User
Tentacle is a hard rated machine on HackTheBox created by polarbearer. In this walkthrough we will first discover a vulnerable OpenSMTP installation hidden behind multiple proxies and exploit it to get root on the SMTP server. Armed with some credentials we will log into the machine using kerberos over ssh. The privilege escalation is all about kerberos, where we first place a k5login file in the admin user’s home directory, abuse a running cronjob and in the final step add a principal to the krb5.keytab file to switch to the root user with ksu.
Nmap
As always we start our enumeration off with a nmap scan against all ports, followed by a script and version detection scan against the open ones to get a full picture of the attack surface.
All ports scan
1 | |
Script and version scan
1 | |
Chaining Proxies
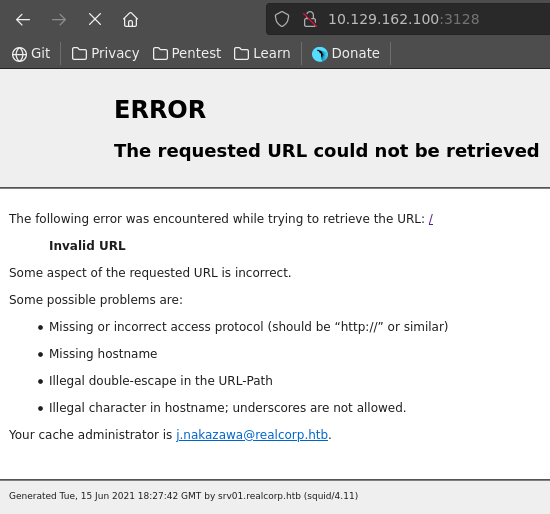
Opening port 3128 in our webbrowser we see the default error page of squid proxy. This reveals a domain name and the potential username for the administrator.
Using impackets GetNPUsers on the the discovered user and domain, we see that preauthentication is not required and retrieve a TGT for j.nakazawa. This hash does however not easily crack and seems to be a rabbit hole.
1 | |
Using dnsenum we can identify 3 subdomains in the network which are on a different subnet. We can’t reach this subnet right now but we might be able to reach it through squid, so we’ll go there next.
1 | |
To do this we first have to add the ip address of the squid proxy to our proxychains configuration. We also select strict chain. Uncommenting quiet mode makes the output more readable. Also lowering the tcp_read_time_out and tcp_connect_time_out lowers the scan-time. (Here it is important to find a good measurment else the results will be skewed)
/etc/proxychains.conf
1 | |
We run the scan through proxychains on localhost of the target which reveals 2 new open ports and continue our pivot to the other subnet.
1 | |
First we also add the squid proxy on localhost of the machine to our chain.
1 | |
Then we run another scan against the earlier discovered host with our new configuration.
1 | |
This reveals yet another squid proxy which we also add to our proxychains.conf which should now look like this.
/etc/proxychains.conf
1 | |
Running another scan, this time on the ip discovered by dnsenum for wpad.realcorp.htb through our chain, we find a running webserver on port 80.
1 | |
Just issuing a curl request to the ip returns a nginx default page, but trying to reach the site with curl on it’s FQDN which we add to our /etc/hosts file, we get a 403 Forbidden instead.
1 | |
Wpad most likely stands for Web Proxy Auto-Discovery (WPAD), which means there should be a wpad.dat file present in the server root.
Issuing another curl request on the server we can indeed retrieve the config file and discover another subnet 10.241.251.0/24.
1 | |
Running a scan against the 10.241.251.0/24 subnet we see that port 25 is open on
10.241.251.113. This scan may take some time to complete because of proxychains usage.
1 | |
OpenSMTP
Connecting to the port we see that it is OpenSMTP. Looking around for public exploits on OpenSMTP, we find this promising looking PoC for CVE-2020-7247. We use it with a different payload to gain remote code execution and a reverse shell on the SMTP server.
First we stand up our listener on the port we want to recieve the shell.
1 | |
We then send the PoC from qualys using the earlier found email address for the administrator. This works by bypassing the whitelist in the smtp_mailaddr() function. If the local name of the mail address is invalid and the domain part empty at the same time , we can bascially pass commands to the mda_unpriv() function with fewer restrictions. Some characters are however still blocked and there is a length restriction.
To also bypass this restrictions, we use a loop to strip the 14 header lines, prepended by the server, via a call of read. The body then get’s passed over to sh and we achieve RCE and in this case a reverse shell.
1 | |
Almost instantly after sending the last ., we recieve a reverse shell as root on the SMTP server. Before we continue our flag hunt we upgrade the shell and fix the terminal size.
1 | |
SSH with Kerberos
In the mail-client configuration in j.nakazawa’s home directory we find some credentials, which unfortunately don’t work with ssh.
1 | |
Since kerberos is also enabled on the machine we try to use it to authenticate over ssh next by creating a ticket using the password and the username.
First we install krb5-user.
1 | |
Then we update our krb5.conf to contain the correct realm and kdc address.
/etc/krb5.conf
1 | |
We also make sure our /etc/hosts contains this entry for our target ip.
1 | |
Now we can create the ticket using the password sJB}RM>6Z~64_, confirm everything went well, log into the machine as j.nakazawa and grab the user flag.
1 | |
Root
Crontab and .k5login
Enumerating basic things on the machine, we find a cronjob for the admin user, which executes a log_backup.sh script.
1 | |
What the script basically does is copy the contents of the /var/log/squid/ directory to /home/admin.
log_backup.sh
1 | |
Since kerberos authentication for ssh is enabled on this machine, this means we can drop a .k5login in the /var/log/squid/ directory, it get’s copied to admin’s home folder and we can ssh into the machine as him.
1 | |
After some time we can log in as the admin user from our local machine. This might not work the first time, but should work tried repeatedly.
1 | |
Keytab to root
Looking around we find the /etc/krb5.keytab file, that is owned by the admin group, which means we can modify it.
1 | |
1 | |
The keytab file contains the principles and encrypted keys for users which can access the machine. This means we can escalate to any user user by adding a keytab entry for him with a password of our choice. We do this for the root user, using the kadmin functionality choosing a password of our liking.
1 | |
Finally we use ksu to switch to our newly created principle with our chosen password and are able to read the flag as the root user.
1 | |