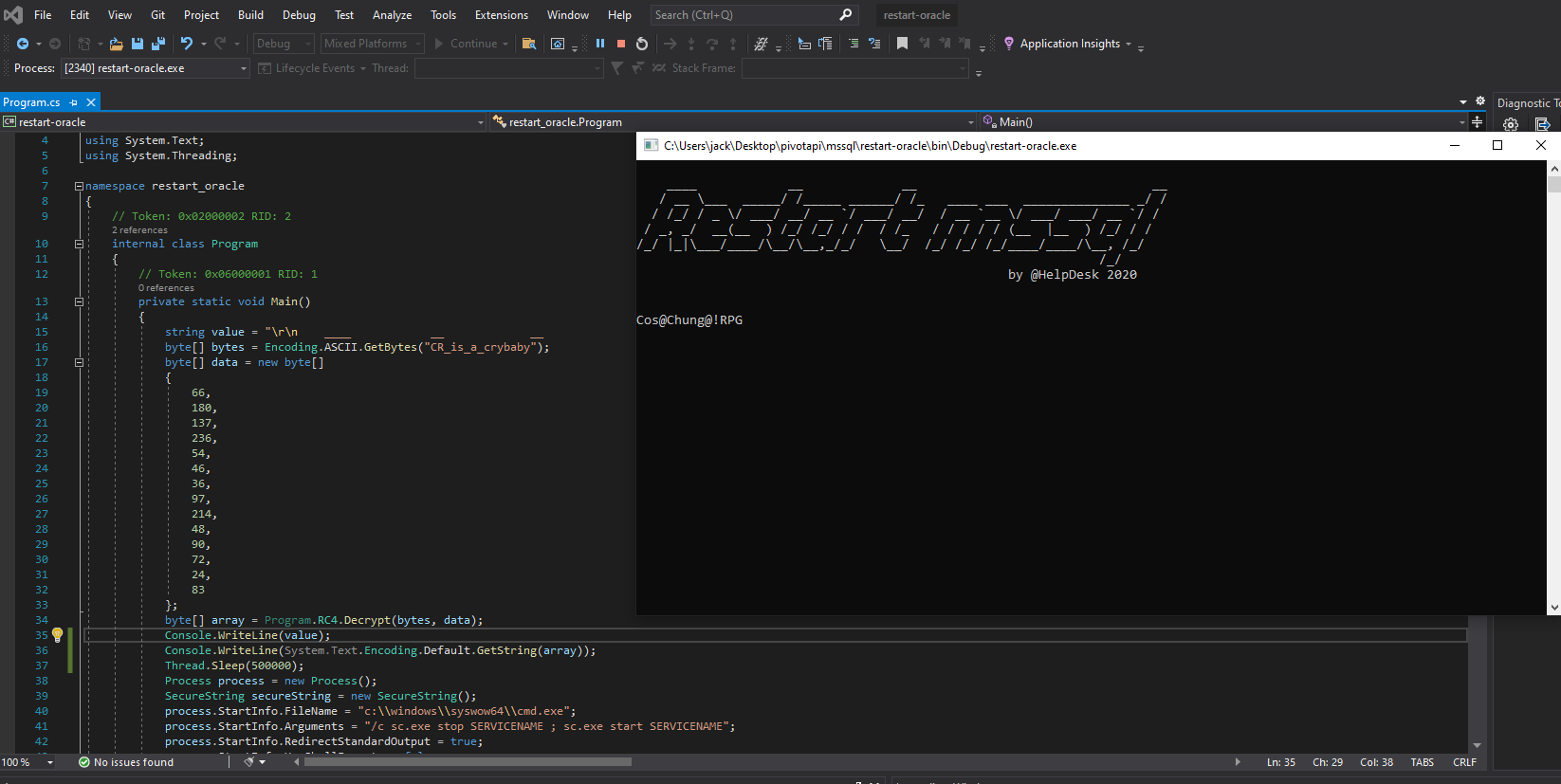
Restart-OracleService.exe
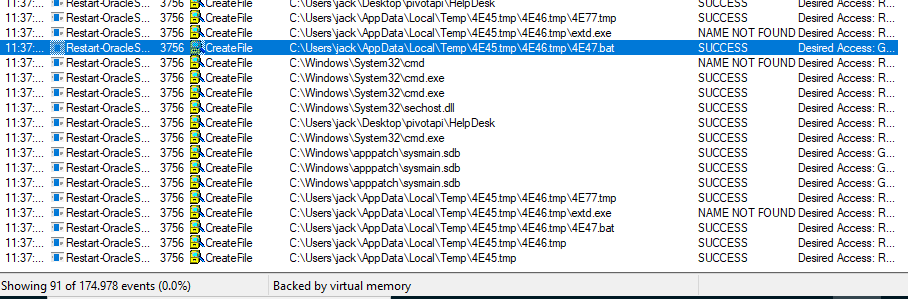
Monitoring with procmon64.exe from the sysinternals suite and running the binary we see it creates a temporary .bat, but trying to retrieve it afterwards, it is already deleted.
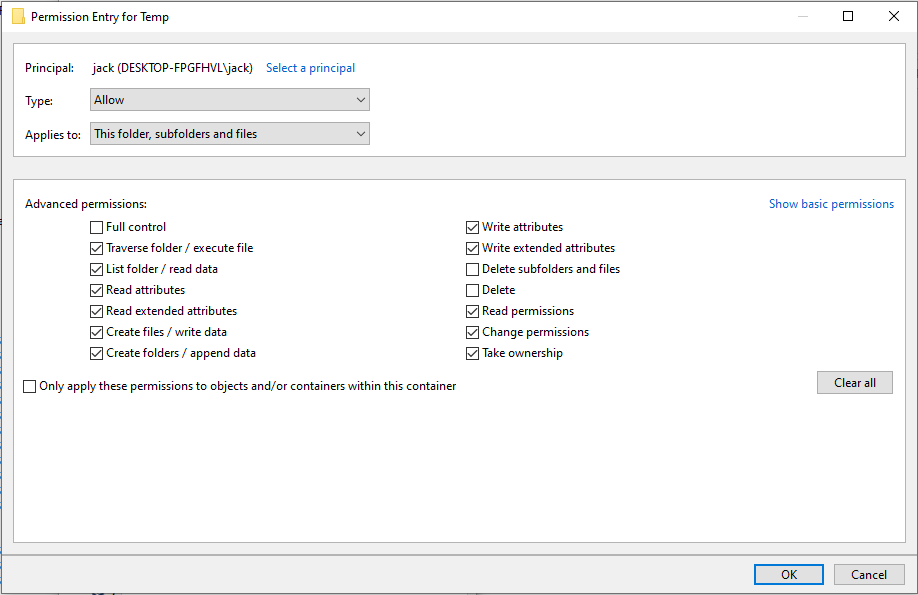
To retrieve the file we change the permission entries for the temp folder in advanced settings for the user the exe is running under. Here we untick the Delete subfolders and files and the Delete checkbox and apply the changes.
Now we run the programm again and this time the .bat does not get deleted.
We copy the file to another folder and restore the previously set permissions. Opening the file in notepad we see it wrtites a lot of BASE64 data to a file and converts it to the restart-service.exe. Removing everything but the base64 from the start and end we can extract all of the data to a file and then decode it in a second step to retrieve the binary.
1 |
|
Restart-Service.exe
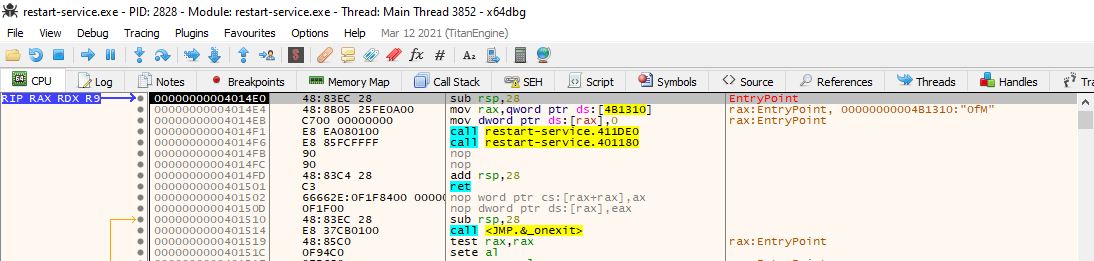
Running the binary it displays an ascii banner and exits. It is probably particularily interesting what happens around this time in the program, so we try to break as close as possbile to the banner getting displayed. Taking a closer look at it in x64dbg we can Execute till return in a first step until we hit a memory address ending in E0.
Next we Step over until the ascii banner gets displayed in the cmd window.
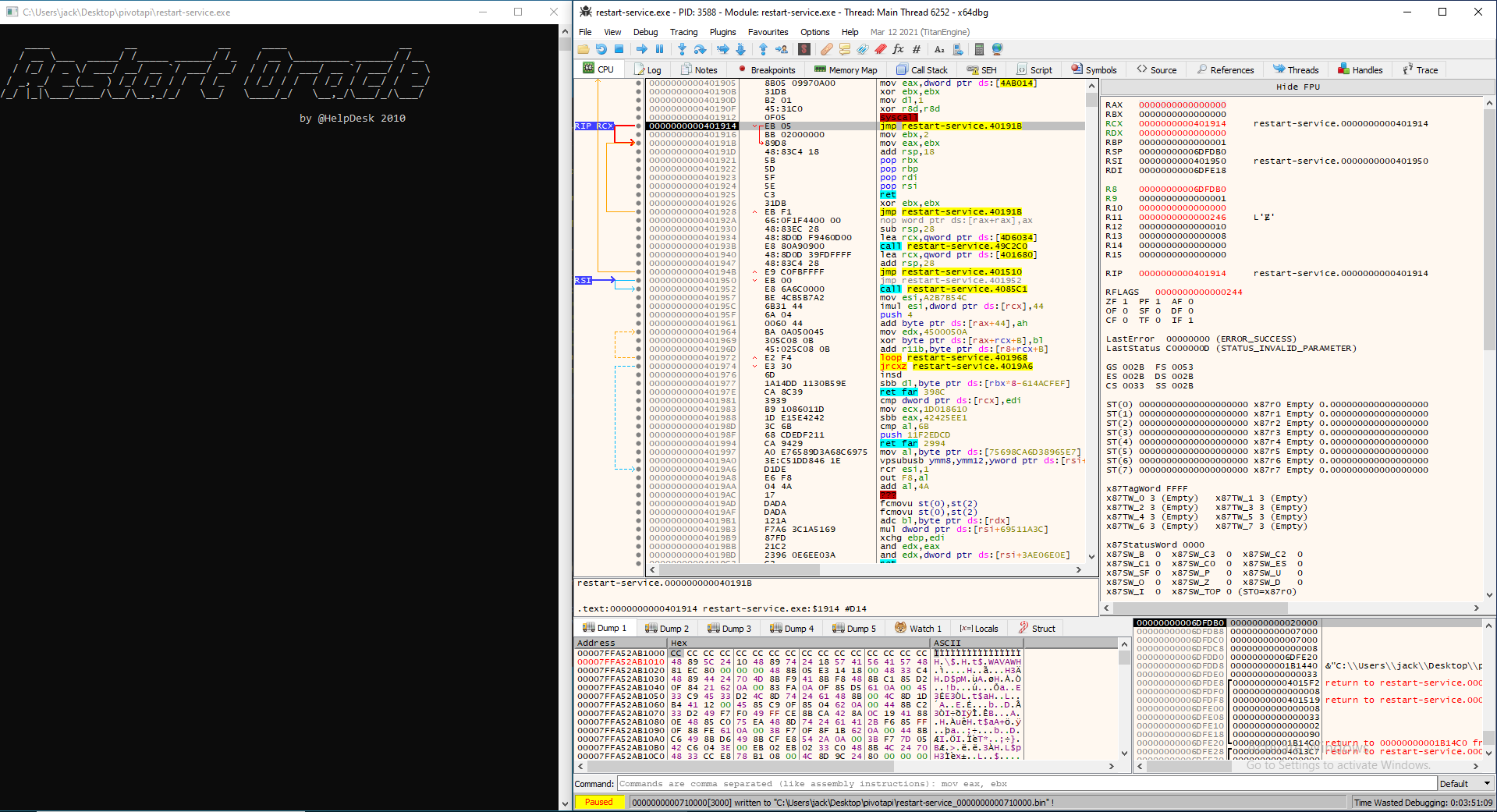
Going to the memory map we see something new mapped to the region right below the executable. Selecting Dump Memory to File we can dump the ram at this place to a file. The address is marked grey in the screenshot.
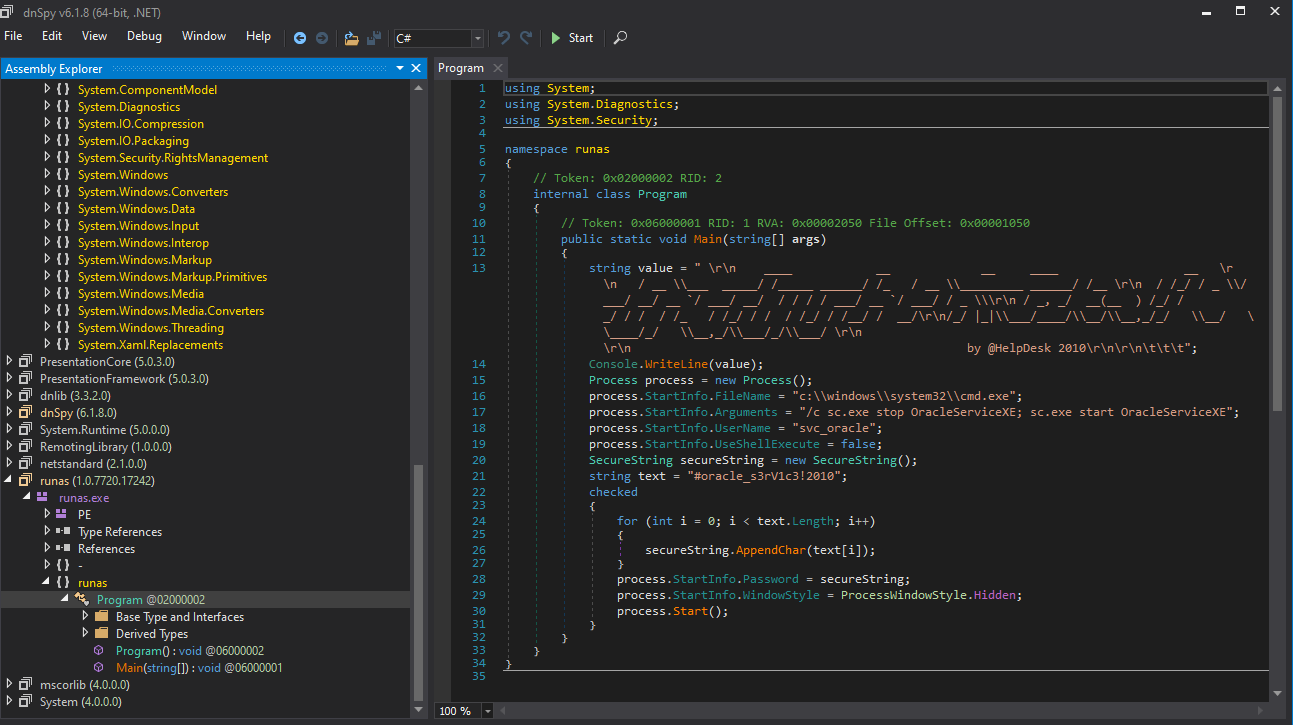
The extracted file is a .NET executable which means we can open it in dnSpy.
Doing so we can retrieve the username svc_oracle and the password #oracle_s3rV1c3!2010.
Checking the password against the default sysadmin mssql username sa we can find out it is a valid combination.
Keybase
With these credentials we can log into mssql using mssql_shell.py by alamot which also features a file upload capability. To make the script work with the current python version we have to exchange base64.encodestring for base64.b64encode.
mssql_shell.py
1 |
|
The current user cannot go into the home directories of users and the firewall rules are pretty strict, but the password is reused for the svc_mssql account. This means we can execute commands as this user using powershells Invoke-Command.
1 |
|
1 |
|
Looking around in the users home directory we find a credentials.kdbx on the desktop.
1 |
|
We want this database on our local machine for further inspection. To do this we first convert it to base64 with certutil.
1 |
|
Now we can simply cat the file to stdout and copy it over to our machine.
1 |
|
After converting the file back from base64 and verifying it’s integrity we can open it with kpcli.
The keepass databass is protected with a password but we can convert it to a hash john can deal with and crack it easily.
1 |
|
We now can use the password mahalkita to open the database and search for credentials.
1 |
|
Looking around we find the SSH credentials for the user 3v4Si0N.
1 |
|
Using this credentials we can now finally ssh into the machine and grab the user flag.
1 |
|
1 |
|
System
3v4Si0N => Dr.Zaiuss
Since our target is a domain controller we might be able to escalate our privileges abusing missconfigurations inside Active Directory. To collect information about it we upload sharphound with scp and run it.
1 |
|
1 |
|
This returns a zip with json files about the active directory structure which we import into bloodhound after transferring it back to us with scp.
1 |
|
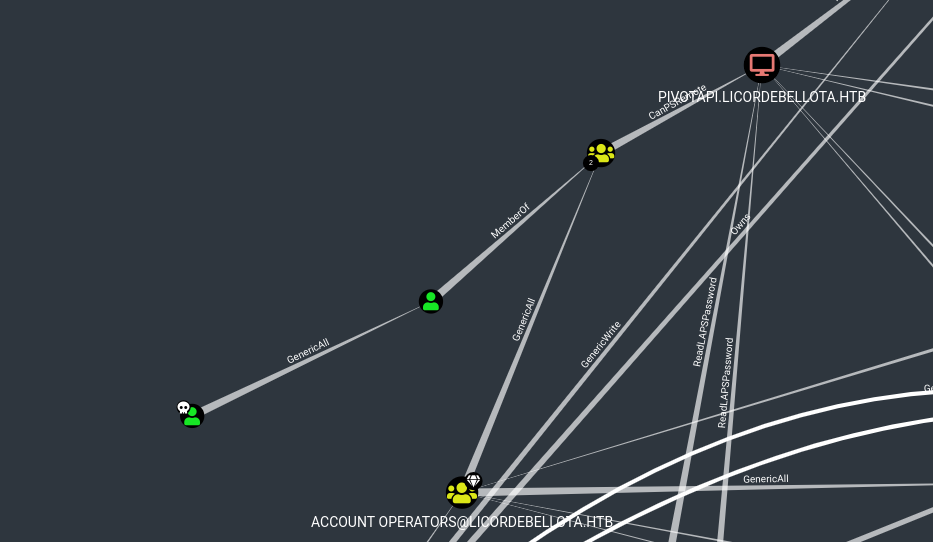
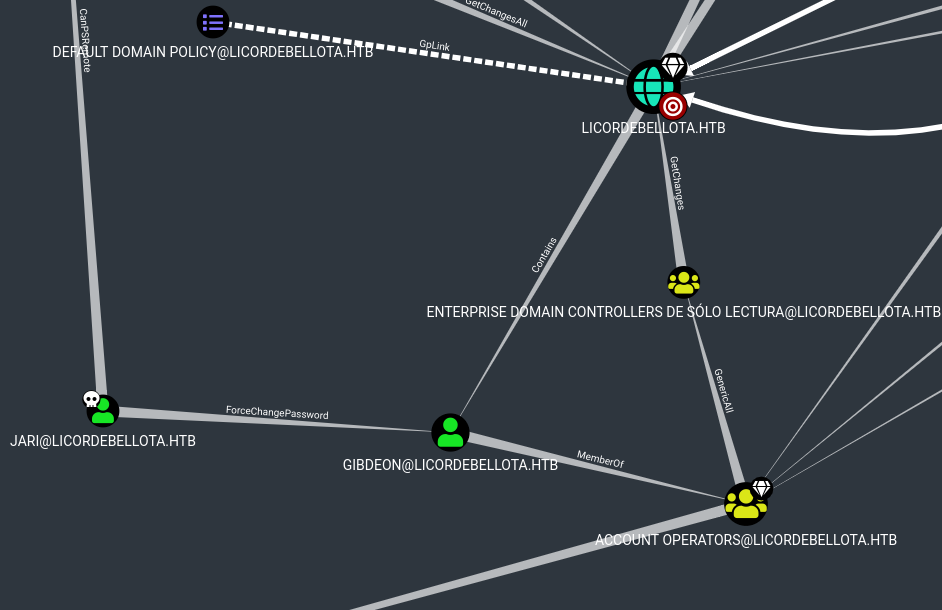
Looking at the output in bloodhound we can see that that 3v4Si0N has Generic All rights over Dr.Zaiuss which means we can do anything we want with this account.
We could change the password but it is less destructive to use PowerView’s functionalities to set the SPN of the user and retrieve a TGT for him. After we have retrieved the ticket we clear the set SPN of Dr.Zaiuss again to restore everything back to normal.
1 |
|
The hash cracks quite quickly with hashcat, giving us access to Dr.Zaiuss account.
1 |
|
Dr.Zaiuss => superfume
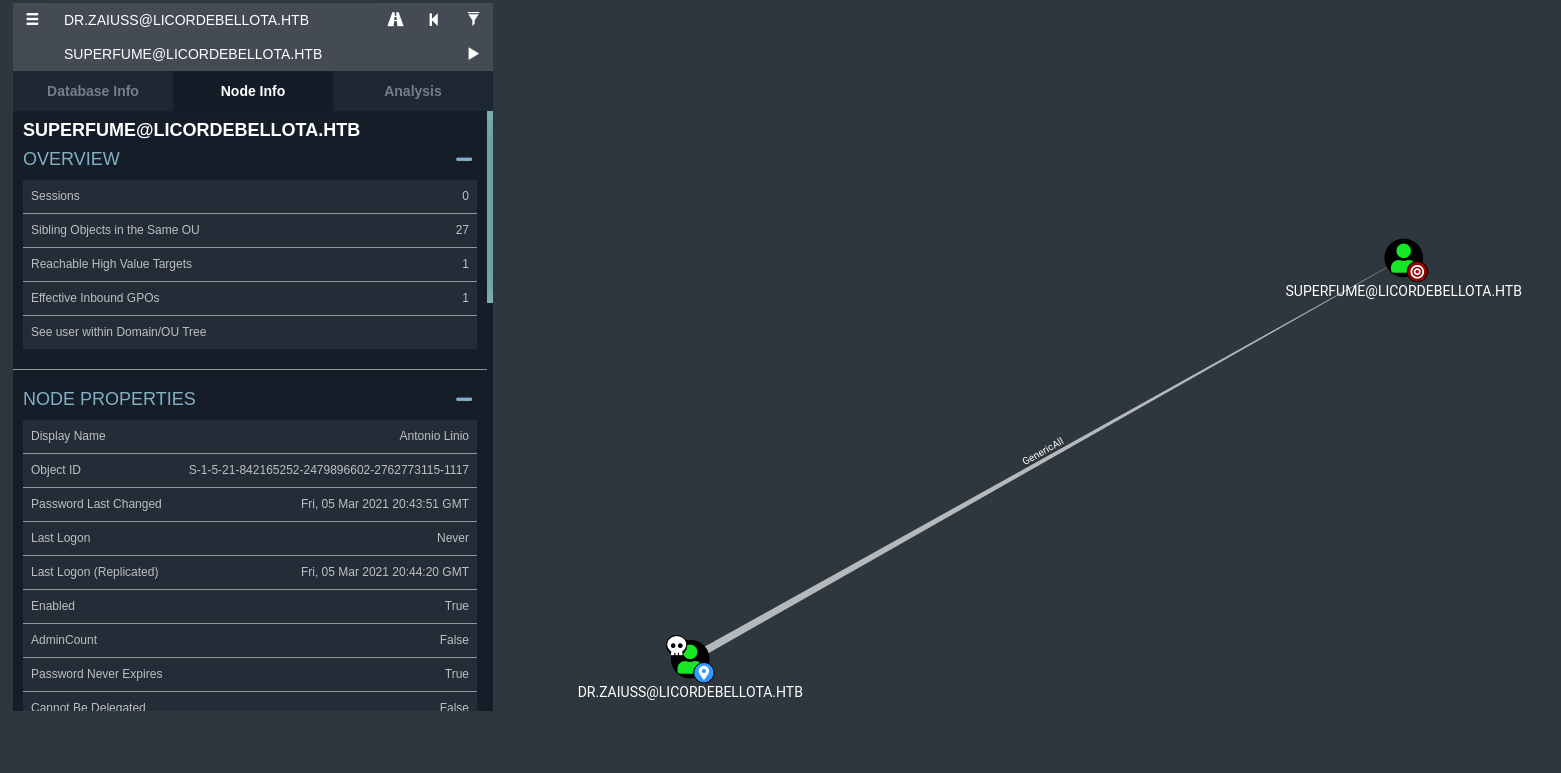
Checking bloodhound again for connections with our newly owned user, we see that he has Generic All over the user superfume.
To exploit this we perform the same steps as before with setting a credential object first to run the command as Dr.Zaiuss.
1 |
|
The hash cracks as quickly as the one before because the password was reused for superfume.
1 |
|
superfume => jari
Superfume is in the dev group and there is a devlopers folder in the file root. To take a closer look we first create and enter a powershell session as the user superfume.
1 |
|
There is indeed an interesting exe in jari’s folder under developers, so we download it to our machine again using scp after copying it to a place 3v4Si0N can reach.
1 |
|
Running file on it reveals it is a .NET binary, which means we can easily reverse it in DnSpy again.
1 |
|
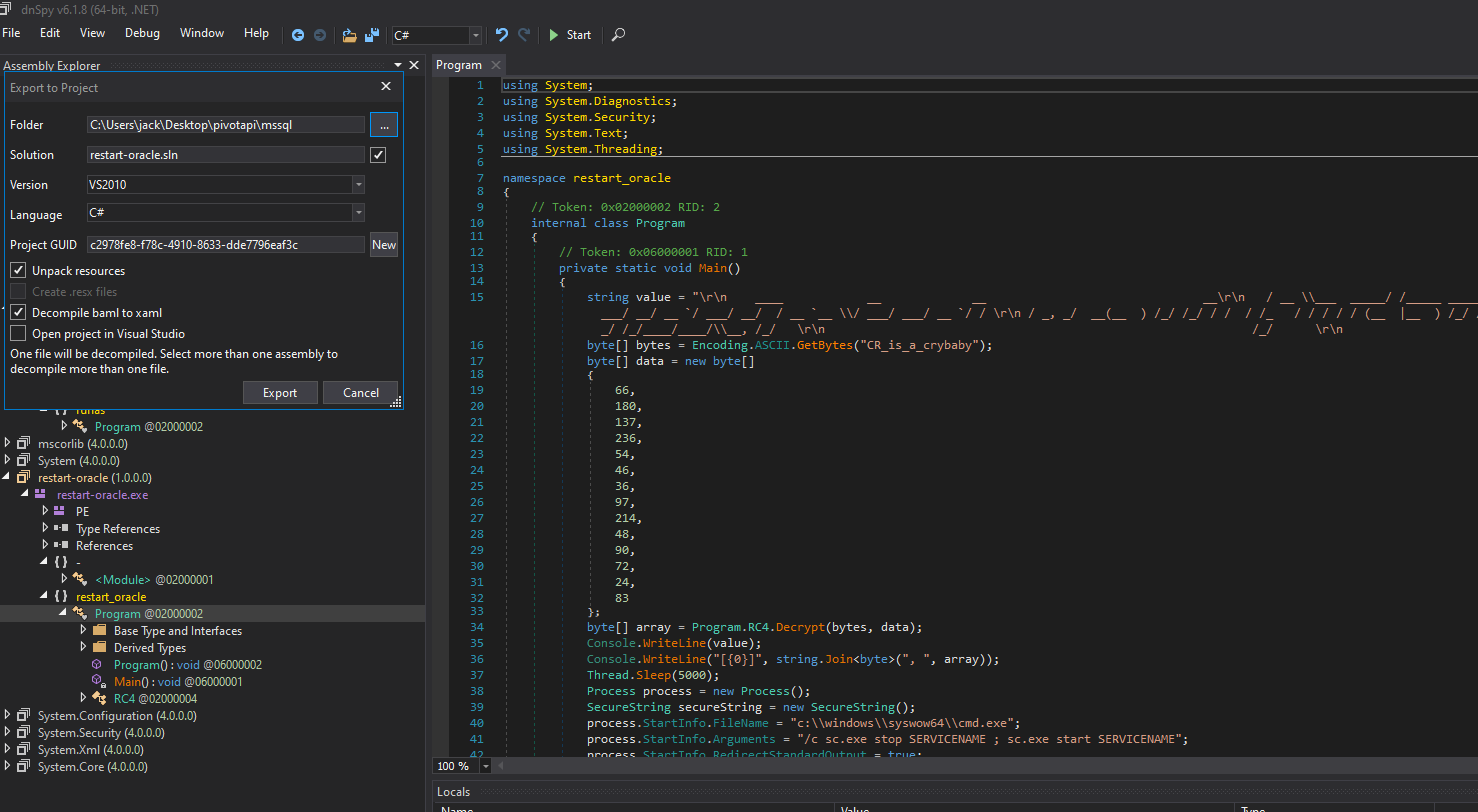
Examining it in DnSpy we see it takes a hardcoded string and a byte array to generate a password. To easier debug and change it we use DnSpy’s export function to continue in Virtual Studio.
The easiest way to get the password is to add an additional line to print it after or before it prints the banner and increase the sleep time by a lot so the terminal windows doesn’t close.
1 |
|
Running the project inside VS we see tha password printed out in cleartext to a terminal window.
Since the exe was in Jari’s folder, we assume it is his password and look again in bloodhound where we can go from Jari. Jari can force change the password for gibdeon and gibdeon is a member of the account operators group. This group has Generic All permissions over the laps read and laps adm, which means we can get the local administrators password if we are a member of it and LAPS is active on the machine.
Jari => gibdeon => SYSTEM
In a first step we force the password change on gibdeon using PowerView again.
1 |
|
Then as gibdeon we add ourselves to the laps read and laps adm group.
1 |
|
With preparations met we can now use LAPSDumper to retrieve the local administrators password in cleartext.
1 |
|
With this password we can now PSExec into the machine and grab the root flag.
1 |
|
1 |
|
Unintended
There are two unintended Methods on this machine to go directly from MSSQL$SQLEXPRESS to SYSTEM with one being patched and the other one still working. We will start with the patched one and also cover the still working one.
Printspoofer
Until some time after release there was the possibilty to go directly to system abusing the printspooler service.
Being connected we first check the privileges for the, MSSQL account since it should have the SeImpersonatePrivilege. The check returns that this privilege is indeed present so we should be able to get a system token using printspoofer.
1 |
|
We first upload printspoofer to the target using the UPLOAD function of mssql_shell.py.
1 |
|
In a first test we can see that we indeed sucessfully impersonate the local machine account.
1 |
|
We can now already read both the flags on the machine in 3v4SiON’s and cybervaca’s desktops.
1 |
|
To get a real shell on the target we can upload mimikatz to the machine and dump the hashes from the domain controller.
1 |
|
1 |
|
With impackets PSExec using the administrator NTLM hash we can now get a shell on the target as nt authority\system .
1 |
|
TGT => DCSync => PSExec
Another alternative route to system from mssql, which was still working the last time i checked is to obtain the TGT from the MSSQL machine account, convert it to perform a DCSync attack and then PSExec into the machine as administrador.
In a first step we download, compile and upload rubeus to the target.
1 |
|
Then we use it to request a Ticket-Granting-Ticket for the service account. and save the base64 encoded ticket in a file.
1 |
|
Next we decode the ticket and convert it with impacket’s ticketConverter.py
1 |
|
1 |
|
We then export the ticket to our environment variables.
1 |
|
Having everything set up we can now perform a DCSync on the target with impacket’s secretsdump.py and extract all the hashes from the domain controller, specifying kerberos authentication and no password.
1 |
|
With the Administrador hash we can now PSExec into the machine and spawn a shell as nt authority\system.
1 |
|