User
Explore is an easy rated machine on HackTheBox by bertolis. For the user part we will exploit an open port for ES file explorer to retrieve ssh credentials in a jpg file. After this we will abuse adb being enabled and listening to get a shell as the root user after forwarding it to our machine.
Nmap
As always we start our enumeration off with a nmap scan against all ports, followed by a script and version detection scan against the open ones to get an overview of the initial attack surface.
All ports
1 | |
Script and version
1 | |
ES file explorer
Port 59777 on an android device is normally used for ES file explorer. Opening the port in our webbrowser we see that directory listing is disabled.
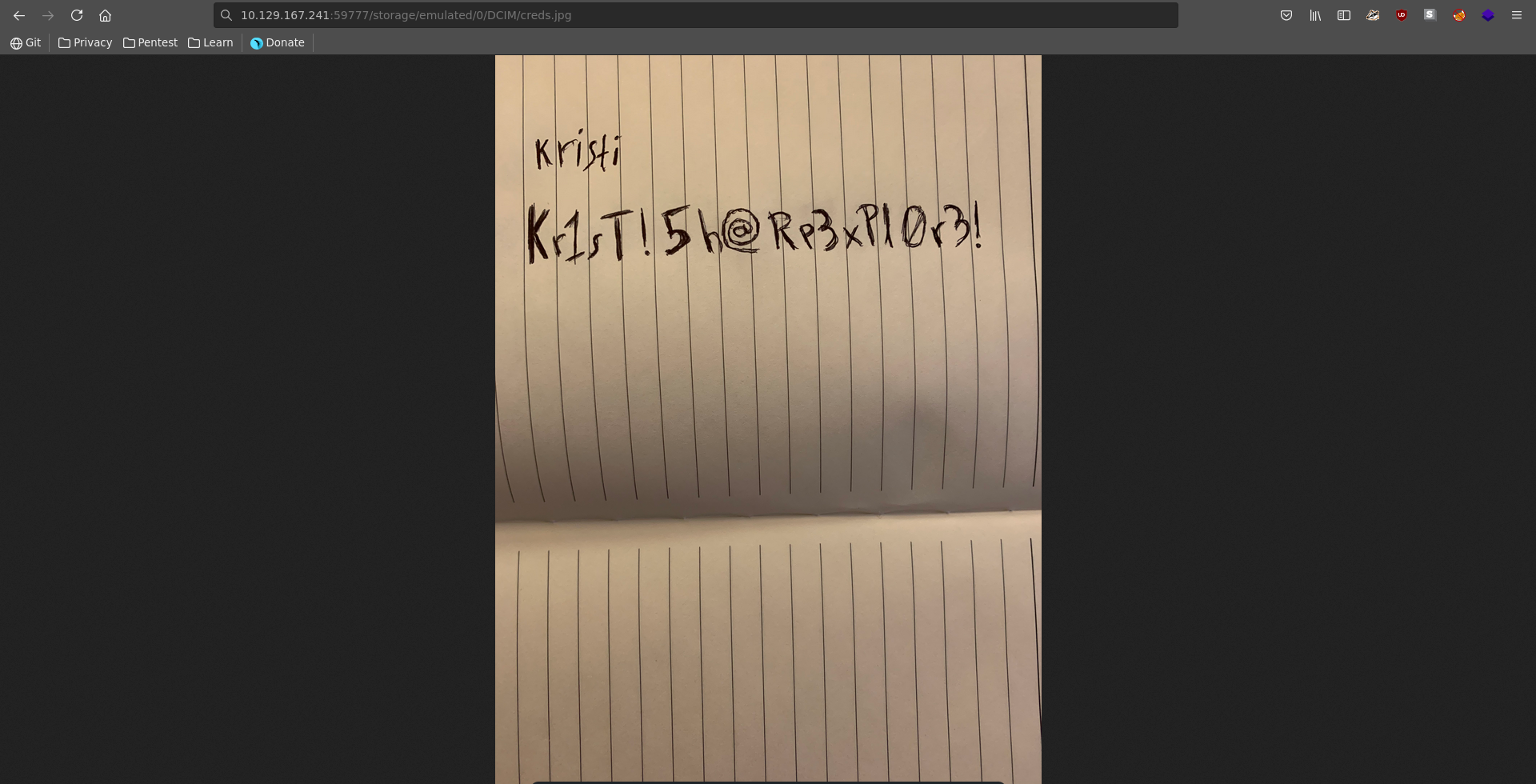
The running installation is vulnerable to CVE-2019-6447, which let’s us read files from the device or start an app. Looking through the images on the device we find an interesting looking creds.jpg file.
1 | |
The image shows a note with the password for the user katie. Trying it on the open ssh port with the credentials kristi:Kr1sT!5h@Rp3xPl0r3! we get access to the device.
1 | |
Looking around in the storage folder which also had the image in it we find the user flag.
1 | |
Root
We earlier saw that port 5555 showed up in our nmap scan. This is most likely the Android Debug Bridge being enabled on the device.
“The adb command facilitates a variety of device actions, such as installing and debugging apps, and it provides access to a Unix shell that you can use to run a variety of commands on a device.” — Android’s developer portal
Being able to communicate with it would most likely give us unauthenticated root access to the device. Checking it again we can see it is listening on all interfaces but seems to be filtered for us.
1 | |
We can however access it if we forward the port to our machine with ssh. For this we open the ssh console in our connection by entering ~C on a new line and issue the local port forward.
1 | |
After installing adb on our machine with apt install adb we kill the adb server, in case it was already running, so it restarts on the next command.
1 | |
We then list all devices to be able to connect to our target with its device name in the next step.
1 | |
Now we can simply connect to the debugging bridge as the root user and drop into a root shell with adb shell.
1 | |
1 | |
Being the root user we can now add the flag to our collection
1 | |